Hello Gowtham.
Before we explain what mobility and RF groups are, we need to clarify certain things. I’ll start with RF Groups
RRM
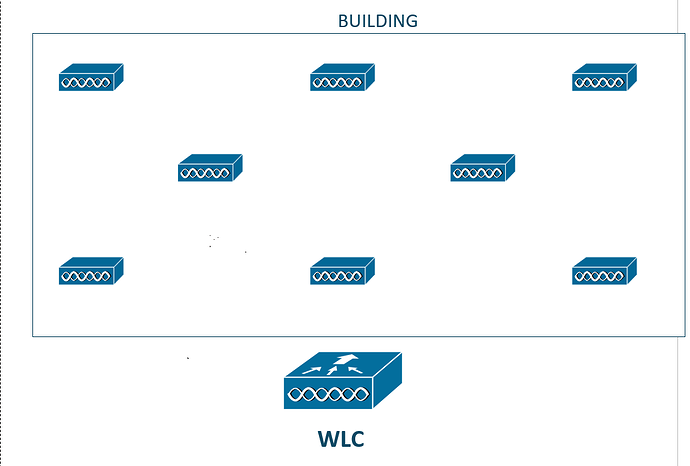
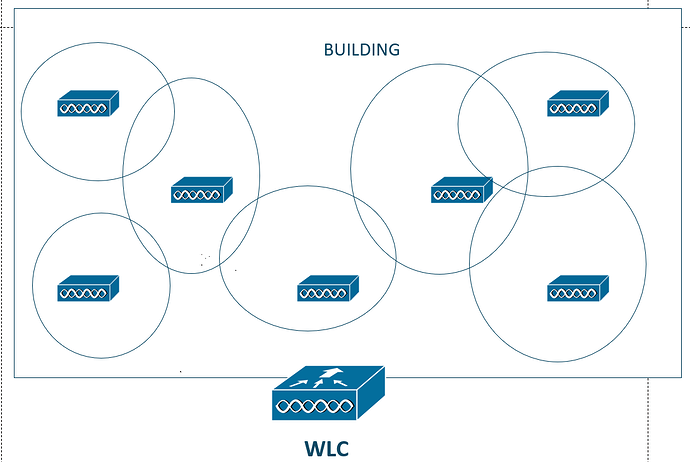
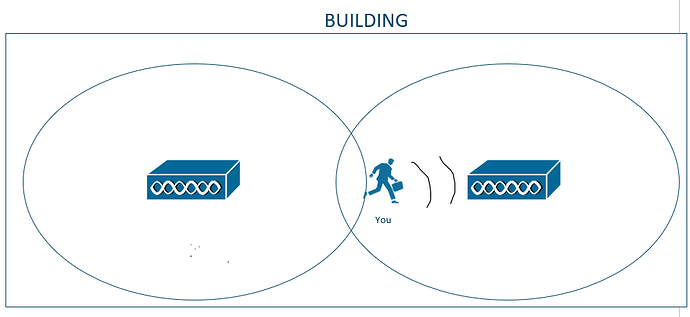
Imagine that we have a building that has several APs that are managed by a WLC.
A really cool thing that WLCs can do is provide RRM (Radio-Resource Management). In other words, the WLC can tell the APs how much signal they should transmit to provide optimal coverage for the building, to ensure that there is a decent overlap, and to prevent things like interference.
