Thanks for the explanation.
Hi Rene, first of all great lesson. However, on the last portion beneath the command of #show nat translations, it says “And as you can see host2 has been translated to IP address 192.168.2.11.” It should be 192.168.23.11, right?
One more question. for the ip nat pool range creation, the prefix-length is the same as the subnet mask, correct? I am seeing in my packet tracer it wants the netmask command instead of the prefix-lenght at the end:
#ip nat pool MYPOOL 192.168.23.1 192.168.23.20 netmask 255.255.255.0
thanks!
Greg
Hello Greg
Yes, you are correct, thanks for catching that! I’ll let @ReneMolenaar know to make the change…
You can specify the network to which this range belongs by using either the netmask keyword or the prefix-length keyword. Both do the same thing, they just indicate it in different ways. For example, the following two commands are identical:
ip nat pool MYPOOL 192.168.23.1 192.168.23.20 netmask 255.255.255.0
ip nat pool MYPOOL 192.168.23.1 192.168.23.20 prefix-length 24
More info about this command can be found at this Cisco command reference:
Because packet tracer is a simulator (and not an emulator) it does not have the full commands and feature sets that real devices have. For this reason, it seems that the designers considered it superfluous to have both the netmask and prefix-length keywords available.
I hope this has been helpful!
Laz
I think the IP address that host 2 is translated to is 192.168.23.11.
I have always been a bit confused by the prefix command at the end of the pool command.
I wondered why I only had 10 ip addresses but such a huge prefix-length. I thought I would mention what I discovered here.
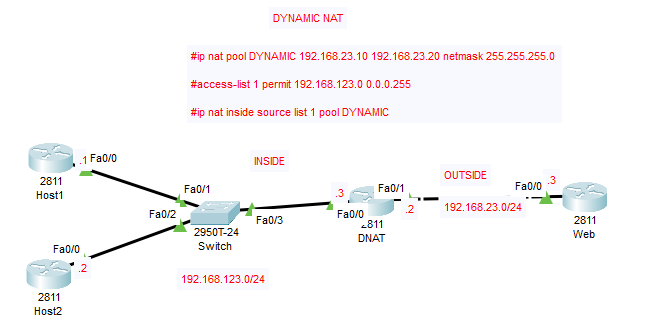
when using Dynamic NAT you have two goals.
- You need an inside global(an IP that you translate to)
- You need to be in the same subnet as the router interfaces on that link.
so when the translation happens you will end up translating the IP address to some ip between 192.168.23.10-192.168.23.20 with a mask of /24
Hello Justin
Yes, you are correct, the lesson has a typo, and I’ll let Rene know to make the correction.
Also, thanks for sharing your understanding of the prefix-length keyword. Indeed it is not used to define the range of addresses, since the range is clearly stated by the “start IP” and “end IP” addresses in the ip nat pool command. The prefix length does indeed indicate the mask of the translated address to determine if a packet needs to be sent directly to the host (if it is in the same subnet) or to the next hop router (if it is in a different subnet).
I will create a new NetworkLessons note soon that describes this and I will reference your post.
Thanks so much!
Laz
Hello Justin
Here’s the NetworkLessons note on the prefix-length keyword at the end of the nat pool command.
Thanks for your input!
Laz
Hello Amran
From the information you have shared here, I don’t see any reason for this not to work. The only difference you have from the lesson is that you are using the netmask instead of prefix-length keyword, but in both cases, the result is the same. (Take a look at this NetworkLessons note about how the prefix-length keyword is used with NAT for more info.)
I hope this has been helpful!
Laz
What if 254 host (for example:192.168.123.0/24) tries connecting Web server at same time and we have configured a dynamic NAT pool of 10 IPs (for example:192.168.23.10 to 192.168.23.20). Then will the NAT operation will perform properly? If yes, then can you explain how it will connect. As I am assuming if first 10 private host connect, it would be translated to 10 public IP and after that the NAT pool will be exhausted.
Hello Debabrata
If all 254 hosts try to connect at the same time, and you have only 10 IP outside addresses in your dynamic NAT pool for translation, then only 10 of the hosts will be able to successfully communicate. The NAT pool will indeed become exhausted.
