This topic is to discuss the following lesson:
Nice read , thank you Rene
I was looking for something like this…
Thanks
If different users want to set different passwords , how can we configure that?
Hi Sakeb,
You can do this on the radius server. In my example I only created one user account (Alice) but you can create an account for each user here.
Rene
Hi Rene,
I’m playing with an IE3000 switch SW version 15, and the command dot1x port-control auto does not exist, I have the following options:
ASW1(config-if)#dot1x ?
authenticator Configure authenticator parameters
credentials Credentials profile configuration
default Configure Dot1x with default values for this port
max-reauth-req Max No. of Reauthentication Attempts
max-req Max No. of Retries
max-start Max No. of EAPOL-Start requests
pae Set 802.1x interface pae type
supplicant Configure supplicant parameters
timeout Various Timeouts
I tried default, but I cannot see the port go down
Groeten,
Hans.
Hi Hans,
Which IOS version are you running? I would expect this device to support all 802.1x commands.
Rene
hi rene I’ve downloaded electron server but i’m unable to get hold of the 30 key everytime I click on the link it takes me to a site that has nothing to do with the server do you know how to get hold of the 30 key thanks as I`m trying to get ready for my switch exam and I don’t want to leave any stone unturned
Hmm what exactly do you mean with the “30 key”?
Elektron was a great and simple Radius server but it seems they are out of business.
Daloradius is a good alternative btw.
Hi Hans
You need to type ‘dot1x pae authenticator’ instead- it enables 802.1X authentication on the port with default parameters
Hi Rene !
What it’s means SwitchA(config)#aaa authentication dot1x default group radius
What is the default group ?
Ori,
The term “default” does not reference the term “group” (so the two are unrelated). Instead, “Default” means “use the default dot1x settings for this particular port.”
The term “group” is associated with “radius”, so “group radius” is how you should think about it. This is what is called a method-list. In this context, it is saying, “use the radius server that has already been defined as the source of authentication.” You can have more than one method list–for example, if you wanted to use locally defined users on the switch, you could use the term “local” instead of “group radius”
–Andrew
Hello,
Can we change the time out period when 802.1x fails? for example- The client tries connecting for 802.1x but due to invalid credentials and request timeout. There has been a fallback mechanism to MAC authentication. But default timeout period is 30 seconds. Is there a way we can change this time period on cisco access switch in order to provide faster fallback?
Thank you
Parth
Hi Parth,
There are two things you can try to speed this up:
- dot1x timeout tx-period: this defines how often you send the Request Identity frame.
- dot1x max-reauth-req: this defines how often you will resend the Request identity frame.
By reducing the number of tries and the number of seconds in between attempts, you should be able to make it fallback faster to another form of authentication.
Rene
hi Rene,
Thank you for the clarifications. In the wired 802.1x design, we usually have fallback mechanism. If the user fails the 802.1x authentication multiple times than we can deploy the “AUTHENTICATION FAIL VLAN” and grant access to JUST internet rather than the Network resources. Because when user is sent into Authentication fail vlan, it gets EAP Success message from the authenticator. So the user assumes that it has the full access, but has only internet? This will continue until the re-authentication timer expires and user can have another chance to do 802.1x.
My question is-
The user will be confuse to not see the access to internal network resources but rather only internet usage. Is there a way where we can remove this confusion or allow the user to have a better experience while using the resources?
Thank you,
Parth
Hi Parth,
If you use fallback then I think it will be difficult to notify the user somehow. After all, on their end the authentication looks “successful”.
Perhaps it would be an idea to intercept Internet traffic in the guest VLAN with a portal? At least you can then notify them that their access is restricted.
Rene
Hi Rene,
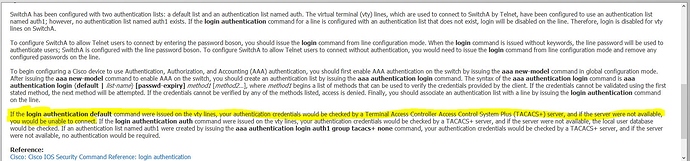
Can I configure both tacacs+ and radius on same device? My company uses Tacacs+ but a new client uses radius for their devices. I’m to find a way of having access sorted out for customer(radius) and msyelf?. Thanks in advance
Hi Tayo,
You can configure both RADIUS and TACACS+ on the device yes. You could use RADIUS for one thing and TACACS+ for another.
AFAIK, you can’t use one and the other as fallback or something. When you specify a group, you have to pick one of the two:
Switch(config)#aaa authentication login default group ?
WORD Server-group name
ldap Use list of all LDAP hosts.
radius Use list of all Radius hosts.
tacacs+ Use list of all Tacacs+ hosts.
You could however create one authentication list for TACACS+ and another one for RADIUS and use each for different purposes.
