Okay I think this has caused another issue though because if I move my web servers to VLAN 28 and change everything to reflect to make the DMZ 28 for the ip scheme. I now still have a default route pushing all traffic to the inside interface from the router to the ASA. If I try to modify this route to network specific route to the 10.15.1.2 ASA inside interface then no traffic is passed out to the internet and everything stops working so the traffic on VLAN 28 is still not pushing over the DMZ with this configuration??
Hello Brandon
What’s important to note here is that any servers you want to be treated with the security that the DMZ provides must be connected to the DMZ port. If you want multiple subnets/VLANs to be treated as DMZ, then you need another router connected to the DMZ port behind which you can place as many subnets/VLANs as you like.
In order to help you more effectively, can you share your current topology, VLANs, and IP address ranges with us so that we can help troubleshoot your issues more specifically?
I hope this has been helpful!
Laz
Laz,
I’m using the exact topology you have helped me design with a few small tweaks to the DMZ recently changed from Vlan 30 to 28 to prevent from so many other changes across the rest of my devices.
So I have another router ready to add to this scenario to my lab equipment but I don’t know where your saying to implement it or how exactly with everything else. So I have Vlans 10, 20 routing to the inside interface and NaT is working wonderful with this config. I currently have Vlan 28 on same switch and the sub int setup on the previous router but I understand the problem but I don’t could I use the 2nd interface on the router or does it need to be a completely different one? If a completely different one then is it plugged into the switch and has only Vlan 28 configured and the default route to the DMZ interface which is currently
10.10.100.10/24
Router is 10.10.100.1/24
Web server 1 is 10.10.100.118
SFTP / VPN is 10.10.100.115
These are the two servers I need to figure out how to configure the routes, ACLS, to allow traffic from public to the inside ? Also I don’t know if it makes it easier if I add in I have a 2nd ASA available and additional public static IPS to use.
Vlan 28 10.10.100.0/24
Vlan 10 10.10.1.0/27
Vlan 20 10.20.1.0/27
Vlan 12 10.12.1.0/26 not in use yet but plan to use for wifi
Hello Brandon
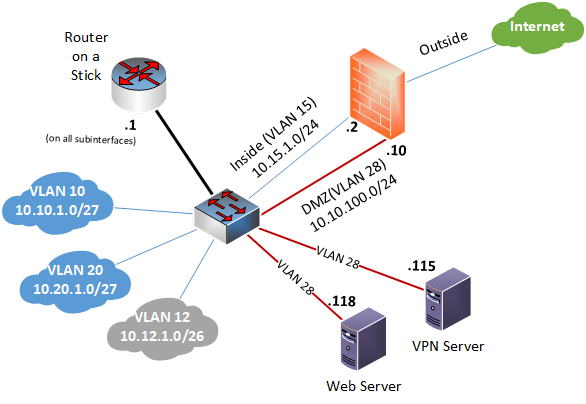
Let me clarify a couple of things. I had suggested to install another router to connect to the DMZ interface only as a solution to placing two or more VLANs behind the DMZ (just like you have multiple VLANs behind the Inside interface). Since this is not the case, and the web and VPN servers are in the same VLAN (28) then we don’t need that. Based on your description, this is the topology I have come up with:
Now on the Router on a stick, you would have a default route to 10.15.1.2 since everything (Internet, DMZ, the rest of the world) is accessible only via the inside interface of the ASA. Here you can specify something more specific, like the IP addresses of the servers, but it will actually make no difference in the functionality of the network.
Secondly, you would have the web and VPN servers hanging off of the DMZ interface. Now in order for the ASA to route traffic appropriately, you will have to do the following:
route 10.10.1.0/27 via 10.15.1.1
route 10.20.1.0/27 via 10.15.1.1
route 10.12.1.0/27 via 10.15.1.1
route 0.0.0.0 via Internet next hop IP
The rest of the networks including 10.15.10.0/24 and 10.10.100.0/24 are directly connected, so no additional routing is necessary. You must verify that the servers are using 10.10.100.10 (the DMZ interface) as their default gateway.
Finally, in order to get the servers accessible from the public to the DMZ, you can either employ Static NAT or NAT port forwarding. These two lessons describe these features in detail:
You can use a second ASA in the event that you want to introduce redundancy in an active/standby failover situation. You can find out more about this here:
I hope this has been helpful!
Laz
I am having an issue with my ASA, in which my VLANs are not passing along from my 3750X Switch stack onto my 5525X ASA. I attempted to configure my switch port to be trunked while allowing all VLANs to traverse then set my physical ASA port to be a subinterface with the corresponding VLAN IPs, but when I pinged from the ASA/Switch I could not reach either interface.
Hello Cory
From your description, you seem to have followed the correct procedure. It’s most likely a small configuration detail that you will have to troubleshoot and work out. One thing you should keep in mind when configuring this, is that unlike router on a stick, the physical interface of the ASA must have no security zone configured, while a security zone must be configured on each of the subinterfaces. This is a common misconfiguration in such implementations, so I thought I’d mention it here.
You can take a look at this lesson which details such a configuration and compare it with yours. This may help you in your troubleshooting procedures.
I hope this has been helpful!
Laz
I see there are articles on how to configure Intervlan routing using a L3 Switch or Router, also articles about using the ASA to do subinterfaces… Is it possible to combine them both and would the best way of going about this is to use ACLs on the ASA?
Imagine a small branch site with say only four VLANs, these endpoints connect into a L2 switch, with the switch connected to the ASA on a single physical interface/port. If the ASA can be configured to support five subinterfaces, and the appropriate ACLs configured for each of these corresponding five VLANs, would it effectively be like using the ACL as a router to handle the intervlan stuff that the L2 switch cannot do? In this case the ASA itself connects to the outside to a SD-WAN endpoint and therefore cannot be another router in between them.
