Hello Shivam
Yes, it is possible to apply the access lists as you mention in your post. Keep in mind that you can apply one access list per direction per interface. This means that you can have both an inbound and an outbound access list applied to the same interface. You can even have the same access list applied in both directions on a single interface. For example, you can have this:
interface GigabitEthernet0/0
ip address 10.10.10.1 255.255.255.0
ip access-group 1 in
ip access-group 1 out
!
interface GigabitEthernet0/1
ip address 10.10.20.1 255.255.255.0
ip access-group 1 in
ip access-group 2 out
!
access-list 1 permit 0.0.0.0 255.255.255.0
access-list 2 permit 0.0.0.0 255.255.255.0
Notice that for GE0/0, the same access list is applied in both directions, while on GE0/1, different access lists are applied in each direction. But you can have the same access list applied to multiple interfaces as well.
You know that it is meant for destination traffic because the extended access list has the following syntax:
access-list access-list-number {deny|permit} protocol source source-wildcard destination destination-wildcard
So you see that after the protocol is specified, you begin with the source address and wildcard mask, and then the destination address and wildcard mask. So for the following command:
(config)#ip access-list extended out_acz_in
(config-nacl)#permit ip any host 10.0.32.10
…the any keyword specifies the source, and the 10.0.32.10 specifies the destination. When there is no subnet mask applied, then the assumed wildcard mask is 0.0.0.0, which means that the destination specifies only a single host with that address.
This is just a name used to name the access list. You can call it anything you like.
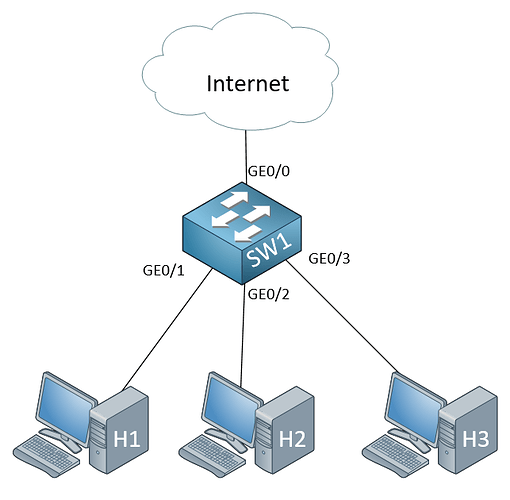
Imagine you have the following topology:
Now if you want to block traffic to the 147.52.0.0/16 network on the Internet, for example, then you would create an ACL such as this:
(config)#ip access-list extended block_147.52
(config-nacl)#deny ip any 147.52.0.0 0.0.0255.255
(config-nacl)#permit ip any any
Now you can apply this to the GE0/1, GE0/2, GE0/3 interfaces in an inbound direction or you can apply this to the GE0/0 interface in an outbound direction. Obviously it would be better to apply it only once to the GE0/0 interface. It is faster, more efficient, and clearer.
I hope this has been helpful!
Laz