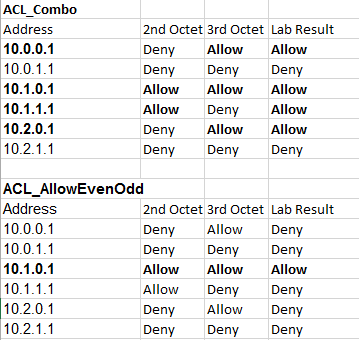
Ok, I feel like a dope. I finally broke down and charted out what was happening in a spreadsheet. After doing this it became clear.
Basically, it comes down to this–the ACL_COMBO is doing an “AND” while the ACL_ALLOWEVENODD is doing an “OR”.
Part of the confusion here is that we are using the ACLs to deny, or filter out, routes (so the logic is flipped). The ACL_COMBO is written too restrictively (hence the resulting filtered set is too large).
ACL_COMBO is saying “You are denied only if the last bit of the second octet is a zero AND the last bit of the 3rd octet is a one.”
ACL_ALLOWODDEVEN is saying, “You are denied if the last bit of the second octet is a zero OR if the last bit of the third octet is a one.”
Sheesh. I need more vitamin B-12, I suppose. Thanks for helping me think through this!