Thanks Dear.Many Thanks
Can we create a group policy only for a specific set of users? For example, if we want that a certain group of users should only access certain set of servers.
Hi Amit,
Yes you can, you’ll need to create an additional policy group and tunnel group for this. Here’s a quick example:
group-policy VIRL_VPN internal
group-policy VIRL_VPN attributes
vpn-filter value VIRL
split-tunnel-policy tunnelspecified
split-tunnel-network-list value VIRL_SPLIT_TUNNEL
access-list VIRL_SPLIT_TUNNEL standard permit 192.168.1.0 255.255.255.0
access-list VIRL extended permit tcp any object VIRL object-group VIRL_PORTS
access-list VIRL extended permit tcp any object VIRL2 object-group VIRL_PORTS
tunnel-group VIRL_TUNNEL type remote-access
tunnel-group VIRL_TUNNEL general-attributes
address-pool VIRL_VPN_USERS
default-group-policy VIRL_VPN
tunnel-group VIRL_TUNNEL ipsec-attributes
ikev1 pre-shared-key *****
The group policy called “VIRL_VPN” uses an access-list called VIRL to define what resources the remote user can access. It also uses split tunneling, this VPN is only used to reach the networks in access-list VIRL_SPLIT_TUNNEL.
In the tunnel-group, you can see we refer to the VIRL_VPN group-policy.
Hope this helps!
Rene
I have added the below command but am able to connect successfully but I cant access LAN device either through ping, tracert, telnet, ssh etc.
ASA1(config)# object network LAN
ASA1(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA1(config)# object network VPN_POOL
ASA1(config-network-object)# subnet 192.168.10.0 255.255.255.0
I wasn’t able to configure the below command since am running an 8.2 version. What am I missing?
ASA1(config)# nat (INSIDE,OUTSIDE) source static LAN LAN destination static VPN_POOL VPN_POOL
Hi Muhammed,
That NAT rule is an important one. It tells the ASA not to translate traffic between 192.168.1.0 and 192.168.10.0. If you don’t have it then traffic from 192.168.1.0 to 192.168.10.0 will be translated which is probably why you don’t have any connectivity.
For ASA versions before 8.3, you can try this:
ASA1(config)# access-list NO_NAT extended permit ip 192.168.1.0 255.255.255.0 192.168.10.0 255.255.255.0
ASA1(config)# nat (inside) 0 access-list NONAT
ASA 8.2 has been EOL since April 2014 so it’s not a bad idea to upgrade ![]()
Rene
Rene,
IPsec Tunnel always speak of New IP Header being applied to the original header when an example is given. Can you give a real world example that shows the newly created Ip addresses in the header and the original ip addresses? I am trying to see how packets are routed from the client with a remote vpn client installed.
Thanks
Hi Edwin,
For such request, you can post your idea in the following URL “Member Ideas” on our website where your idea can be voted so Rene can pick it up and make a new lesson from it.
Thanks for following our lessons.
Hi,
I need to create to remote access VPN but my outside interface have private adddress with ISP conecction.
My DMZ have public address.
Can do I make to VPN remote access in my ASA 5520 with NAT to one public address ??
best regars
Hi Rene,
Can do I make a VPN if my outside interface have private address IP, but I have public IP address for my DMZ interface ?
Hi Rene,
I have private ip address in the outside interface connected the ISP, and DMZ interface have public IP for diferent service. then the question is:
Can do I use a IP public address from my pool of DMZ for get up my VPN remote access?
how do I make this ?
best regards
Hi Gabriel,
It is possible. Most devices, including the ASA firewall, support NAT traversal for IPsec.
Is your public IP addresses NATed 1-to-1 to the private IP address that your ASA uses? If so, give it a shot.
Rene
19 posts were merged into an existing topic: Cisco ASA Remote Access VPN
HI
When the tunnel is brought up on the ASA does it create a logical tunnel interface and assign it an ip address from the vpn pool?
what show commands could i use to see this interface on the asa ?
