Hello Laz,
I just had a few questions about the contents of this lesson, as well as a some questions regarding the use of a Radius/TACACS server for authorization:
- For the 3 default privilege levels (Level 0, 1, and 15) I understand that there are a range of commands that are accessible to users depending on which of those levels their credentials fall under, but my question is arent those levels also associated with what mode that user is dropped into once they successfully log into the Router/switch? For example, if I configure:
username admin privilege 15 password cisco
username tech password cisco123
username reader privilege 0 password cisco12345
then anytime “admin” logs into the router/switch via the console port or VTY lines then we would end up in privileged exec mode (Hostname #), regardless if we have an enable password configured to get from user exec to privileged exec correct?
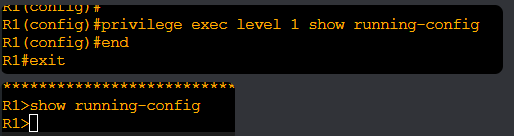
On the other hand, “tech” would end up in user exec mode (Hostname >) since it has privilege level of 1, and “reader” would end up in user exec mode as well, except only 5 commands would be available, such as “enable”, since this user has privilege level 0. Both of these users would have to input the enable password in order to go into privileged exec mode. Is my understanding here correct? Please assume the only authentication that is configured in the Router/switch in this scenario is “login local” under the VTY lines and the console port.
- My next question involves applying privilege levels directly to the console port/ VTY lines so that upon successful authentication all users can go straight into privileged exec mode (hostname #). If my understanding from the previous question is correct, then user admin would go straight into privileged exec mode due to its privilege level 15 after it authenticates with the router regardless of whether we are using the console port or the VTY lines for SSH/Telnet. But what if we wanted the same for user “tech” who has a privilege of 1? Couldnt we apply the “privilege level 15” command directly on the VTY lines and Console port to achieve this?
Some additional questions regarding authorization with the use of a radius/tacacs server:
Assume we had a router with the following AAA config to authenticate/authorize:
aaa new-model
radius server EXAMPLE1
address ipv4 10.1.1.1 auth-port 1812 acct-port 1813
key cisco123
radius server EXAMPLE2
address ipv4 10.1.1.2 auth-port 1812 acct-port 1813
key cisco123
aaa group server radius TEST
server name EXAMPLE1
server name EXAMPLE2
aaa authentication login default group TEST local
aaa authorization exec default group TEST if-authenticated
My first question revolves around authorization for the exec shell. I understand this is supposed to determine if users are authorized to start an “exec” shell according to cisco. In my example above, this is checked by first checking with the TEST group, then relying on if the user was successfully authenticated to determine if the user is allowed to start an exec shell, but what exactly is meant by “exec shell” here, is it just the CLI? and does that mean that the CLI wont even start if a user fails authorization?
My last question involves the use of the aaa authorization commands command. If we were to use “aaa authorization commands 15 default group TEST local none” I understand it would authorize by checking with the TEST group and then relying on local command authorization if that fails, and then not doing any authorization at all if the first two methods fail, but I dont understand how this works. Are we only allowing commands associated with privilege 15 to be used if they are authorized? I know Radius cannot do command authorization so lets pretend were using tacacs just for this last question.
Thank You
Laz