Rene
First off if I post this in wrong place let me know and I will move the question to better forum area.
I am studying AAA Authentication. I keep hearing it stressed to be aware that its best practice to put “local” on the end of your lines in case your tacacs server or radius server goes down.
For example I setup switch and AAA Server and PC in Boson Simulator to play with and test:
username brian password brian
!
aaa new-model
aaa authentication login auth group tacacs+ local
tacacs-server host 192.168.1.3
!
line con 0
line aux 0
line vty 0 4
login
!
I created a tacacs+ server and added the user auth and created a password for him on the boson.
When I try to connect with the config above it asks for password and then gives login invalid.
So if I change the config for VTY to the following:
line vty 0 4
login authentication auth
It will connect using the authenticaton from the tacacs server and use that password so successful.
So now I wanted to test the “local” thing on the end right? I mean that’s best practices so its suppose to be there in case the tacacs server goes down. So I go into the interface that connects to the tacacs server (fast0/1) and shutdown.
I then try to connect with the Tacacs server down and it does not let me connect via “local” as I was led to belive but instead says:
Trying 192.168.1.1 ...
% Destination unreachable; gateway or host down
c:>
so I cannot telnet if this had not been a test situation I would have been in big trouble with a remote switch or router and not able to reach it.
the AAA only works it seems if you set it up under VTY or Console ect… but the “local” backup command does not seem to work.
I know I can make it use telnet use local by telling it to and using login and a password or using login local but if I do that then that defeats purpose of having local on end of the AAA tacacs command.
I also did something like vty 0 2 and gave that login authentication auth and then vty 3-4 login authentication local. so if vty 0 2 did not work I could get in on vty 3-4.
That is not what they are talking about is it because I could do same thing without adding local to the end of the tacacs command.
Here is some documentation from an exam practice test:
now their lines of text was a bit different from what I was practicing up in my custom lab. they had:
aaa authentication login auth group tacacs+ local
aaa authentication login default group tacacs+
would love some help understanding this so it is actually feasible to use.
Thanks!
-=---------------------------------------------------EDIT::::::::::
Ok I set this up on VIRL and it works… so the Boson simulator software is great for labs but you cannot deviate and go experimenting.
on my cisco VIRL lab I added the following syntax:
switchA#show run
Building configuration…
*Jul 4 00:27:09.870: %SYS-5-CONFIG_I: Configured from console by console
Current configuration : 2798 bytes
!
! Last configuration change at 00:27:09 UTC Tue Jul 4 2017
!
version 15.2
!
!
username brian password 0 brian
aaa new-model
!
!
aaa authentication login default group tacacs+ local
line con 0
line aux 0
line vty 0 4
!
!
end
note: I did not add anything to the line vty 0 4 it did not allow for it but I didn’t have to. I was able to telnet from my hostA to Switch A and it asked for username and password and I entered the local username and password and it worked!
To test this I removed the local from the end of syntax:
!
!
username brian password 0 brian
aaa new-model
!
!
aaa authentication login default group tacacs+
!
!
!
this time it gave me error and would not let me:
HostA#telnet 192.168.1.2
Trying 192.168.1.2 … Open
% Authentication failed
% Authentication failed
% Authentication failed
[Connection to 192.168.1.2 closed by foreign host]
HostA#
I also tested this with “enable” and the “line” instead of “local” and it used the enable, and the line password and worked fine as well. =)
So it is working as intended the only difference is I don’t have to add the line VTY 0 4 commands they don’t exist on my VIRL switch. I don’t know if that’s because the Cisco VIRL is using a newer IOS than the one emulated in the BOSON software or something else but it does seem to be working as I would understand it to.
I love the boson software for pre configured labs but not for experimenting, have to create a cisco VIRL test lab for that. The reason I like the boson is its fast and easy but in the end its not the real stuff so you cannot go deviating much on it.
Hi Brian,
Good to hear you figured it out. The output of your Boson simulator was indeed that it was unable to connect so this didn’t have anything to do with your AAA configuration ![]() Boson is nice to practice commands but it’s only a simulator so you can’t really test things.
Boson is nice to practice commands but it’s only a simulator so you can’t really test things.
If you don’t add anything to your VTY line(s) then it will use the default AAA group. If you want to use RADIUS / TACACS+ authentication for some things but not for your VTY lines, then you can also create a second group and use that for the VTY lines. Something like this:
SW1(config)#aaa authentication login VTY local
SW1(config)#line vty 0 4
SW1(config-line)#login authentication VTY
Also, when you are messing around with AAA…I like to enable debug AAA authentication:
SW1#debug aaa authentication
AAA Authentication debugging is on
It will show you when it’s trying to reach the TACACS+ server and such, it’s pretty useful.