Hi Laz,
Thank you for the reply.
This confirms some of my thoughts.
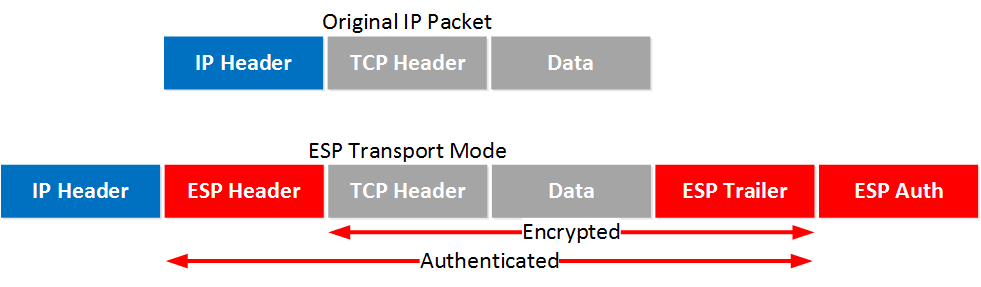
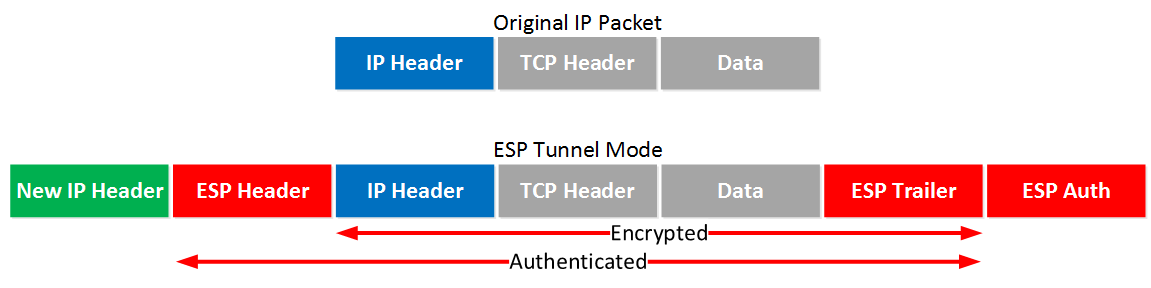
So if I use GRE with tunnel protection with tunnel mode, the GRE packet is encapsulated by ESP, and a new header is added.
Since the IPsec uses GRE to communicate, the new header has the same IP address as the tunnel source and destination.
Would you please confirm my thoughts again?
---
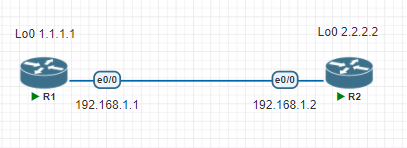
As for the link I shared, why the transport mode can not be used in the below topology?
To be honest, I am not sure I understand the explanation in the link.
Would you please explain this in more detail?
There is no GRE tunnel between R1 and R2.
I configure the transport mode for IPSec but it still uses tunnel mode.
If I configure the GRE tunnel between R1 and R2, the transport mode can be used.
The following is the configuration of both routers.
R1
crypto isakmp policy 10
encr aes
hash sha256
authentication pre-share
group 15
crypto isakmp key CISCO address 192.168.1.2
crypto ipsec transform-set TS esp-aes esp-sha256-hmac
mode transport
crypto ipsec profile IPSEC
set transform-set TS
crypto map CMAP 10 ipsec-isakmp
set peer 192.168.1.2
set transform-set TS
match address ICMP
interface Ethernet0/0
ip address 192.168.1.1 255.255.255.0
duplex auto
crypto map CMAP
end
ip access-list extended ICMP
permit icmp any any
interface Loopback0
ip address 1.1.1.1 255.255.255.255
end
R2
crypto isakmp policy 10
encr aes
hash sha256
authentication pre-share
group 15
crypto isakmp key CISCO address 192.168.1.1
crypto ipsec transform-set TS esp-aes esp-sha256-hmac
mode transport
crypto ipsec profile IPSEC
set transform-set TS
crypto map CMAP 10 ipsec-isakmp
set peer 192.168.1.1
set transform-set TS
match address ICMP
interface Ethernet0/0
ip address 192.168.1.2 255.255.255.0
duplex auto
crypto map CMAP
end
ip access-list extended ICMP
permit icmp any any
interface Loopback0
ip address 2.2.2.2 255.255.255.255
end
show crypto ipsec sa on R1
inbound esp sas:
spi: 0x946E41E6(2490253798)
transform: esp-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 3, flow_id: SW:3, sibling_flags 80000040, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4179069/1873)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x28C59527(684037415)
transform: esp-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 4, flow_id: SW:4, sibling_flags 80000040, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4179069/1873)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
Thank you
Best regards,
James