Hello Sameer.
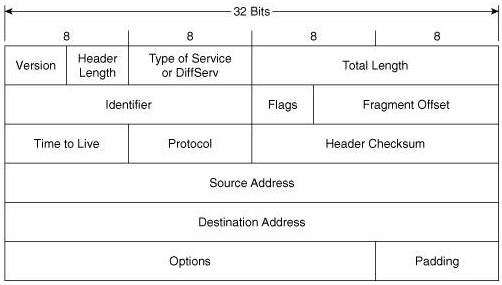
The quick answer is yes. Fragmentation will occur during encapsulation. If a PC is preparing an email to send, it will take the transport segment and encapsulate it into an IP packet. An IP packet can theoretically be up to 65535 bytes long. So during encapsulation from the Network to the Data Link layer on the PC, if an IP packet is larger than the allowable 1500 bytes (or whatever the interface MTU has been set to), then it will be fragmented into several parts and sent in multiple frames. Now the IPv4 header has some fields called Flags and Fragment Offset.
These two fields are used in order to identify fragmented packets and put them back together correctly. The Flags contain three bits:
- bit 0: Reserved; must be zero
- bit 1: Don’t Fragment (DF)
- bit 2: More Fragments (MF)
The first is not currently used. The second is used to indicate during encapsulation that this packet should not be fragmented. The third is the one used for reassembly, which is 1 if there are additional fragments of this IP packet coming in additional frames or if this is the last one. The Fragment offset is used to specify the offset of a particular fragment relative to the beginning of the original unfragmented packet. This way, the reassembly can take place correctly.
Reassembly is performed during the deencapsulation processes when the multiple frames reach the destination. The frames are deencapsulated and the IP headers are examined. Because the MF bit will be set to 1, the receiver keeps the current IP packet in memory and receives the next one and the next until the MF=0. Once all the fragments are collected, the Fragment offset is used to reassemble the packet correctly before deencapsulation is continued upwards towards the Transport and Application Layers.
I hope this has been helpful!
Laz