Hello, I checked the new CCNA 200-301 exam topics and i could not find AAA configuration in it. The only section in the exam topics that talks about is: 2.8 Describe AP and WLC management access connections (Telnet, SSH, HTTP, HTTPS,
console, and TACACS+/RADIUS)
I want to know if I should still learn AAA configuration for 200-301 exam?
Hello Kevin
Based on the exam topics as described by Cisco, there is no indication that you need to know any details about AAA configuration beyond simply that TACACS+ and RADIUS are used for this purpose. However, Cisco always states the following before the list of exam topics:
The following topics are general guidelines for the content likely to be included on the exam. However, other related topics may also appear on any specific delivery of the exam.
So this essentially gives them the ability to throw in some additional related topics, so you can never be absolutely sure. Having said that, I believe that you will be OK without studying any specifics about AAA configuration, as it is highly unlikely to be found on the exam.
I hope this has been helpful!
Laz
Hello Laz,
Your answer was very useful, Thank you very much, so i would look into AAA configuration only if I had extra time after preparing for necessary topics.
Regards,
kevin
Hi Rene and Team,
A little explanation would be helpful for my case below.
On the switch I have AAA group server tacacs + configured with two ISE servers. AAA works well on the primary ISE but when I test failover to secondary by denying flow from switch to primary server the AAA on the secondary server is becoming a bit unresponsive when I try to log to the device or type commands. To be precise it waits for 5-6 sec.
I found explanation that the switch is always asking the first server from the group and if no response is received it will check the next one.
Do you perhaps know what is the default timeout in this case, hence for how long exactly it waits for primary ISE to respond and could I resolve this issue with adding for example “timeout 2 sec” next to the primary server command?
Thank you in advance.
Best regards,
Hello Milan
When configuring a backup TACACS server within an AAA group, the behaviour is just as you described. The first server is checked first, and if that times out, it will then reach out to the second server. This can result in a delay every time you want to log in.
Server groups that contain more than one host entry are tried in the order they are configured. For each server configured, there is a timer that can be adjusted before an error is detected, but by default, that timer is set to 1 second, which is the minimum setting so you probably won’t find a solution to your issue there. More about how these backups can be configured can be found here:
There is however another parameter called single-connection which is used to maintain a single open connection between the router and the daemon. This eliminates the need to re-establish a TCP connection to the server (which can take several seconds for each attempt to both primary and backup servers) once it is established. This is a parameter that is configured within the tacacs-server command and more information about it can be found here:
Now I am not sure what effect this has on the operation of the backup. Does it maintain an open connection to the backup and have all subsequent communications take place with the backup, or does it still attempt to connect to the primary server first? I was unable to find any information on this. You can do some experimentation with this to see if it results in any speeding up of the failover process, and let us know your results.
I hope this has been helpful!
Laz
Hi
I would like to know if it possible to use this command in a vrf
test aaa group radius REMOTE_ADMIN MY_PASSWORD new-code
I explain i have a vrf managment for exemple and i would like to try to join the radius
is it possible ?
thanks
Hello Veronese
This command is not associated directly with any VRFs, and thus can be applied in a device that has multiple VRFs. The command is applied in privileged executive mode. As long as you have access from the device to the server, there should be no other restrictions. You can find out more about it here:
If I have not understood your question correctly, please clarify so that we can respond more appropriately.
I hope this has been helpful!
Laz
Hello Laz,
Thank you for your time and explanation.
This was definitely a big help.
I will test it and let you know.
Best regards,
Hi Rene and staff,
usually i do SSH on CSR1000v in GNS3 labs with username/PWD in the local database of each router (aaa new-model is OFF by default)
Recently, i tried to activate aaa new-model in one of the router, to work with local database of this router.
So i create a list, lines vty authentication use this list, and this list points to the local database of the router
That was a test: i wanted to compare log details with and without aaa model, to monitor ssh
With debug aaa authentication i could see some details on the console
But even with severity 7 nothing came into the cisco logs. Show logging (with config set to login buffered 7) is empty when i do a SSH connection
So this my question: do aaa events go to Cisco logging system ?
Regards
Hello Dominique
According to this Cisco documentation, the debug aaa authentication command states that it displays “information on authentication, authorization, and accounting (AAA) TACACS+ authentication”. Looking further, it seems to indicate that it indicates RADIUS and TACACS+ client server interaction. In the case where you are using the local user database, no events will be logged.
If you want to log events of logging in and logging out of SSH or Telnet sessions, you could take a look at the following Cisco Community thread which includes some information…
I hope this has been helpful!
Laz
Hello;
I just have a question. Someone can tell what does the follow command means:
show auth session interface fa1/018
Thanks in advance for your feedback
Hello Daoud
The Cisco Auth manager in an IOS device handles all network authentication requests and enforces authorization policies of all types. It maintains operational data for all port-based network connection attempts, authentication, authorizations, and disconnections.
The show authentication sessions command is used to display information about all current auth manager sessions. If you use the interface keyword, then you are filtering the results and showing only the session information for that particular interface.
You can find out more about this command at the following Cisco command reference:
You can also find out more about the Cisco IOS Auth Manager on page 6 of the following document:
I hope this has been helpful!