Thanks
Hi @sclarke1210,
You won’t see a tunnel interface directly. If you want to verify that a user has connected and see the IP address that was assigned from the VPN pool, it’s best to use these two commands:
ASA# show crypto ikev1 sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
2 IKE Peer: 62.44.197.140
Type : user Role : responder
Rekey : no State : AM_ACTIVE
Above you can see that a user has connected. The IP addresses you can see below:
ASA# show crypto ipsec sa user renemolenaar
username: renemolenaar
Crypto map tag: RMCS_VPN, seq num: 10, local addr: 1.2.3.4
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (192.168.1.100/255.255.255.255/0/0)
current_peer: 62.44.197.140, username: renemolenaar
dynamic allocated peer ip: 192.168.1.100
dynamic allocated peer ip(ipv6): 0.0.0.0
#pkts encaps: 67, #pkts encrypt: 67, #pkts digest: 67
#pkts decaps: 75, #pkts decrypt: 75, #pkts verify: 75
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 67, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 1.2.3.4/4500, remote crypto endpt.: 62.44.197.140/6967
path mtu 1500, ipsec overhead 82(52), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 029C51AC
current inbound spi : 323F5F7F
inbound esp sas:
spi: 0x323F5F7F (843014015)
transform: esp-aes esp-sha-hmac no compression
in use settings ={RA, Tunnel, NAT-T-Encaps, IKEv1, }
slot: 0, conn_id: 4460544, crypto-map: RMCS_VPN
sa timing: remaining key lifetime (sec): 28722
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x029C51AC (43798956)
transform: esp-aes esp-sha-hmac no compression
in use settings ={RA, Tunnel, NAT-T-Encaps, IKEv1, }
slot: 0, conn_id: 4460544, crypto-map: RMCS_VPN
sa timing: remaining key lifetime (sec): 28722
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Above you can see the dynamic allocated peer ip, which is the IP address from the VPN pool.
Rene
A post was merged into an existing topic: Cisco ASA Anyconnect Remote Access VPN
Hi Rene,
Hope you are doing well and safe.
Did you make any guide with IKEv2 with VPN client (NOT Anyconnect)
Please let me know
Thanks
Regards
Zeeshan
Hello Zeeshan
There is no lesson that specifically includes the use of IKEv2 with VPN hosts as clients without using Anyconnect. The specific configuration would depend on the specific VPN client that you are using on the host end. You can find some examples of IKEv2 VPNs with use with Windows or Android VPN clients on a Cisco ASA device at the following links:
For more specific VPN client configurations, it is best to use your favourite search engine to find configs for your particular clients.
I hope this has been helpful!
Laz
Hi Rene,
Why does it set twice in the next statement the words LAN LAN and VPN_POOL VPN_POOL?
ASA1(config)# nat (INSIDE,OUTSIDE) source static **LAN LAN** destination static **VPN_POOL VPN_POOL**
Hello Alberto
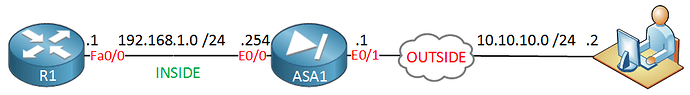
This is actually correct. This is what is called “Twice NAT” or “Identity NAT”. Take a look at the image of the network:
The ASA has NATing enabled, so any traffic going from INSIDE to OUTSIDE, or visa versa, will be NATed.
The VPN client on the OUTSIDE network is on the 10.10.10.0/24 subnet. When it connects via VPN, its connection is tunneled over this subnet, and the internal IP address it is provided is in the 192.168.10.0/24 subnet, which is configured in the VPN_POOL.
So the client sends encapsulated data to R1 over the tunnel. Outside IP header 10.10.10.0/24 subnet, inside IP header 192.168.10.0/24 subnet. Once it reaches the ASA outside interface, it is first decapsulated, so the 10.10.10.0/24 IP address is removed.
The result is an IP packet with a source and destination IP in the 192.168.10.0/24 subnet, and the packet is going in the OUTSIDE interface and exiting the INSIDE interface. Under normal circumstances, this traffic would be NATed. But we don’t want that, because the addresses are already the inside addresses we want. So we use this commands:
ASA1(config)# object network LAN
ASA1(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA1(config)# object network VPN_POOL
ASA1(config-network-object)# subnet 192.168.10.0 255.255.255.0
ASA1(config)# nat (INSIDE,OUTSIDE) source static LAN LAN destination static VPN_POOL VPN_POOL
These commands simply state that any traffic that traverses the ASA with these IP addresses should not be translated. It essentially says: translate 192.168.1.0/24 to 192.168.1.0/24 and 192.168.10.0/24 to 192.168.10.0/24. This is why LAN and VPN_POOL are stated twice in the comand.
I hope this has been helpful!
Laz
Hi,
I can connect the vpn , but I can’t reach the any of the network .
What could be the issue .How to trouble shoot
Thanks