I am trying to implement policy based routing and I am seeing some strange results.
I was wondering if anyone had any ideas what the issues could be ?
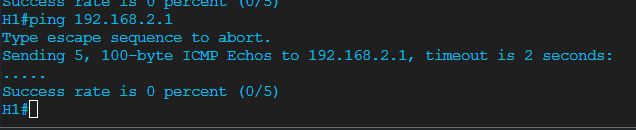
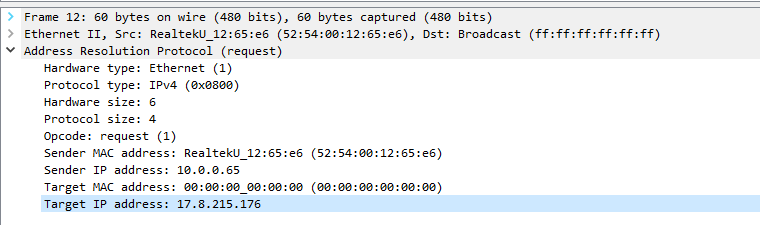
The “routing” itself appears to be working as when I do ping or traceroute I can see the results are showing that they are going to intended next hops.
However a web page such as google etc. wont open on the client that is being policy base routed.
I have used “ip” to be allowed in my acl statement and from my understanding permit ip from source to any would allow all traffic ?
My understanding is permit ip would cover all bases meaning for example I don’t have to go in and created permit “tcp eq443” etc.
Is this correct ?
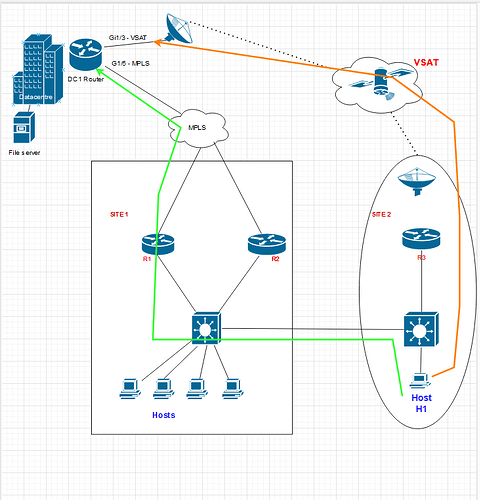
And the next issue is how pbr works with SVI’s. I understand that PBR works only on inbound traffic with the exception of local PBR.
But when applying PBR to an SVI is “inbound” seen as the traffic coming from within that SVI’s Subnet/vlan or is it seen as “inbound” traffic coming in towards that subnet/vlan ?
Also lets say I have 6 SVI’s on a switch.
vlan 10 -10.10.10.1/24
vlan 20 -20.20.20.1/24
vlan 30 -30.30.30.1/24
vlan 40 -40.40.40.1/24
vlan 50 -50.50.50.1/24
vlan 60 -60.60.60.1/24
Say the are acting as gateways for each vlan.
The switch has a direct link to 60.60.60.2/24 and uses it as the switches default gateway.
10.10.10.2/24 is also directly connected to a firewall and I need PBR the traffic from within some of the Vlans with the SVI’s to the next hop of the firewall (10.10.10.2) rather than the switch using its default gateway of 60.60.60.2
So far this is straight forward but I need Vlans 20,30,40 to be able to “route/talk” to each other on the core and if those vlans need to talk to any other address they should go to the firewall (10.10.10.2)
So for example lets take Vlan 20.
I would create the following acl MYTESTACL -
Extended ACL
Deny ip 20.20.20.0 0.0.0.255 30.30.30.0 0.0.0.255
Deny ip 20.20.20.0 0.0.0.255 40.40.40.0 0.0.0.255
Permit ip 20.20.20.0 0.0.0.255 any
I would then create a route map
Route map test permit 10
match ip address MYTESTACL
set next hop 10.10.10.2
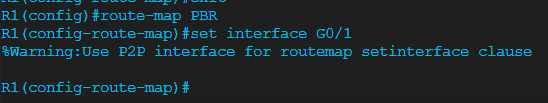
I would then apply this route map under the SVI of vlan 20.
I would then create another different acl and route map and apply to the next svi and so on…
My first question here is do I need to put a “deny” statement in the ACL for the point to point link between the switch and firewall ie. the 10.10.10.0/24 subnet ?
Do I need to add deny ip 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255 so that they will ignore they will route between each other or is it enough that the PBR is pointing to 10.10.10.2 on that subnet so that will cover anything that is needed to talk to that ?
Also instead of the ACL and route map described above should I possibly use two separate ACLS and a deny statement in the route map instead ?
For example -
Extended ACL MOUSE
permit ip 20.20.20.0 0.0.0.255 30.30.30.0 0.0.0.255
permit ip 20.20.20.0 0.0.0.255 40.40.40.0 0.0.0.255
Extended ACL DOG
permit ip 20.20.20.0 0.0.0.255 any
ROUTE MAP TEST deny 10
match ip address MOUSE (this is so vlan 20 can route between vlan 30 and 40)
permit 20
match ip address DOG (this is to policy route anything else to 10.10.10.2 (firewall)
set ip next hop 10.10.10.2
And I would then apply this to the SVI of vlan 20 and do similar but obviously slightly different acls and route maps for the other SVI’s.
Which of the above acls makes sense if any ?
Thanks.