The NAT operation will perform properly, but only for those 10 hosts, the rest will be unable to communicate.
Now I understand that your question focuses on the idea that 254 hosts connect “at the same time” so the question has to do with, how the NAT router deals with all these simultaneous connection attempts, right?
Well, in a network, things rarely happen simultaneously. Packets are always sent sequentially. Even if a switch receives multiple frames at the same time that are destined to the same egress port, it will queue them and send them out one at a time. In the same way, the inside port of the NAT router will always receive packets in sequential order. So even if 254 hosts try to connect to the web at EXACTLY the same time, the network will sort out those packets into a specific sequence. So the NAT router will receive them sequentially, and only the first 10 connection attempts will be translated. The 11th and above will fail. Does that make sense?
I hope this has been helpful!
Laz
Hi Laz ,
Are you configure the NAT translation for the destination host can you advised what command you placed on NAT router ip nat outside source x.x.x.x x.x.x.x .(Traffic is from inside to outside ).
If traffic is from outside to inside means a webserver try to access to our local host then how nat translation can be acheived , i have share a snap , can you tell me how ip nat outside source static will work here and which interface should be ip nat inside and ip nat outside on NAT router shown as below
[Network Diagram removed - (see link below)]
Here is the overview can you provide some more insights
On the outside interface (S1) of Router 2514X, the ping packet shows up with a Source Address (SA) of 172.16.89.32 and a Destination Address (DA) of 172.16.68.1.
NAT translates the SA to the Outside Local Address 172.16.68.5 (correspondent to the ip nat outside source static command configured on Router 2514X).
Router 2514X then checks its routing table for a route to 172.16.68.1.
If the route does not exist, Router 2514X drops the packet. In this case, Router 2514X has a route to 172.16.68.1 through the static route to 172.31.1.0. It forwards the packet to the destination.
Router 2501E sees the packet on its incoming interface (E0) with an SA of 172.16.68.5, and a DA of 172.16.68.1.
It sends an Internet Control Message Protocol (ICMP) echo reply to 172.16.68.5. If it does not have a route, it drops the packet.
However, in this case it has the (default) route.
Therefore, it sends a reply packet to Router 2514X, with an SA of 172.16.68.1, and a DA of 172.16.68.5.
Router 2514X sees the packet and checks for a route to the 172.16.68.5 address.
If it does not have one, it responds with an ICMP unreachable reply.
In this case, it has a route to 172.16.68.5 (due to the static route).
It therefore translates the packet back to the 172.16.89.32 address, and forwards it out its outside interface (S1).
Best Regards
Shivam Chaudhary
Hello Rene, Laz, forum members.
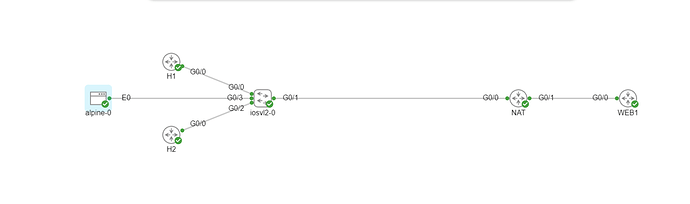
I rebuild this lab in GN3: c3620-a3jk8s-mz.122-26c.image
Again de outcome is different then what is shown in the lessons. I am sure that the configurations are right.
host 1 config.txt (898 Bytes)
host 2 config.txt (896 Bytes)
Ip nat translations outcome.txt (6.5 KB)
NAT config.txt (1.4 KB)
web1 config with and without IP routing.txt (1.7 KB)
What is the reason for the different outcome?
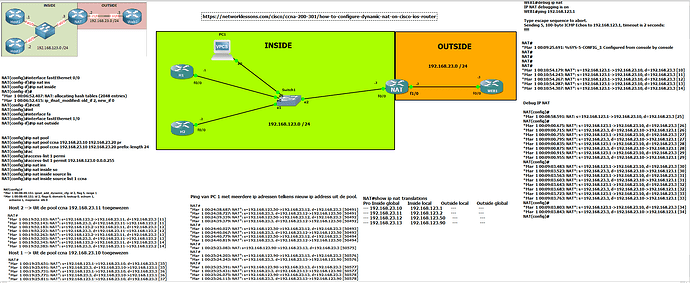
I played with an extra host pc 1 and changed the IP address a few times. You can see that NAT gives out new IP addresses every time I changed te IP address of PC1.
