Oh I saw the earlier post. My bad… ![]()
when we configure the radius server, can we just write [SW1(config)#radius-server host 192.168.1.101 key radiuspass] ? without specifying port numbers? also we write the default value of acct-port which is 1646 (So, it is possible to not mention the acct-port in the command, right?). What is the auth-port 1812?
is it because of the radius server (Elektron)? meaning, there is a specific port number for each server? if we use another server then, different port number need to be used?
Hello Mohanad
You can indeed issue the command without the port numbers if you choose to. By default, the auth-port port number is 1645 and by default, the acct-port port number is 1646. In this specific lesson, Rene had to specify the auth-port since it was different from the default. He didn’t need to specify the acct-port since it is the default, however, he chose to include it for completeness.
I hope this has been helpful!
Laz
Hello,
please can you give me a help for how can i configure the switch WS-C2960L-24PS-LL.
some comand are different from your swtich dimostration.
Thanks
Hello Valerio
It could be that some of the commands have changed since the writing of the lesson. Can you share with us the version of the IOS in the device you are using and which commands you find are not working? Let us know and we’ll look into it further…
Looking forward to hearing back from you!
Laz
Hello Lazaros,
C2960L Software (C2960L-UNIVERSALK9-M), Version 15.2(6)E, when i enable aaa new-model then in config i cannot make the comand: radius-server host ?
% Unrecognized command.
the only options that i have are :
radius-server ?
accounting Accounting information configuration
attribute Customize selected radius attributes
authorization Authorization processing information
backoff Retry backoff pattern(Default is retransmits with constant delay)
cache AAA auth cache default server group
challenge-noecho Data echoing to screen is disabled during Access-Challenge
configure-nas Attempt to upload static routes and IP pools at startup
dead-criteria Set the criteria used to decide when a radius server is marked dead
deadtime Time to stop using a server that doesn't respond
directed-request Allow user to specify radius server to use with `@server'
domain-stripping Strip the domain from the username
load-balance Radius load-balancing options.
optional-passwords The first RADIUS request can be made without requesting a password
retransmit Specify the number of retries to active server
retry Specify how the next packet is sent after timeout.
source-ports source ports used for sending out RADIUS requests
throttle Throttle requests to radius server
timeout Time to wait for a RADIUS server to reply
transaction Specify per-transaction parameters
unique-ident Higher order bits of Acct-Session-Id
vsa Vendor specific attribute configuration
Hello Valerio
Starting from IOS 15.4(2)S, the command has changed. As shown in this Cisco IOS command reference, the command is now radius server <name>.
For example:
Router(config)# aaa new-model
Router(config)# radius server
Router(config-radius-server)# address ipv4 10.0.0.1 acct-port 1813 auth-port 1812
Router(config-radius-server)# key mykey
More info on this command can be found in this command line reference:
I hope this has been helpful!
Laz
Hi community !
AAA Configuration on Cisco Switch : Section 2: Configuration
I could not find **dot1x ** cli config under switchport interface. I am using
Cisco IOS Software, vios_l2 Software (vios_l2-ADVENTERPRISEK9-M), Version 15.2
Please inform the which version of the switch has interface cli option for dot1x
Hello Raghu
I’ve just logged in to CML and found that I have Cisco IOS Software, vios_l2 Software (vios_l2-ADVENTERPRISEK9-M), Version 15.2 same as you, and I have the dot1x optoin available. Did you remember to start off by issuing the aaa new-model command?
Let us know!
I hope this has been helpful!
Laz
HI Rene a bit of an nooby question but how did you figure out the port numbers for
SW1(config)#radius-server host 192.168.1.101 auth-port 1812 acct-port 1646 key radiuspass
is this set in stone? as in always the same? or is it given to me some where and I just don’t know where to find it?
Hello Brian.
Modern RADIUS implementations use UDP port 1812 for authentication and authorization, and UDP 1813 for accounting. Older implementations used 1645 and 1646.
Here’s what freeRADIUS uses
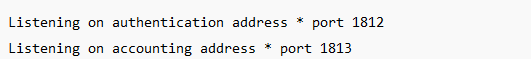
So what you would do is specify the ports as 1812 for auth/autz and 1813 for accounting so the device knows which ports to use.

The ports you specify here should be the same as the ones you’re using on the RADIUS server. Most RADIUS servers should use these ports by default but just like with anything else, you always have the option to change them ![]()
So in summary, RADIUS implementations will typically use 1812/1813 these days, so you can specify these ports in the command. However, these ports can be changed and if you’re unsure what ports is the RADIUS server using, you’re always free to log into it and check. What’s important here is having the ports specified in the RADIUS configuration and on the RADIUS server the same.
