Hello guys,
I have a few problems with EIGRP and its distribute-lists.
I´m playing with filtering on R1.
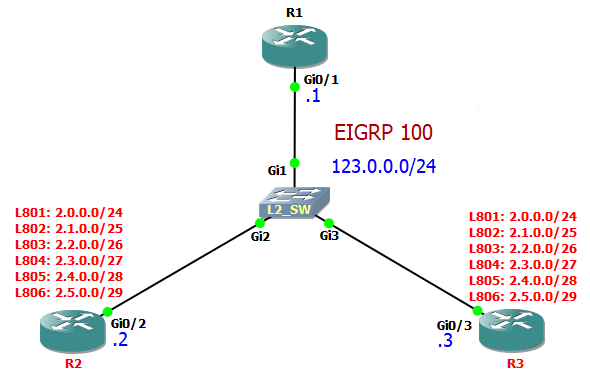
Topology looks like this.
Problem 1:
I want to block incoming route 2.1.0.0/25 (R3 Loopback 802) only from R3, using Extended Named ACL.
I cannot use Named Extended ACL in EIGRP distribute-list. Getting this error message.
R1(config)#router eigrp 100
R1(config-router)#distribute-list ACL_BLOCK_R3_L802 in
% The ACL cannot be created or an ACL with the same name but incompatible type already exists.
R1(config-router)#do show ip access-list ACL_BLOCK_R3_L802
Extended IP access list ACL_BLOCK_R3_L802
100 deny ip host 123.0.0.3 2.1.0.0 0.0.0.127
200 permit ip any any
Therefore EIGRP distribute-list is not compatabile with Named Extended ACL or it is just issue of my GNS3 emulator? I use Cisco VIRL image IOSv 15.6(2)T.
R1(config-router)# do show version | include Version
Cisco IOS Software, IOSv Software (VIOS-ADVENTERPRISEK9-M), Version 15.6(2)T, RELEASE SOFTWARE (fc2)
Everything works fine, when I use Numbered Extended ACL.
R1(config-router)#do show access-list 150
Extended IP access list 150
10 deny ip host 123.0.0.3 2.1.0.0 0.0.0.127
20 permit ip any any
R1(config-router)#do show run | section eigrp
router eigrp 100
distribute-list 150 in
network 123.0.0.1 0.0.0.0
passive-interface default
no passive-interface GigabitEthernet0/1
eigrp router-id 0.0.0.1
R1(config-router)#do show ip route eigrp | begin Gateway
Gateway of last resort is not set
2.0.0.0/8 is variably subnetted, 6 subnets, 6 masks
D 2.0.0.0/24 [90/130816] via 123.0.0.3, 00:27:43, GigabitEthernet0/1
[90/130816] via 123.0.0.2, 00:27:43, GigabitEthernet0/1
D 2.1.0.0/25 [90/130816] via 123.0.0.2, 00:02:20, GigabitEthernet0/1
D 2.2.0.0/26 [90/130816] via 123.0.0.3, 00:27:43, GigabitEthernet0/1
[90/130816] via 123.0.0.2, 00:27:43, GigabitEthernet0/1
D 2.3.0.0/27 [90/130816] via 123.0.0.3, 00:27:43, GigabitEthernet0/1
[90/130816] via 123.0.0.2, 00:27:43, GigabitEthernet0/1
D 2.4.0.0/28 [90/130816] via 123.0.0.3, 00:27:43, GigabitEthernet0/1
[90/130816] via 123.0.0.2, 00:27:43, GigabitEthernet0/1
D 2.5.0.0/29 [90/130816] via 123.0.0.3, 00:27:43, GigabitEthernet0/1
[90/130816] via 123.0.0.2, 00:27:43, GigabitEthernet0/1
Problem 2:
I want to do the same using route-map. On R1 block route L802 2.1.0.0/25 comming from R3.
Numbered Extended ACL should pass route 2.1.0.0/24 from R3 to route-map´s deny statement, so route from R3 will be denied.
Configuration looks like this:
R1(config-router)#do show run | sec eigrp
router eigrp 100
distribute-list route-map RM_DENY_R3_L802 in
network 123.0.0.1 0.0.0.0
passive-interface default
no passive-interface GigabitEthernet0/1
eigrp router-id 0.0.0.1
R1(config-router)#do show route-map RM_DENY_R3_L802
route-map RM_DENY_R3_L802, deny, sequence 100
Match clauses:
ip address (access-lists): 199
Set clauses:
Policy routing matches: 0 packets, 0 bytes
route-map RM_DENY_R3_L802, permit, sequence 200
Match clauses:
Set clauses:
Policy routing matches: 0 packets, 0 bytes
R1(config-router)#do show access-list 199
Extended IP access list 199
10 permit ip host 123.0.0.3 2.1.0.0 0.0.0.127
20 deny ip any any (12 matches)
I dont see any matches in ACL 199 sequence 10, therefore we can´t see any matches in route-map and 2.1.0.0/25 route from R3 makes it to R1´s EIGRP topology table and from there to global ip routing table.
R1(config-router)#do show ip route | sec 2.1.0.0/25
D 2.1.0.0/25 [90/130816] via 123.0.0.3, 00:13:11, GigabitEthernet0/1
[90/130816] via 123.0.0.2, 00:13:11, GigabitEthernet0/1
Why is ACL 199 not matching route 2.1.0.0/25 from R3 (123.0.0.3)?
Edit: some debug output added
R1#debug ip eigrp
EIGRP-IPv4 Route Event debugging is on
R1#clear ip eigrp neighbors 123.0.0.3
000281: %DUAL-5-NBRCHANGE: EIGRP-IPv4 100: Neighbor 123.0.0.3 (GigabitEthernet0/1) is up: new adjacency
.
.
.
000300: EIGRP-IPv4(100): Processing routemap RM_DENY_R3_L802 tableid:(0) map(10881098) for addr: 2.1.0.0/25
000301: EIGRP-IPv4(100): Int 2.1.0.0/25 M 130816 - 1000000 5010000000 SM 128256 - 4060086272 76293
000302: EIGRP-IPv4(100): table(default): route installed for 2.1.0.0/25 (90/130816) origin(123.0.0.2)
000303: EIGRP-IPv4(100): table(default): route installed for 2.1.0.0/25 (90/130816) origin(123.0.0.3)