My drawing isn’t perfect but you hopefully understand my point here

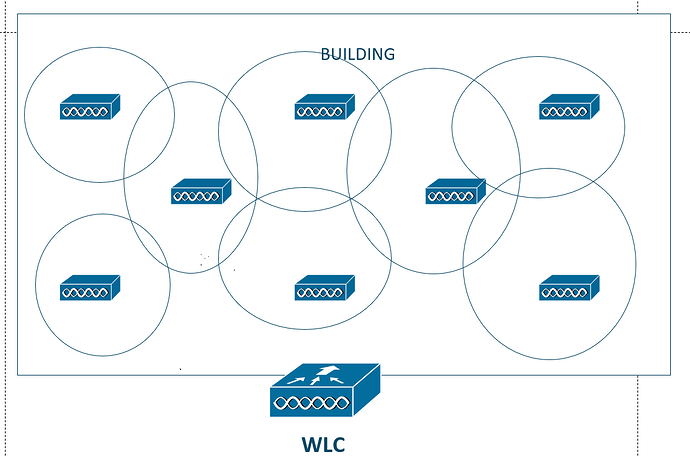
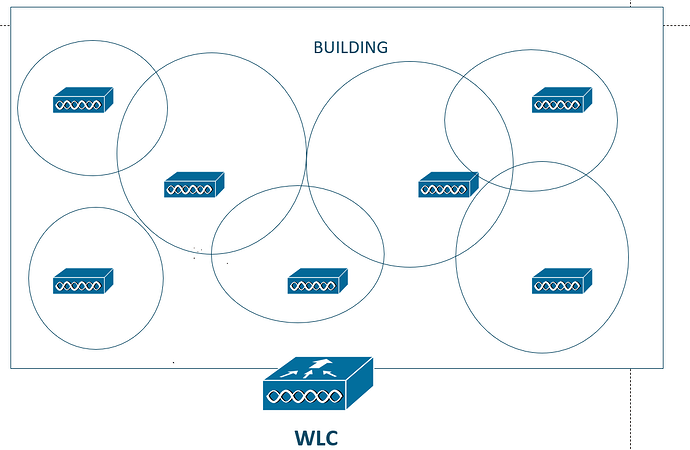
Another thing that RRM can do is provide coverage hole detection and self-healing. In other words, if an AP goes down for whatever reason
Normally, it would create a hole or a point in the network that has no wireless coverage which could create problems. If something like this happens, the WLC can tell the APs around to increase their transmit power to
cover and heal the hole.
RF Groups
If you have APs managed by multiple WLCs, the WLCs will have to exchange information and coordinate RRM together. For simplicity, the WLCs exchange information and one of them eventually becomes the leader who controls the radios based off the provided information 
In order for this to happen, the WLCs need to be part of the same RF group. If they aren’t, they won’t work and coordinate this RRM information together.
RF Groups are more of a CCNP topic so I’ve only provided a high overview for you here, assuming that you’re studying for the CCNA?
What is roaming?
Roaming occurs when a wireless client disconnects from one AP and connects to another as a result of physical movement.
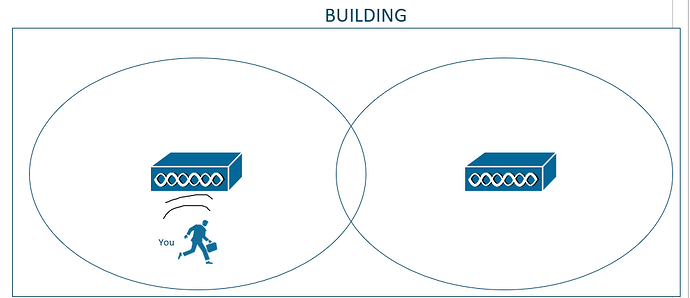
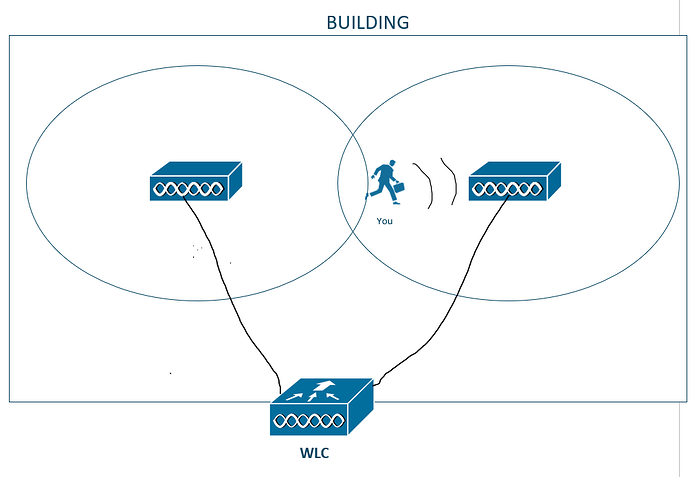
Imagine that you’re in a building that has wireless coverage that is provided by 2 APs. AP-1 covers the left side of the building while AP-2 covers the right side of the building.
If you are located on the left side of the building, you will associate to AP-1. However, what happens if you move around the building? If you decide to walk around the building and you happen to move further to the right
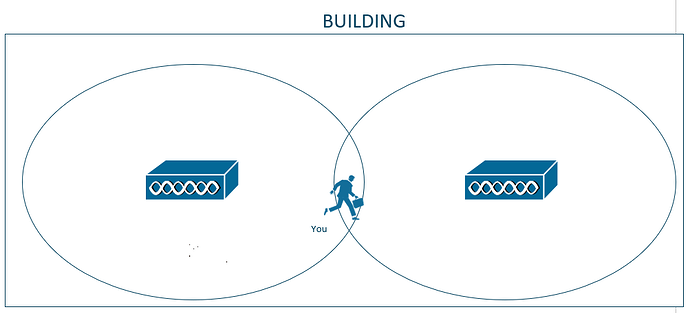
Your device will notice that there are now 2 APs broadcasting the same WiFi network. If you move even more to the right, the signal from AP-1 will become weaker while the signal from AP-2 will become stronger.
