Hi Rene/Laz,
Can you clarify if there is any limitation of NATing on opposite sides.
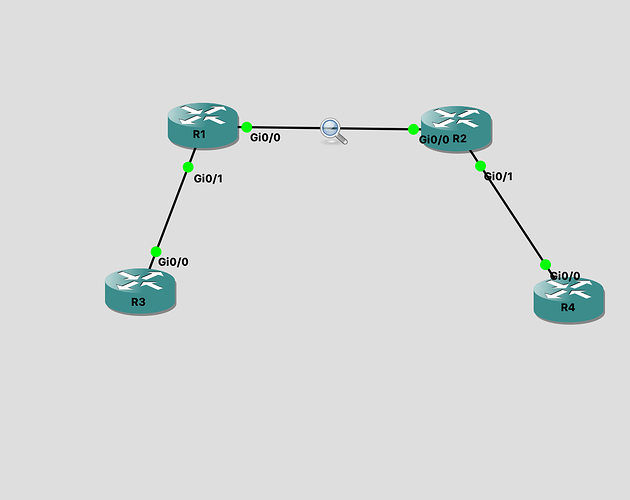
. All routers are connected using OPSF. I have 4 loopbacks on R3(1.1.1.X/32) and R4(2.2.2.X/32). I have implemented PAT on routers R1 and R2. The configs are as follows:R1:
interface GigabitEthernet0/0
ip address 192.168.1.1 255.255.255.248
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
interface GigabitEthernet0/1
ip address 10.0.0.1 255.255.255.248
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
ip nat inside source list 10 interface GigabitEthernet0/0 overload
access-list 10 permit 10.0.0.0 0.0.0.7
access-list 10 permit 1.1.1.0 0.0.0.255
access-list 10 permit any
R2:
interface GigabitEthernet0/0
ip address 192.168.1.2 255.255.255.248
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
interface GigabitEthernet0/1
ip address 11.0.0.1 255.255.255.248
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
ip nat inside source list 10 interface GigabitEthernet0/0 overload
access-list 10 permit 11.0.0.0 0.0.0.7
access-list 10 permit 2.2.2.0 0.0.0.255
access-list 10 permit any
If I dont do PAT on one of the side it works just fine, up on PATing on both sides the R3 is not able ping R4 and vice versa. From my understanding if R3 tries to ping R4 the packet flow should be as follows:
R3: 1.1.1.1 (S) ping 2.2.2.2 (D)
R1: 1.1.1.1 -> 192.168.1.1(S) while exiting interface gi0/0 to 2.2.2.2 (D)
R2: 192.168.1.1(S) -> 2.2.2.2(D)
R4: 2.2.2.2(S) -> 192.168.1.1(D)
R2: 2.2.2.2->192.168.1.2(S) ->192.168.1.1(D)
R1: 192.168.1.2(S)-> 1.1.1.1(D)
I am assuming that R1 and R2 will be stateful while performing NAT or PAT although I am not really sure, but I think this is how they remember the different ports assigned to different internal ip’s.
Attaching Screen captures of debug messages.
Can you help me find where exactly am I doing wrong or where my understanding of NATing is not right. Thanks a ton in advance.