Hi Mithun,
These are not the same. Take a look at this picture from my IPsec lesson:
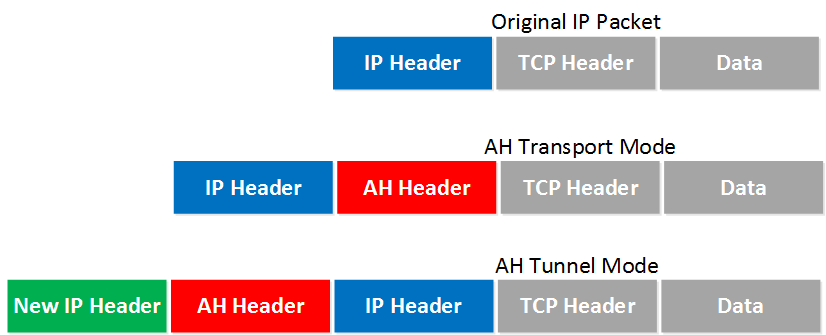
When we use IPsec tunnel mode, we encapsulate the original IP packet and put an AH or ESP header and new IP header in front of it. IPsec only supports unicast packets.
GRE also encapsulates IP packets and it supports multicast traffic. It adds a GRE header in front of the original IP packet and then a new IP header. You can see this in this capture file:
GRE and IPsec tunnel mode both encapsulate IP packets. GRE doesn’t offer any encryption though.
When we combine GRE and IPsec, normally we use IPsec transport mode. GRE has already added a new IP header so there’s no need for IPsec to do it again. That’s why you can use transport mode.
Hope this helps ![]()
Rene