Can you explain me wat is VLAN access Map
Hello Akhil
A VLAN Access Map is a data structure used in the application of VACLs. Specifically, it matches specific criteria and defines an action to take. An example is the following
Router(config)# vlan access-map thor 10
Router(config-access-map)# match ip address net_10
Router(config-access-map)# action forward
Router(config-access-map)# exit
Router(config)#
Once the VLAN access map is created it does nothing. It is not in effect until it has been applied to specific VLANs. This can be done with the following command for example:
Router(config)# vlan filter thor vlan-list 12-16
This command takes the VLAN access map and applies it to VLANs 12 to 16.
I hope this has been helpful!
Laz
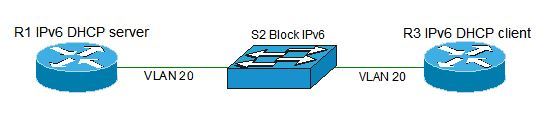
Hi, my topology is two routers with L2 switch in the middle.
I applied your method for blocking IPv6 on switch with hope, that IPv6 client wont get the IPv6 address from IPv6 server, because IPv6 should be blocked, but R3 got it anyway.
Why?
Hmm you used the same config as mine? What switch and IOS version did you use?
I removed my first question as I glossed over something that was stated that explained my questions.
it has to do with the why no Match on the 20 sequence. however I then saw this:
• Sequence number 20 doesn’t have a match statement so everything will match, the action is to forward traffic.
As a result all traffic from any host to destination IP address 192.168.1.100 will be dropped, everything else will be forwarded.
which is actually pretty interesting
also second question.
access-list makes devices work harder correct? meaning more CPU work? so having a lot can be a bad thing from design principle if not careful. meaning we want to stay away from them unless we have to have, and would that be same for VACL?
I read about that in a QoS post you had talking about classification and markings and how markings are better because classification which was ACL can make the devices work harder.
The reason that we use marking is that sometimes classification requires some complex access-lists / rules and can degrade performance on the router or switch that is doing classification. In the example above, the router receives marked packets so it doesn’t have to do complex classification using access-lists like the switch. It will still do classification but only has to look for marked packets.
Half way down page: https://networklessons.com/quality-of-service/introduction-qos-quality-service/
Hello Brian
It is true that both an access list as well as a VACL will use up more resources (CPU memory etc) of a device. And yes, this is why marking can be used instead of classification to avoid using ACLs in order to improve resource usage. However, this is an alternative for a very specific situation, specifically QoS. VACLs filter traffic within a VLAN, something that cannot be done in another way. However, keep in mind that you would require hundreds of VACLs and lots of traffic in order to reach the point of saturating the resources of a device.
I hope this has been helpful!
Laz
As always your answer is very helpful on this and the other post you have made to help explain. You have been really active on the forums of late helping out and its very appreciated!
Hi Rene,
I am trying to find out about Vxlan in all level like ccna,ccnp or ccie but not able to find out in your any lesson so do you have any own written document for Vxlan? I see some topic in google bt it’s not good actually my one of team mate wants to know about this but can’t help him and I am also interested to know about this..
So do you have any documents on this?
Thanks & Regards,
Arindom
India
Hello Arindom
There are currently no VXLAN lessons in the Networklessons site, however, as you can see from the new lessons that are coming out below, Rene continually updates content and adds materials.
I suggest you go to the Member Ideas section and post a recommendation to add VXLAN as course content.
In the meantime, if @ReneMolenaar may have something more specific for you to take a look at.
I hope this has been helpful!
Laz
Lets say i have two switches (switch A, switch B , and a trunk between them) and vlan X exists on both switches and the trunk , and i create a VACL on switch A and filter against vlan X - (maybe blocking traffic between hosts in vlan X) - will devices on switch B be effected. For instance if host 1 and 2 are both in vlan X but both are connected directly to switch B will the VACL still somehow be applied, or does the VACL have to be applied to both switches separately ? Thanks!
Hello Edgar
A VACL is applied to a particular VLAN on a particular switch. Any and all traffic that traverses that VLAN on that particular switch will be acted upon. So in the scenario that you describe, if a VACL is created on switch A, it will only affect traffic traversing switch A on VLAN X. If there is traffic from a host on switch B to another host on switch B over VLAN X, this traffic will not be affected.
