Hello Ahmedlmad
First of all let’s clarify some terminology. As far as networking goes, there are two “planes:” The control plane and the user plane.
The control plane refers to communication that takes place by protocols between networking devices for the purpose of enabling a network to function. OSPF, EIGRP, and BGP are routing protocols that operate exclusively on the control plane. Similarly, STP, CDP, DTP, VTP, and others are also control plane protocols. Other protocols such as FTP, HTTP, IMAP, and POP3 have control plane components that are used to communicate between servers and hosts to enable their functionality. These protocols also have a user plane component as well.
The user plane refers to communication that carries actual user data. The contents of the email that you sent that’s being routed over the Internet is user plane communication. Similarly, the web site you viewed, or your voice and video being sent over the network from your video telephone call is also user plane.
Another way to say the same thing is that control plane traffic has the network device itself (router, switch, firewall, etc) as the source and destination of the traffic. User plane traffic is usually transient traffic through those network devices, and is destined for other hosts.
Now we sometimes use the term “management plane” to refer to those mechanisms used to manage a network. Among those, we have CLI connectivity using SSH and Telnet and monitoring protocols such as SNMP. The management plane is not in the same category as the user and control planes, so it is not mutually exclusive with those other two. Although it sounds the same, it is a different entity.
Now having said that Telnet and SSH have a control plane component as well as a user plane component. The user plane component is composed of the actual characters that you type and is being sent over the network as bits, as well as the responses to the prompts you see on the screen. Similarly, the control plane functions of these protocols involve dealing with encryption, authentication, and successful session management. Similarly, SNMP also has a control plane and user plane component, where the control plane communication has to do with the coordination between the server and the client, while the user plane data is the actual SNMP trap information that is being sent from devices to the server.
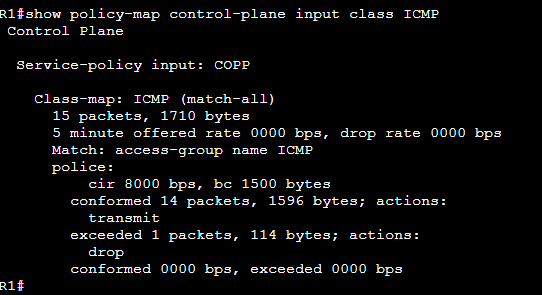
So getting to your question, why do we use CoPP to limit the packets of these protocols? Because we are limiting the traffic generated by the control plane components of those protocols.
I hope this has been helpful!
Laz