Hello, everyone.
These ACLs are quite tricky, especially if we consider the fact that they will also filter layer 2 traffic.
I have a question regarding something I encountered in CML and I am thinking that this could be an IOSvL2 bug but I have to confirm.
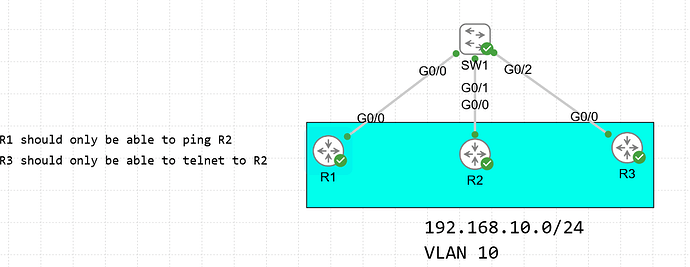
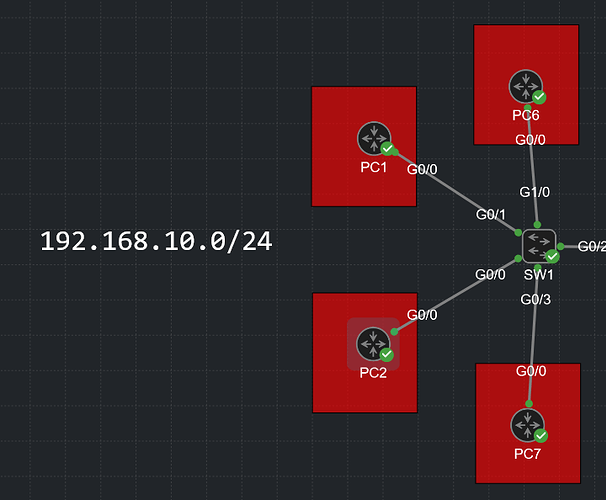
Here is my topology:
The PCs have their IP addresses configured to match their respective hostnames. So for ex: PC7 is 192.168.10.7 and they are in
VLAN 10.
My goal is to isolate PC7 and to block any traffic destined to it from the other PCs. I was using a MAC ACL to accomplish this to get some practice with it. PC7 has a MAC of 5254.0014.80ed
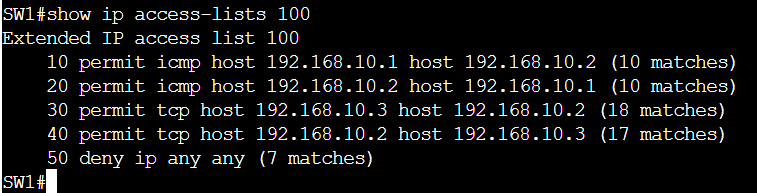
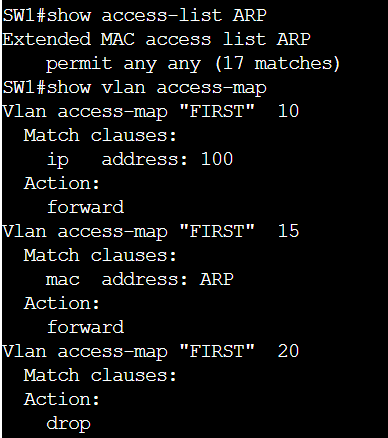
SW1(config-access-map)#do show access-lists | begin MAC
Extended MAC access list BLOCK
permit any host 5254.0014.80ed (250 matches)
deny any any (461 matches)
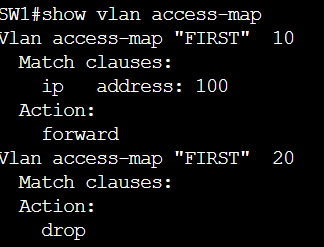
SW1(config-access-map)#do show vlan access-map BLOCK_PC7
Vlan access-map "BLOCK_PC7" 10
Match clauses:
mac address: BLOCK
Action:
drop
Vlan access-map "BLOCK_PC7" 20
Match clauses:
Action:
forward
SW1(config-access-map)#
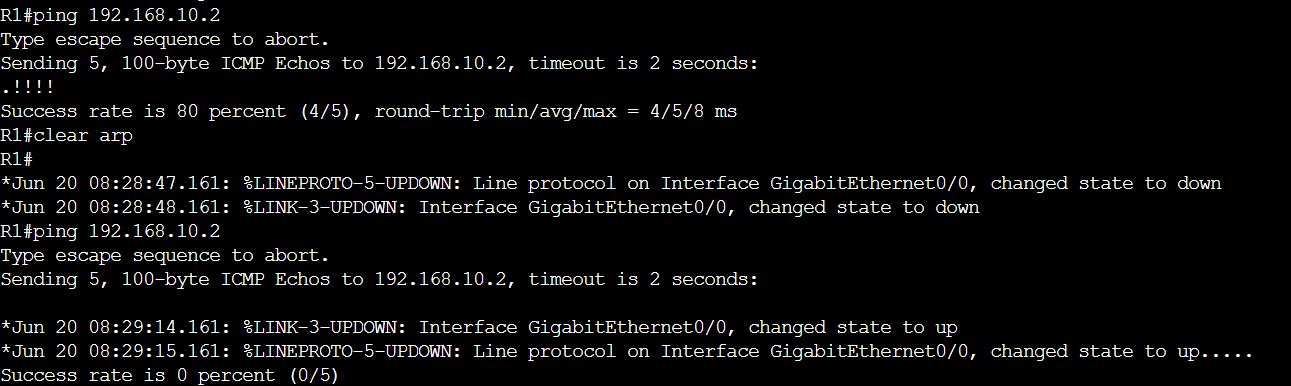
This configuration should drop anything destined to PC7’s MAC, right? But this isn’t quite the case
PC2#ping 192.168.10.7 repeat 3
Type escape sequence to abort.
Sending 3, 100-byte ICMP Echos to 192.168.10.7, timeout is 2 seconds:
!!!
Success rate is 100 percent (3/3), round-trip min/avg/max = 6/9/15 ms
PC2#
A ping for example still works. The funny thing is that when I shutdown the interface between SW1 and PC7 and then re-enable it, the ping no longer works 