I enabled debug IP nat on the NAT device.
When I give the command show ip nat tranlation the outcome is different then the outcome in de lesson! I don’t see the Outside local of global ip addresses.
See configs and topology attached to this ticket.
Please can someone explain why I get a different outcome while the configurations are identical?
Best regards,
Michel
###########################################################
Update. Made the same lab in CML 2.6
NAT#show ip nat translation
Pro Inside global Inside local Outside local Outside global
icmp 192.168.23.10:2 192.168.123.1:2 192.168.23.3:2 192.168.23.3:2
--- 192.168.23.10 192.168.123.1 --- ---
--- 192.168.23.11 192.168.123.2 --- ---
NAT#
NAT#
*Jun 22 15:03:08.834: NAT*: s=192.168.123.2->192.168.23.11, d=192.168.23.3 [5]
*Jun 22 15:03:08.836: NAT*: s=192.168.23.3, d=192.168.23.11->192.168.123.2 [5]
*Jun 22 15:03:08.840: NAT*: s=192.168.123.2->192.168.23.11, d=192.168.23.3 [6]
*Jun 22 15:03:08.840: NAT*: s=192.168.23.3, d=192.168.23.11->192.168.123.2 [6]
*Jun 22 15:03:08.844: NAT*: s=192.168.123.2->192.168.23.11, d=192.168.23.3 [7]
*Jun 22 15:03:08.846: NAT*: s=192.168.23.3, d=192.168.23.11->192.168.123.2 [7]
*Jun 22 15:03:08.851: NAT*: s=192.168.123.2->192.168.23.11, d=192.168.23.3 [8]
*Jun 22 15:03:08.852: NAT*: s=192.168.23.3, d=192.168.23.11->192.168.123.2 [8]
*Jun 22 15:03:08.858: NAT*: s=192.168.123.2->192.168.23.11, d=192.168.23.3 [9]
*Jun 22 15:03:08.858: NAT*: s=192.168.23.3, d=192.168.23.11->192.168.123.2 [9]
*Jun 22 15:03:10.191: NAT: expiring 192.168.23.10 (192.168.123.1) icmp 2 (2)
NAT#
NAT#show ip nat translation
Pro Inside global Inside local Outside local Outside global
--- 192.168.23.10 192.168.123.1 --- ---
icmp 192.168.23.11:1 192.168.123.2:1 192.168.23.3:1 192.168.23.3:1
--- 192.168.23.11 192.168.123.2 --- ---
NAT#show ip nat translation
Pro Inside global Inside local Outside local Outside global
icmp 192.168.23.10:2 192.168.123.1:2 192.168.23.3:2 192.168.23.3:2
--- 192.168.23.10 192.168.123.1 --- ---
--- 192.168.23.11 192.168.123.2 --- ---
Same configuration. In CML it is working and the outcome is as expected.
Hello Michel
The output from various commands, such as those that list the NAT translations on Cisco routers, may differ slightly based on various factors. These include:
- Different IOS versions. Each version may output the translations in a slightly different manner.
- The time at which you issue the commands. Because translations change over time, and will depend on what traffic has actually traversed the router, when you issue the verification show command will make the output different
The fact that the output is the same in the topology you created with CML makes sense, because Rene has created these labs using CML, so it is likely you are using the same router images.
The goal of the lab is not necessarily to recreate EXACTLY the output that we see in the lab. The point is to ensure that the lab is functioning as expected, translations are taking place, and connectivity is achieved. From a brief look at your results, it seems that you have successfully communicated across the NAT router and the translations look good. Other than the difference in the output, do you see any failures in your communication or is there anything that doesn’t seem to be working properly? If so, let us know so that we can help you further…
I hope this has been helpful!
Laz
Hello Laz,
Thank you for your explanation. Again very clear.
I just decided to make the labs of www.networklessons.com in CML and the lessons of the GNS3 vault with GNS3 becaus like you said Rene uses them respectively. I think that makes sense.
