Hello Josh
I appreciate your encouragement! It’s responses like these that really make all of this worth it. We’re here to help and we’re doing our best, and thanks so much for your kind words!
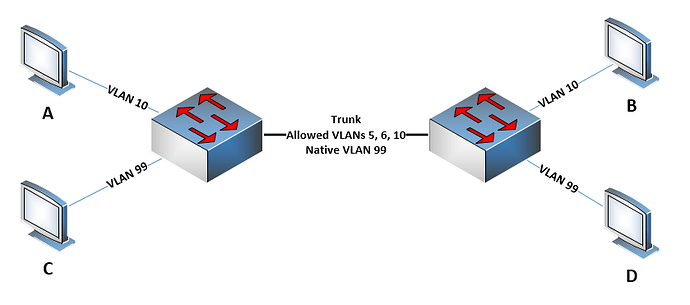
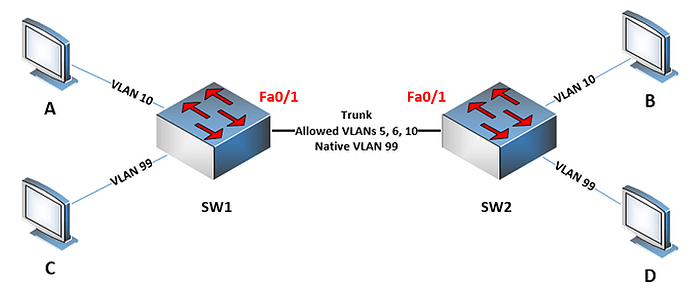
Actually, what the native VLAN command does is it states that “if an untagged frame is received on a trunk port, in which VLAN should it be placed?” This does not mean that any traffic on the native VLAN will be sent over the trunk port without a tag. Take a look at the following topology:
Here we have a trunk that carries VLANs 5 6 and 10 and has a native VLAN of 99. Hosts A and B will be able to communicate, but hosts C and D will not. This is because only traffic on VLANs 5 6 and 10 will be
sent out of the corresponding trunk ports and not VLAN 99 traffic. The native VLAN traffic will never be sent out of a trunk port. It only tells the trunk port what to do with incoming untagged frames.
In order for C and D to communicate, you must allow VLAN 99 on the trunk, and if you do so, their communication will take place using untagged frames.
The above description has to do with data plane traffic. Control plane traffic on the other hand will use the native VLAN across trunks by sending untagged frames from trunk ports. But this is limited only to control plane traffic. (I actually labbed this up to confirm).
Now applying this to REP, note that LSL frames are dealt with as control traffic, and those frames do indeed operate over the native VLAN. HFL frames on the other hand, that travel over the administrative VLAN, are considered data traffic and are dealt with in the same way as any traffic that goes from host to host.
Now the document states that it makes sense to assign the administrative VLAN as the native VLAN as well. This is perfectly fine, since any LSL traffic will be sent as untagged traffic across the trunks, and HFL traffic will be sent as tagged frames across the trunk. The tagged frames will be placed on the Administrative VLAN, while the untagged frames will be placed on the native VLAN. And in such a case case, both of these VLANs are the same.
So to answer your question:
…yes that is correct. 
I hope this has been helpful!
Laz