Hello Bo
What you are describing is using the ASA as the router between VLANs on an L2 switch. This is exactly what is being described in this lesson:
What I am not clear about is what you mean when you say:
ACLs are simply filtering mechanisms that will either allow or deny packets of specific source or destination addresses or ports. ACLs don’t route traffic. The ASA itself routes traffic. So in the scenario you are describing, it is the ASA that is routing between the VLANs, something that the L2 switch cannot do. Does that make sense?
I hope this has been helpful!
Laz
Hello,
In this lesson, we use VLANs for DMZ.
But we can use VLANs with differents security level for a LAN ?
For example, in my LAN I have 2 VLANs : VLAN 10 Marketing et VLAN 20 HR.
Can I use security-level 70 for VLAN 10 et security-level 80 for VLAN 20 ?
So, VLAN 20 can communicate with VLAN 10 but not VLAN 10 with VLAN 20 in my opinion.
Am I right ?
Thanks
Hello Anas
To answer your question, yes it is possible to create a different type of “zone” for each subinterface you create. So you could theoretically have an INSIDE, OUTSIDE, and DMZ subinterface all on the same physical interface.
But you must remember that the definition of INSIDE, OUTSIDE, and DMZ are not fixed. That is, an ASA is not confined to creating only three zones with these specific names. These are just names used to refer to the zones of the most common topology that is created using an ASA. But you are free to define even more zones if you like, and call them whatever you like.
The zones are defined using the security level. An ASA can have up to 100 security levels, so for example, you can have five interfaces or sub-interfaces, and have different security levels for each. In such a case, which would you consider the DMZ? It is no longer clearly defined.
In the lesson, we see that one subinterface is provided with a security level of 70 and the other 80. Even though they are called INSIDE1 and INSIDE2, the first with a security level of 70 is effectively the DMZ, if we look at the most commonly configured topologies with three zones. This is because it has the “middle” security level, and would thus function as a traditional DMZ.
I hope this has been helpful!
Laz
Hi Rene
How the Routing Traffic between VLANS 10 and 20 is possible without setting up the Routing on the ASA ?
Also if we want to STOP connectivity between VLANs for security reasons on the ASA what should be done ? No Route Entries - Just thinking Loud ???
Hi Rene,
For the security level on the level, what was the reason behind assigning them 70 and 80 instead of 100 for both..
Hi Rene
How the Routing Traffic between VLANS 10 and 20 is possible without setting up the Routing on the ASA ?
Also if we want to STOP connectivity between VLANs for security reasons on the ASA what should be done ? No Route Entries ? ACL ? - Just thinking Loud ???
Hello Surendra
Whenever you configure two or more SVIs (or physical interfaces) on an ASA, routing between those interfaces is automatically enabled. You don’t have to actually configure it. The same goes for L3 switches and routers. InterVLAN routing and routing between active interfaces is enabled by default.
In an ASA, in order to stop connectivity between VLANs, you can either configure the security level appropriately, or you can apply an access list that will block the traffic that you choose.
I hope this has been helpful!
Laz
Hello Irfan
Assigning different security levels to different inside networks on an ASA gives you more control over which networks can communicate with which. By making INSIDE1 (70) and INSIDE2 (80) security levels different, you allow communication initiated from INSIDE2 → INSIDE1 but not the other way around. Rene could have set both to 100, and that would work fine. If both were set to 100, they would be able to communicate with each other regardless of who initiated communication.
By setting different security levels, Rene here demonstrated the additional control you have over communication from network to network using the ASA.
I hope this has been helpful!
Laz
Hi
I want to have the following Communications
Internal → DMZ
DMZ-> Outside
Communications from Inside directly to outside should be blocked
Let me know what ACLs should be applied to what interfaces ?
Hello Surendra
The Deny Traffic from inside section of the following lesson describes how you can block traffic from the INSIDE to the OUTSIDE network specifically for HTTP to a particular destination:
If you want to completely block all communication from INSIDE to OUTSIDE, then you can do the same configuration as shown in this lesson, but with the following access list:
access-list IN_OUT_BLOCK deny any any
If you apply this in an inbound direction on the INSIDE interface, all traffic will be blocked.
I hope this has been helpful!
Laz
Laz
why the word Block before deny ?
And at the same time i can define an ACL before this ACL to allow the traffic from Inside to DMZ right ?
Something like this
access-list IN_DMZ permit any any
Hi Laz,
Yes that does makes sense, i’m running into an issue where i have a similar topology with a L3 switch and ASA with multiple VLANs but only one VLAN works at a time, i have to keep the other vlan shutdown for the network to work. If both vlans are “no shut” the traffic to the internet just drags to a point where the pages time out and as soon as i shut down one of the vlans, then internet traffic starts working fine..I have the option checked for "Enable traffic between two or more interfaces which are configured with same security levels.
Any insight would be appreciated.
Thanks..
Hello Surendra
The word “block” used in my post above is part of the name of the access list. This name can be anything, I just chose to use the term IN_OUT_BLOCK to be descriptive of what the access list does. So the command could be:
access-list LAZAROS deny any any
and it would still be correct. I just have to apply the proper name when I use the access-group command.
You don’t need to because, by default, traffic from a higher security level interface is allowed to go to a lower security level interface. In the lesson, INSIDE has a security level of 100, and DMZ a level of 50. So INSIDE–>DMZ is allowed without the configuration of any access list.
An access list is only necessary when you want to change this default behaviour. Rene has a clear description of how this works at the beginning of the lesson.
I hope this has been helpful!
Laz