Best regards,
Michel
Hello Shivam
First of all, I removed the diagram from your post in order to avoid any copyright violations from Cisco. I have included a link below to the original Cisco documentation you got the diagram from as well as the text you shared.
The ip nat outside source command is used to translate traffic that ORIGINATES on the outside. When we say “originates” we mean that the communication was instigated by a device on the outside. For example, a ping was initiated from a host on the Internet towards your internal PC. If you have correctly set up the ip nat outside source command, then such a communication would be successful, and you would have a response from the PC towards the host on the Internet.
If however, you want to accommodate traffic that originates on the inside, such as from your PC, then you must also issue the ip nat inside source command. Otherwise, no NAT translations can take place for traffic originating on the inside.
The example you shared is a good step-by-step example of communication that originates on the outside and reaches the inside device. And there is a response to that with an ICMP reply packet. It is able to be translated on the way back because it is identified as a response to the original communication from the outside device.
For other readers who may be wondering, the diagram and the explanation text come from the following Cisco documentation:
I hope this has been helpful!
Laz
Hello, everyone.
When it comes to defining a NAT pool, the network/broadcast addresses of the public IPs should be excluded, right? For ex:
ip nat pool CISCO 9.9.9.0 9.9.9.3 netmask 255.255.255.252
The device won’t hand out the network or broadcast address for a translation to a device.
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
--- 9.9.9.1 10.1.1.11 --- ---
--- 9.9.9.2 10.1.1.22 --- ---
R1#
So if a third device was to communicate, the pool would technically be “exhausted” and the translation wouldn’t happen.
*Jan 31 08:13:59.474: NAT: translation failed (A), dropping packet s=10.1.1.33 d=73.5.9.33
*Jan 31 08:13:59.477: NAT: translation failed (A), dropping packet s=10.1.1.33 d=73.5.9.33
And in the output of show ip nat statistics, the allocated IPs would display 50% which could make us assume that NAT isn’t even the problem
R1#show ip nat statistics | begin access-list
[Id: 1] access-list 1 pool CISCO refcount 2
pool CISCO: netmask 255.255.255.252
start 9.9.9.0 end 9.9.9.3
type generic, total addresses 4, allocated 2 (50%), misses 50
That’s all, thank you.
David
Hello David
That’s a great experiment! Let me just add a bit of info about the ip nat pool command. When you issue a command like so:
ip nat pool CISCO 9.9.9.0 9.9.9.3 netmask 255.255.255.252
you are stating that you are making the 9.9.9.0, 9.9.9.1, 9.9.9.2, and 9.9.9.3 addresses available to the NAT pool, using the 255.255.255.252 subnet mask. NAT will always take into account this subnet mask and will not try to assign the network or broadcast addresses to hosts. It is “smart” enough not to do that.
Keep in mind that the ip nat pool command is quite flexible and forgiving. For example, you can do the following:
ip nat pool MYPOOL 192.168.1.1 192.168.1.254 netmask 255.255.255.128
This command gives a range of IP addresses from 192.168.1.1 to 192.168.1.254 that are available with a subnet mask of 255.255.255.128. This subnet mask is smaller than the range of addresses given. But it still works. So this command actually provides NAT translation addresses in two subnets. Specifically, it offers:
- 192.168.1.1 to 192.168.1.126
- 192.168.1.129 to 192.168.1.254
- but does not offer the 192.168.1.127, which is a broadcast address according to the subnet mask
- nor does it offer 192.168.1.128 which is a network address, based on the subnet mask provided.
In extreme cases, you can do this:
ip nat pool MYPOOL 192.168.0.0 192.168.7.255 netmask 255.255.255.240
The above gives a range of 2048 addresses but with a subnet mask that provides an address space of only 16 addresses. So this command would offer NAT translation addresses within 128 separate subnets! And it is smart enough to exclude all of the network and broadcast addresses that result from this.
Concerning the results of the NAT statistics command, the misses don’t count the number of failed address allocations but the number of translation table lookups that fail to find an entry, resulting in the creation of a new entry.
The point is that this is a valid implementation. You can choose to exclude the network and broadcast addresses from the ip nat pool command, and indeed it may be cleaner, but it’s not mandatory. As long as you keep in mind that those won’t be allocated, you should be OK.
I hope this has been helpful!
Laz