SW1(config)#interface G0/3
SW1(config-if)#shut
*Feb 12 12:24:43.143: %LINK-5-CHANGED: Interface GigabitEthernet0/3, changed state to administratively down
*Feb 12 12:24:44.143: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/3, changed state to down
SW1(config-if)#no shut
*Feb 12 12:24:47.963: %LINK-3-UPDOWN: Interface GigabitEthernet0/3, changed state to up
*Feb 12 12:24:48.963: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/3, changed state to up
PC2#ping 192.168.10.7 repeat 6
Type escape sequence to abort.
Sending 6, 100-byte ICMP Echos to 192.168.10.7, timeout is 2 seconds:
......
Success rate is 0 percent (0/6)
PC2#
If I then change the action on the entry number 10 to forward
SW1(config)#vlan access-map BLOCK_PC7 10
SW1(config-access-map)#action forward
PC2#ping 192.168.10.7 repeat 6
Type escape sequence to abort.
Sending 6, 100-byte ICMP Echos to 192.168.10.7, timeout is 2 seconds:
!!!!!!
Success rate is 100 percent (6/6), round-trip min/avg/max = 1/2/3 ms
PC2#
It works, which proves that the communication did not work because of the 10th entry  Which is exactly what I wanted. However, if I configure it to drop again.
Which is exactly what I wanted. However, if I configure it to drop again.
SW1(config)#vlan access-map BLOCK_PC7 10
SW1(config-access-map)#action forward
SW1(config-access-map)#action drop
PC2#ping 192.168.10.7 repeat 6
Type escape sequence to abort.
Sending 6, 100-byte ICMP Echos to 192.168.10.7, timeout is 2 seconds:
!!!!!!
Success rate is 100 percent (6/6), round-trip min/avg/max = 1/2/3 ms
PC2#
The ping still works  Is this a CML bug?
Is this a CML bug?
Thank you.
David