I hope this has been helpful!
Laz
Hi Rene,
My Switch didn’t support the VLAN ACLs. It didn’t support the commands:
show vlan filter
show vlan access-map IOS: L3 15.4.1T.
Please suggest kindly and thanks in advance.
Hi Binod,
What switch model / platform do you use?
Rene
Hello Binod
If a specific command is not found when using a particular IOS on some platform (including WEB IOU) there is usually a restriction due to the IOS and platform combination. In this case it seems the specific commands are unavailable on this IOS on the WEB IOU platform. There’s not always a clear-cut and reasonable explanation. It happens on GNS3 as well. When using Cisco hardware however, Cisco has a clear indication of which features are available for which IOS on which platform, and this can be found at the Cisco Feature Navigator.
Sorry I couldn’t be more helpful.
Laz
Hi,
I read that MAC ACLs don’t work against IPv4 or IPv6 traffic, also when i check my virl switch running ios 15.2, i do not see any ether type for IPv4 or IPv6 (output below). can you please clarify?
Switch(config)#mac access-list extended NO-IPV6
Switch(config-ext-macl)#permit any any ?
aarp EtherType: AppleTalk ARP
amber EtherType: DEC-Amber
appletalk EtherType: AppleTalk/EtherTalk
dec-spanning EtherType: DEC-Spanning-Tree
decnet-iv EtherType: DECnet Phase IV
diagnostic EtherType: DEC-Diagnostic
dsm EtherType: DEC-DSM
etype-6000 EtherType: 0x6000
etype-8042 EtherType: 0x8042
lat EtherType: DEC-LAT
lavc-sca EtherType: DEC-LAVC-SCA
mop-console EtherType: DEC-MOP Remote Console
mop-dump EtherType: DEC-MOP Dump
msdos EtherType: DEC-MSDOS
mumps EtherType: DEC-MUMPS
netbios EtherType: DEC-NETBIOS
vines-echo EtherType: VINES Echo
vines-ip EtherType: VINES IP
xns-idp EtherType: XNS IDP
<cr>
Hello Onyi
The MAC access-list command is able to filter frames based on the Ethertype field in the Ethernet header. The list you see here in the context sensitive help in your post is a list of protocols with predefined Ethertype values for quick and easy reference. The list is not complete. You don’t have to use one of these, but you can actually input the actual hex value of the Ethertype you want. For a more complete description of the permit (or deny) statement of a MAC access list, take a look at this Cisco CLI command reference:
It is noteworthy however, that neither IPv4 or IPv6 are actually on the list that you posted, something which is actually quite unexpected. In order to filter based on these Ethertypes, you must input their Hex values, which are 0x0800 and 0x86DD respectively.
So if you want to filter based on IPv4 you must use this command:
SW1(config-ext-macl)#permit any any 0x0800 0x000
And for IPv6 use this command:
SW1(config-ext-macl)#permit any any 0x86DD 0x000
The 0x000 in both commands is called the type mask and is used to specify “don’t care bit” in order to define ranges of Ethertype values. By using 0x000, you specify that you require an exact match, so only IPv4 or IPv6 (as the case may be) are matched. You can find out more about that in the above command reference link. For a list of other common Ethertype values, take a look at this IANA link.
I hope this has been helpful!
Laz
I have a question.Can i use VACL to filter inbound for vlan?or what do you advice we use if we want to achieve filtering for vlan interfaces? Better still what is the best recommended security practice for vlan interfaces .I am trying to filter inbound to vlan 20 using mac addresses? please
Scenario: our phones are connected to a GPON which currently don’t support Mac filtering centrally and consistently.
Hello Temitope
Using VACLs in combination with MAC address filtering can result in unpredictable results. Take a look at this post:
You could use a MAC address access point on the VLAN interface (SVI) itself, and that should do what you need. You can find out more about this at the following (nicely put together) INE article:
GPON as a technology is great, but it does have some limitations as far as these more intricate detailed configurations go.
I hope this has been helpful!
Laz
Thank you for another very helpful response.just wondering..if we intend to use the MACL, we have over 200 mac addresses we want the ACL to use.will this be stored in the configuration or where?..because this might be too much in the running configuration.
What do you think?
Very respectfully