Hello Yuta
IPSec functions in two modes. Tunnel mode and transport mode. Tunnel mode is when IPSec is the protocol that is used for tunneling and for encapsulation. This is the case when we configure the following:
tunnel mode ipsec ipv4
tunnel protection ipsec profile profile_name
where the profile as shown in the lesson chooses to use the tunnel mode for IPSec.
Whenever you choosetunnel mode ipsec ipv4 it is necessary to include the type of encapsulation mechanisms that you will use by indicating the tunnel protection command as well. These two commands together will have the result of implementing an IPSec Tunnel Mode connection. The first indicating the tunnel mode and the second indicating the way in which that tunnel mode will be implemented.
Now, if you were to use these two commands:
tunnel mode gre
tunnel protection ipsec profile profile_name
then you are configuring a GRE tunnel with IPSec protection. This essentially is configuring IPSec in transport mode. In this case, the correct configuration would be to change the profile to indicate mode transport.
IPSec transport mode is usually used when another tunneling protocol (like GRE) is used to first encapsulate the IP data packet, then IPSec is used to protect the GRE tunnel packets. IPSec protects the GRE tunnel traffic in transport mode.
The following image gives us an idea of the difference between the modes.
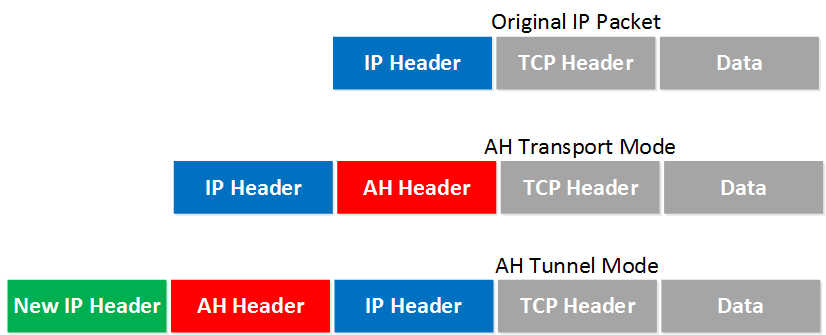
More information about these modes can be found at the following introductory lesson to IPSec:
https://networklessons.com/cisco/ccie-routing-switching-written/ipsec-internet-protocol-security/
Now how do you decide which case to use? Well, take a look at the characteristics of each:
- IPSec encapsulation does not support multicast
- GRE does support multicast
- IPSec is more complex to configure
- GRE is less complex
- IPSec includes security for the headers
- GRE does not include any security but payload only can be encrypted with IPSec transport mode
- GRE supports multiple Layer 3 protocols while IPSec only supports IP
These are just some of the characteristics of these two options, and based on those, you can choose what’s best for your application. Using IPSec in tunnel mode is by far the safest, but it does have drawbacks as seen above. GRE is most efficient, but it does have some security issues even when used with IPSec transport mode.
I hope this has been helpful!
Laz