If your device notices that AP-2 is broadcasting the same WiFi network and provides a better signal, it can decide to
disconnect/disassociate from AP-1 and
connect/associate to AP-2 instead. This process is called
roaming.
The goal here is to associate and be connected to an AP that is simply providing the better and more reliable signal.
Mobility Groups
Disconnecting from one AP and connecting to another isn’t as simple as we’d like it to be unfortunately. When this happens, the client has to fully re-authenticate. During this process, the client could encounter a small window of downtime. This might be fine if you’re doing things like browsing the web but if you’re running any real-time applications (voice call/video), even a small downtime could cause noticable disruption.
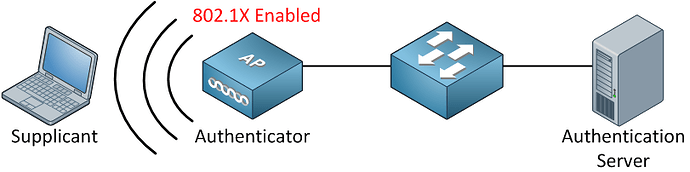
A simple home authentication (WPA Personal) where you only enter the WiFi password happens pretty quickly and the client doesn’t really notice any large downtime. However, if you work in an Enterprise where you use 802.1x and a RADIUS server for authentication (WPA Enterprise), this process could be significantly longer considering that the RADIUS server is also involved in this process.
So how can we improve this? How can we make the roaming as fast and as seamless as possible with minimal downtime? What we’re about to discuss is more of a CCNP/IE-level thing, so I’ll do my best to keep it as simple as possible.
We’ll use this topology as an example. The main point here is that both APs are managed by the same WLC for simplicity.
We know that if the client disconnects from AP-1 and connects to AP-2, depending on how our authentication and such is setup, downtime could be introduced.
For this reason, fast-roaming technologies were introduced. In simple terms, if you enable a fast-roaming technology like 802.11r or CCKM, the WLC will preserve/store a portion of the client’s original authentication and session information and will provide it to AP-2 once the client roams. This will allow the client and the AP to effectively “skip” a part of the authentication process which will make it faster.
The real process behind this can be hard to understand, especially at the CCNA level so all of this is an oversimplification.
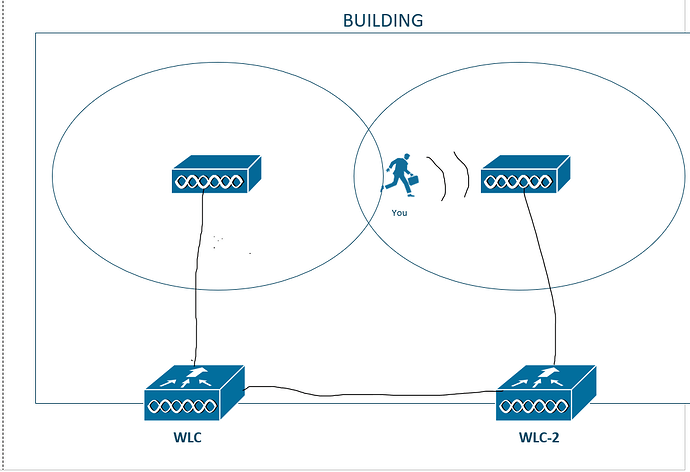
This process becomes even more complicated if the APs are managed by different WLCs
In this case, if the client roams and disconnects from AP-1 that is connected to WLC-1, WLC-1 will need to send the preserved authentication and session information to WLC-2 that manages AP-2 to make fast roaming possible.
This is where mobility groups come into play. If two controllers are part of the same mobility group (for example, lets call it NETWORKLESSONS) - they will exchange this information and thus we will have seamless roaming. If they aren’t a part of the same mobility group then they won’t exchange this information and we won’t have fast roaming.
There is a lot more to this including mobility lists/domains and such so if you want to know more, you should read these documents
If you’re studying for the CCNA and you find mobility groups hard to understand then I wouldn’t really bother covering them until later in your studies (CCNP and so on) as the CCNA doesn’t require you to know them. There’s an entire topic dedicated to roaming and mobility groups on the CCNP ENCOR exam.
Let me know if you need further help!
David