Hello Juan,
You can have two distribute lists tied to interface, one for inbound and one for outbound updates.
Correct, this is how it works in Cisco IOS. You can verify it for example using these commands.
show running-config | section eigrp
show ip protocols
First command tells you what is applied configuration under EIGRP. In your case:
- distribute-list 2 in FastEthernet0/0
Second command is going to list used filtering (including ACL for interface). You should see something like this under EIGRP output in your example.
- FastEthernet0/0 filtered by 2
So far I know, Cisco IOS allows following filtering for each process and each interface:
- 1 incoming distribute list for updates per specific interface
- 1 outgoing distribute list for updates per specific interface
- 1 incoming global distribute list for updates per specific routing process
- 1 outgoing global distribute list for updates per specific routing process
- 1 outgoing redistribution distribute list per process
Different interfaces can use different access-lists.
The way how global distribute-list per direction and distribute-list per interface per same direction inter-operate is very simple. For route to pass, it has to be permitted by both access-lists. Do not forget there is “hidden” deny any for each ACL. This “deny any” is always applied for all routes that are not permitted in the ACL. Route passes only in case its not denied in any specific ACL entry and on top of it cannot be denied by this “hidden” deny any on the end of BOTH access-lists.
Lets make one example. Imagine topology from this lesson.
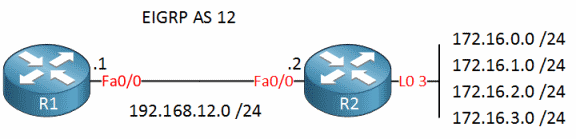
Configure imaginary ACLs on R1.
access-list 1 permit 172.16.0.0 0.0.0.0
access-list 1 permit 172.16.1.0 0.0.0.0
access-list 2 permit 172.16.1.0 0.0.0.0
access-list 2 permit 172.16.2.0 0.0.0.0
Apply access lists in EIGRP process on R1.
distribute-list 1 in
distribute-list 2 in FastEthernet0/0
With such configuration, you should see only one route 172.16.1.0 on R1. Its the only one that was permitted in both ACLs. What happened to others?
172.16.0.0 – denied by ACL 2 “hidden” deny any
172.16.1.0 – permitted by ACL 1 and ACL 2, thus its the only route that passed.
172.16.2.0 – denied by ACL 1 “hidden” deny any
172.16.3.0 – denied by “hidden” deny any of ACL 1 and ACL 2
The example used within link Laz provided is indeed correct, but can be missleading. There is configuration they used.
access-list 1 permit 1.0.0.0 0.255.255.255
access-list 2 permit 1.2.3.0 0.0.0.255
router rip
distribute-list 2 in ethernet 0
distribute-list 1 in
If we are speaking about route 1.2.3.0, what happens when update with network 1.2.3.0 comes in?
- Its permitted by interface distribute list using ACL 2.
- Its permitted by global distribute list ACL 1, because it falls into range 1.x.x.x
But imagine that ACL is written like this:
access-list 1 permit 1.0.0.0 0.1.255.255
In such case, route 1.2.3.0 would be denied by “hidden” deny any within ACL 1.