David
Is there any difference when we used
aaa authorization exec default group radius local
compared to
aaa authorization exec default radius local
Does this do the same thing? What is the point of the group command if I can specify it without it?
radius-server host 192.168.1.101 auth-port 1812 acct-port 1646 key radiuspass
why i cannot type the above command any switch under any switch ?
Hello Cameron
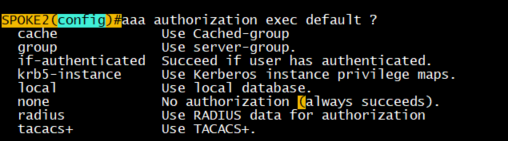
First of all, it seems that I am unable to issue the aaa authorization exec default radius local command on my CML.
Router(config)#aaa authorization exec default ?
cache Use Cached-group
group Use server-group.
if-authenticated Succeed if user has authenticated.
krb5-instance Use Kerberos instance privilege maps.
local Use local database.
none No authorization (always succeeds).
Router(config)#aaa authorization exec default
I am running the following:
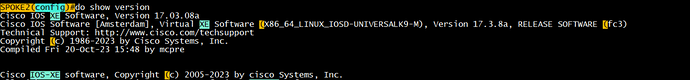
Cisco IOS Software, IOSv Software (VIOS-ADVENTERPRISEK9-M), Version 15.9(3)M6, RELEASE SOFTWARE (fc1)
I also don’t see this syntax for the command as shown in the following Cisco command reference:
If however, on some IOS version this command is available, there is still a difference between these commands.
The use of the group radius keywords uses the list of all RADIUS servers for authorization as defined by the aaa group server radius command. If the group keyword is not used (and assuming this works on some other IOS version) then the single configured RADIUS server will be used.
Just to confirm, can you check to see that your setup does indeed support this command and let us know what IOS you’re using.
I hope this has been helpful!
Laz
Hi Laz,
Thank you for taking time and looking into this for me! I appreciate it. I am using IOS XE. See the screenshots below.
I thought that using the group command would first make it use the radius server that is configured then if not if you had a second way to authenticate/authorize it would use that, such as local for local credentials after.
I did this get this after I entered the command.
aaa authorization exec default radius local is a hidden command. Use of this command is not recommended/supported and will be removed in future.
I also was wondering a bit about the reverse-access command. I read the documentation and it seems it is only used for reverse telnet and that allows you to telnet to a device but then console into another device from the device that you telnetted into. Is that correct? Would that be configured on the device you are telnetting to or the one you originally telnetted from?
Hello Prasenjit
The radius-server host command has been deprecated in newer devices and OSes and it has been replaced with the following syntax:
radius server MY_SERVER
address ipv4 192.168.1.101 auth-port 1812 acct-port 1646
key radiuspass
Take a look at this Cisco command reference for more details:
I will let @ReneMolenaar know to consider updating the lesson.
I hope this has been helpful!
Laz
Hello Cameron
Thanks for letting us know the version you’re using.
That’s an interesting response. Cisco often has commands that are considered “hidden” because they are not documented in the standard command reference guides. These commands may still be usable to ensure backward compatibility with legacy IOS versions, but are not recommended because they could be deprecated or removed in future versions of the IOS software. The warning you mentioned suggests that Cisco plans to remove or stop supporting this command in the future.
The specific command that you had shared in your post was this one:
aaa authorization exec default group radius local
The group keyword indicates that the methods that follow will be used for authorization. In this case, radius specifies that the device should first attempt to authorize the user through a RADIUS server group. If the RADIUS server is not available or does not respond, the device will fall back to using the local user database, that is, user credentials and authorization settings configured manually on the device itself.
Your understanding of the reverse-access command is generally correct. The reverse-access command is used to facilitate “reverse telnet,” which is a method that allows you to telnet into a network device (like a router or a terminal server) and then connect to the console port of another device connected to that first device. This is particularly useful for managing and accessing devices that do not have direct network connectivity.
The reverse-access command is configured on the device that you initially telnet into (often referred to as a terminal server or access server). This device has asynchronous serial lines (often referred to as “lines” in Cisco terminology) that are connected to the console ports of other devices.
I hope this has been helpful!
Laz
Hi Lazarus,
Thank you for taking the time for looking into this for me. I understand all of it a lot better now. You are always great at understanding and always have great research and knowledge!
Hello Cameron
Thanks for your kind words, it’s my pleasure!!
Laz