Hello Fadi
Thanks a lot
Hello Laz
Thanks a lot
Does anyone have a use case for BPDUfilter? I have come up empty handed ![]()
I have seen a topology connecting a provider network L2 topology to a customer network L2 topology, however, I miss the explanation on when that would ever happen
Hello Orla
Take a look at this NetworkLessons note on the BPDU filter feature for more info.
One possible use case is when you have a multi-tenant situation, where a building owner provides network facilities to tenants. You don’t want the tenants to participate in the STP of the network infrastructure, you can use BPDU filter to essentially ignore all BPDUs that arrive on such a port. That way, the port won’t go down, but will not be affected by any STP attempts, whether malicious or not. You can have a similar situation with a provider L2 network as well, the idea and logic are the same.
I hope this has been helpful!
Laz
Thanks, Laz -
That actually makes sense ![]()
/ Orla
Hi Rene,
Do you know what exactly happens when BPDU filter is enabled on trunk port between switches? It is recommended to do that? For example my scenario is with a Core Cisco switch and a Core Ruckus both working with 802.1w (rstp), where the Cisco Core is the root of all the vlans, but not all are consumed on the Ruckus Core side, only some vlans cross over the trunk link between them. I cannot find a clear answer on that anywhere. Core Cisco switch stp priority 0 and Core Ruckus switch stp priority 4096.
Does anyone know something about this topic or scenario?
Thanks
Hello Miguel
BPDU Filter should not be used on interfaces that connect to other switches, including both trunks and access ports. By doing so, you are essentially disabling STP on that port, so the connected switch will not be able to participate in STP. If you do employ such a configuration, it should be done with great caution, as it can cause a Layer 2 loop.
For more info, take a look at this NetworkLessons note on STP BPDU Filter.
In your particular case, you have some VLANs on the Cisco switch that are not included on the trunk to the Ruckus switch, correct? If the Cisco core switch is root for all VLANs, you should be OK. What is it that you want to achieve? Let us know a little bit more so that we can help you further.
I hope this has been helpful!
Laz
Hello team,
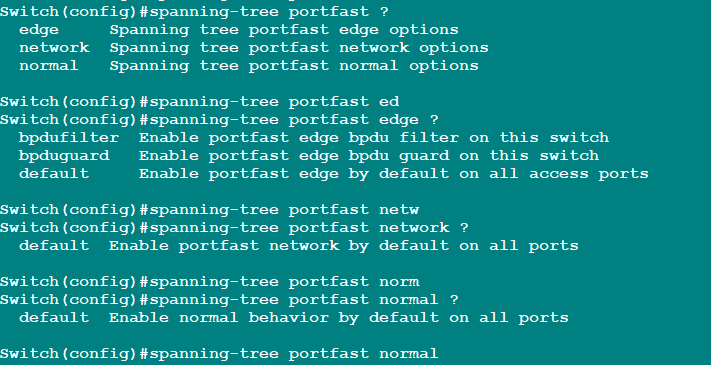
What i tried, unable to find similar global command on Cisco IOSvL2 related to BPDU filter and guard, instead i found attached one, please let me know the difference, which one should i pick (edge, network or normal).
attachment,
Hello Nahro
The difference you see here in commands has to do with the version of STP that is running. Rapid STP uses the edgeport keyword. What STP version is active will depend upon the platform and IOS being used, and the default STP version being used on that particular platform/IOS version.
Here is the command reference for the spanning-tree portfast edge bpdufilter default command:
And here is the command reference for the spanning-tree portfast bpdufilter default command:
Take a look at this thread for some more info on these commands that you see in your output:
I hope this has been helpful!
Laz
Thanks so much Sir Laz,
i’ve noticed that bpduguard and bpdufilter can be configured without spanning-tree portfast. My question is if whether bdpuguard or bpdufilter is enabled per interface or globally takes effect or not when spanning-tree portfast is not activaded (whether per interface or globally)
Hello Juan
That’s an interesting question. Indeed, the behavior of both BPDUFilter and BPDUGuard change somewhat when applied to ports with or without PortFast, and also when applied globally or on a per-interface basis. I created a NetworkLessons note on the topic to respond to your question.
If you have any further questions, let us know!
I hope this has been helpful!
Laz
Hi,
Global: if you enable BPDU filter globally then any interface with portfast enabled will not send or receive any BPDUs. When you receive a BPDU on a portfast-enabled interface it will lose its portfast status, disables BPDU filtering, and acts as a normal interface.
What is the purpose of enabling BPDU Filter Globally then?
Hello Görgen
The purpose of applying BPDU Filter globally is to cause a port configured with PortFast, to lose its PortFast status.
Remember that PortFast is applied to interfaces that we expect to be connected to hosts. BPDUs should not be received on such ports. If a BPDU is received on such a port, then it is likely that a switch has been connected to this port, or some malicious user is up to no good. In such a case, it is safer for the port to revert to functioning as a normal interface, going through the normal listening/learning/forwarding process rather than remain in the PortFast state. Does that make sense?
I hope this has been helpful!
Laz
Hello.
Is there a real-world example of where I would use this feature?
Thank you.
Hello David
The BPDU Filter feature of STP is often used in enterprise networks to improve network stability and security by controlling the transmission and reception of BPDUs on specific ports.
Imagine an enterprise network that consists of numerous access switches connecting end-user devices such as computers, IP phones, and printers. These access ports are not intended to participate in STP because the end-user devices do not need to send or receive BPDUs.
Now if an end-user connects a rogue switch to one of these access ports, it can start sending BPDUs. This can disrupt the STP topology, potentially causing network instability, loops, and outages. By enabling BPDU Filter on all user-facing access ports, you can ensure that only legitimate network devices (i.e., core and distribution switches) participate in the STP. This setup helps maintain a stable and secure network environment, even if users inadvertently or maliciously connect unauthorized networking devices.
I hope this has been helpful!
Laz
Hi.
Yes that correct, I think it depends on the platform, but when you enable it globally I will send a few of BPDUs, then it will stop.
Hello Daniel
Yes, you are correct. I have updated this NetworkLessons note on the topic to be more specific and clear about the way that the global and interface-level commands work. You can also find additional clear explanations in this Cisco documentation:
I hope this has been helpful!
Laz