Laz
Hi Team,
I am seeing the following message when I test the credentials of freeradius server on Router R1.
R1#test aaa group radius REMOTE_ADMIN MY_PASSWORD new-code
User rejected
R1#
*Jan 21 08:31:28.833: %RADIUS-3-ALLDEADSERVER: Group radius: No active radius servers found. Id 97.
Appreciate your suggestion and resolution.
Raghunath
Hi Community !
I have installed freeradius on Ubuntu Server 18.04.3 LTS (64bit) on my gns3 appliance ; when i am running
R1# test aaa group radius REMOTE_ADMIN MY_PASSWORD new-code
I am seeing the following messages is FAILING the user authentication. please explain and advise resolution. my router address 192.168.122.1 and RADIUS SERVER add 192.168.122.118
root@gns3 freeradius -X
.
.
Listening on auth address * port 1812 bound to server default
Listening on acct address * port 1813 bound to server default
Listening on auth address :: port 1812 bound to server default
Listening on acct address :: port 1813 bound to server default
Listening on auth address 127.0.0.1 port 18120 bound to server inner-tunnel
Listening on proxy address * port 44405
Listening on proxy address :: port 49912
Ready to process requests
Ignoring request to auth address * port 1812 bound to server default from unknown client 192.168.122.1 port 1645 proto udp
Ready to process requests
Ignoring request to auth address * port 1812 bound to server default from unknown client 192.168.122.1 port 1645 proto udp
Ready to process requests
Ignoring request to auth address * port 1812 bound to server default from unknown client 192.168.122.1 port 1645 proto udp
Ready to process requests
Ignoring request to auth address * port 1812 bound to server default from unknown client 192.168.122.1 port 1645 proto udp
Ready to process requests
regards
Raghunath
Hello Raghu
I’m no RADIUS guru, but I believe the issue has to do with the phrase “unknown client 192.168.122.1”. It seems that for some reason, the client information is not correctly included within the clients.conf file in the RADIUS server. Take a look at that, and make sure that the IP address is correct, as well as the credentials, as shown in the lesson.
Check that out and let us know how you get along.
I hope this has been helpful!
Laz
Hi Lazaros ,
I am not successful in installing freeradius on Ubuntu in GNS3 ; however I have used GNS3 AAA docker container a customized freeradius - with two users alice and bob with password “gns3” and is successfully authenticated:
R1# test aaa group radius alice gns3 ?
legacy Code path through legacy
new-code Code path through new-code
port Port send as part of request
R1# test aaa group radius alice gns3 new
R1# test aaa group radius alice gns3 new-code
User successfully authenticated
USER ATTRIBUTES
reply-message 0 "Hello, alice"
R1#
R1# test aaa group radius bob gns3 new-code
User successfully authenticated
USER ATTRIBUTES
reply-message 0 "Hello, bob"
R1#
Hello Raghu
Hmm, I’m not quite sure what is happening there. There are many reasons for which this particular error appears, and most have to do with some setting on the RADIUS server that
Here are a couple of instances that others have faced that may help to guide you in the right direction:
https://askubuntu.com/questions/708663/radius-is-ignoring-request-to-authentication-address
https://www.reddit.com/r/networking/comments/c8ibkq/freeradius_server_issues/
In any case, I’ll let @ReneMolenaar know about it as well and see what suggestions he may have.
I wish I could have been more helpful!
Laz
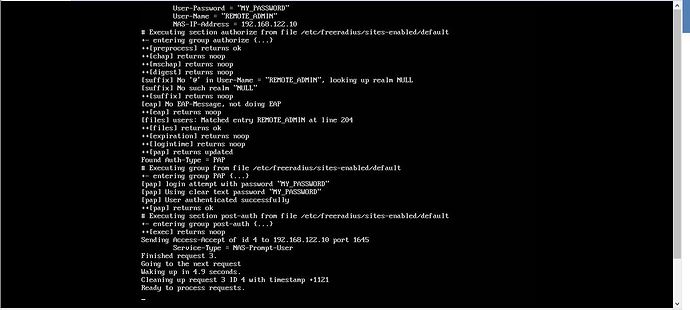
Hi Lazaros,
I have re-installed freeradius on Ubuntu 18.0.4 desktop VM on vmware workstation ( instead of GNS3 appliance) and it is working as demonstrated in the video.
R1#test aaa group radius REMOTE_ADMIN MY_PASSWORD new
R1#test aaa group radius REMOTE_ADMIN MY_PASSWORD new-code
User successfully authenticated
USER ATTRIBUTES
service-type 0 7 [NAS Prompt]
R1#
Hello Raghu
Perfect! Great to hear that it worked out! Thanks for keeping us updated…
Laz
Hi Lazaros,
I would like to suggest, if possible, to include in the ENARSI /ENCOR curriculum , a demo video or a procedure for basic configuration and installation of software (like freeradius, graylog-server, python, netmiko, ansible etc.) into Linux /Ubuntu docker containers or VMs interfacing with Cisco devices. This is time-consuming and involves lot of troubleshooting. Ignore my request if already provided in other sections.