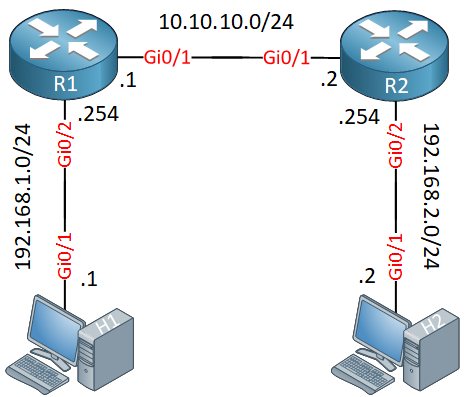
Hi Hussein,
The only thing you have to change is the transform set:
R1(config)#crypto ipsec transform-set MY_TRANSFORM_SET ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
ah-sha256-hmac AH-HMAC-SHA256 transform
ah-sha384-hmac AH-HMAC-SHA384 transform
ah-sha512-hmac AH-HMAC-SHA512 transform
comp-lzs IP Compression using the LZS compression algorithm
esp-3des ESP transform using 3DES(EDE) cipher (168 bits)
esp-aes ESP transform using AES cipher
esp-des ESP transform using DES cipher (56 bits)
esp-gcm ESP transform using GCM cipher
esp-gmac ESP transform using GMAC cipher
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-null ESP transform w/o cipher
esp-seal ESP transform using SEAL cipher (160 bits)
esp-sha-hmac ESP transform using HMAC-SHA auth
esp-sha256-hmac ESP transform using HMAC-SHA256 auth
esp-sha384-hmac ESP transform using HMAC-SHA384 auth
esp-sha512-hmac ESP transform using HMAC-SHA512 auth
For example, if you want to use AH:
R1(config)#crypto ipsec transform-set MY_TRANSFORM_SET ah-sha-hmac
or ESP:
R1(config)#crypto ipsec transform-set MY_TRANSFORM_SET esp-aes esp-sha-hmac
or ESP+AH:
R1(config)#crypto ipsec transform-set MY_TRANSFORM_SET esp-sha-hmac ah-sha-hmac esp-aes
If you want to test this, change the transform-set and then clear the current SA:
R1#clear crypto sa
You can verify if you are using ESP/AH by looking at the SA. For example, here’s ESP:
R1#show crypto ipsec sa | begin inbound esp
inbound esp sas:
spi: 0x52BDAEFA(1388162810)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 5, flow_id: SW:5, sibling_flags 80004040, crypto map: MY_CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4241877/3557)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x7D2533B3(2099590067)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 6, flow_id: SW:6, sibling_flags 80004040, crypto map: MY_CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4241877/3557)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
Above you see that it only shows inbound/outbound ESP, nothing at AH.
Here’s AH:
R1#show crypto ipsec sa | begin inbound ah
inbound ah sas:
spi: 0xC412FE1D(3289579037)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 7, flow_id: SW:7, sibling_flags 80004050, crypto map: MY_CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4189277/3584)
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound pcp sas:
outbound esp sas:
outbound ah sas:
spi: 0xBF33F950(3207854416)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 8, flow_id: SW:8, sibling_flags 80004050, crypto map: MY_CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4189277/3584)
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound pcp sas:
Above you only see inbound/outbound ESP, no AH.
Here is AH+ESP:
R1#show crypto ipsec sa | begin inbound
inbound esp sas:
spi: 0xD68D5E92(3599589010)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 9, flow_id: SW:9, sibling_flags 80004070, crypto map: MY_CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4298169/3577)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
spi: 0x58397E06(1480162822)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 9, flow_id: SW:9, sibling_flags 80004070, crypto map: MY_CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4298169/3577)
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound pcp sas:
outbound esp sas:
spi: 0x2CA509F3(749013491)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 10, flow_id: SW:10, sibling_flags 80004070, crypto map: MY_CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4298169/3577)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
spi: 0x110A4D8E(285887886)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 10, flow_id: SW:10, sibling_flags 80004070, crypto map: MY_CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4298169/3577)
replay detection support: Y
Status: ACTIVE(ACTIVE)
Here is a quick example for a virtual tunnel interface. I’ll turn this one into a lesson later:
Here are the configs of the routers.
R1:
hostname R1
!
ip cef
!
crypto isakmp policy 1
encr aes
authentication pre-share
group 2
crypto isakmp key MY_PASSWORD address 10.10.10.2
!
crypto ipsec transform-set MY_TRANSFORM_SET esp-aes esp-sha-hmac
mode tunnel
!
crypto ipsec profile IPSEC_PROFILE
set transform-set MY_TRANSFORM_SET
!
interface Tunnel0
ip address 12.12.12.1 255.255.255.0
tunnel source 10.10.10.1
tunnel mode ipsec ipv4
tunnel destination 10.10.10.2
tunnel protection ipsec profile IPSEC_PROFILE
!
interface GigabitEthernet0/1
ip address 192.168.1.254 255.255.255.0
!
interface GigabitEthernet0/2
ip address 10.10.10.1 255.255.255.0
!
ip route 192.168.2.0 255.255.255.0 Tunnel0
!
end
And R2:
hostname R2
!
ip cef
!
crypto isakmp policy 1
encr aes
authentication pre-share
group 2
crypto isakmp key MY_PASSWORD address 10.10.10.1
!
crypto ipsec transform-set MY_TRANSFORM_SET esp-aes esp-sha-hmac
mode tunnel
!
crypto ipsec profile IPSEC_PROFILE
set transform-set MY_TRANSFORM_SET
!
interface Tunnel0
ip address 12.12.12.2 255.255.255.0
tunnel source 10.10.10.2
tunnel mode ipsec ipv4
tunnel destination 10.10.10.1
tunnel protection ipsec profile IPSEC_PROFILE
!
interface GigabitEthernet0/1
ip address 192.168.2.254 255.255.255.0
!
interface GigabitEthernet0/2
ip address 10.10.10.2 255.255.255.0
!
ip route 192.168.1.0 255.255.255.0 Tunnel0
!
end
The main difference is that we don’t use a crypto-map anymore. We still have a crypto isakmp policy and a transform set. What is new is that we have a crypto ipsec profile that refers to our transform-set. We also use a tunnel interface where we refer to our IPSec profile and where Ipsec is enabled.
The tunnel interface now shows IPSEC/IP:
R1#show interfaces tunnel 0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 12.12.12.1/24
MTU 17878 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel linestate evaluation up
Tunnel source 10.10.10.1, destination 10.10.10.2
Tunnel protocol/transport IPSEC/IP
We can verify that it works:
R1#show crypto session
Crypto session current status
Interface: Tunnel0
Session status: UP-ACTIVE
Peer: 10.10.10.2 port 500
Session ID: 0
IKEv1 SA: local 10.10.10.1/500 remote 10.10.10.2/500 Active
Session ID: 0
IKEv1 SA: local 10.10.10.1/500 remote 10.10.10.2/500 Active
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 6, origin: crypto map
Hope this helps!
Rene