Hello Hugues
In this lesson, the standard inbound access list is applied to Fa0/0 of R2. So any ping coming from R1 destined for the loopback will be blocked on its way in. Standard access lists filter based on the source address. For this reason, best practice is to place the access list as close as possible to the expected source of traffic.
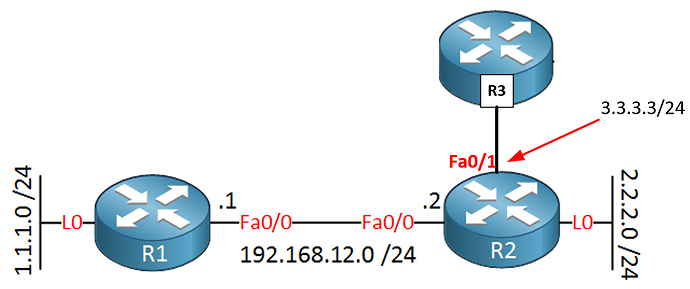
Now if you want to filter traffic on a loopback interface, configuring an ACL on the loopback interface itself will not filter traffic. This is true of Packet Tracer, and of real devices. This is because, by definition, a router will never filter traffic that is destined for itself. But this is true even of physical interfaces. Let’s say you have the following topology:
Imagine you create an access list that denies everything, and you place it on Fa0/1 of R2 like so:
access-list 99 deny any
!
interface GigabitEthernet0/1
ip address 3.3.3.3 255.255.255.0
ip access-group 99 in
ip access-group 99 out
duplex auto
speed auto
!
Now if R1 has the appropriate routing, and you try to ping 3.3.3.3, the ping will be successful! This is because you cannot filter traffic on an interface that is destined for the IP address of that interface using an ACL. If the traffic is traversing an interface but is destined for another network (not that of the interface itself) then the ACL will be applied.
So it is not so much an issue of filtering traffic to a loopback, but traffic the IP address of the interface on which the ACL is applied.
If you want to filter such traffic, you will have to use control plane policing:
I hope this has been helpful!
Laz