This topic is to discuss the following lesson:
Hi Rene,
Very Good Lesson about ARP poisoning and am waiting for DAI.
In real network, can host accepts all the ARP reply from any other host (updates arp table ) without generating the ARP broadcast request for that particular host?
It is very basic question still curious to understand.
Regards,
SV
Hi SV,
You are welcome, the DAI lesson is now online:
Hosts will accept the ARP reply, even if they didn’t send the ARP request.
Rene
Hi Rene,
Thanks for your all valuable articles , I want to do in the Lab environment but at this moment i don’t have any physical Router and switch , is it possible to do in the GNS3 or any other emulation/simulations software where i can do your all of lab.
Thanks,
Arif
Both GNS3 (free) and VIRL (paid) can be used for almost all simulations. Some minor topics, like Bi-Direction Forwarding Detection, Unidirectional Link Detection, and a few more, don’t work well (BFD will actually crash GNS3!).
GNS3 is easier to use, and less complicated to setup. The downsides are you have to supply your own IOS images, and GNS3’s support for switching is marginal at best. If you want to practice topics related to routing I would recommend it.
VIRL requires a paid yearly subscription, as well as access to 3rd party emulator software (VMWare Workstation or VMWare ESXi). VIRL is resource intensive (you will need lots of RAM and CPU power), but it comes packaged with all the latest IOS versions. VIRL is a bit complicated to setup (although the instructions are good), and it is vastly superior to GNS3 on topics of layer 2 or switching.
Thanks a lot, Rene, you are amazing !
HI Laz,
I am unable to understand how packet is going though attacker and reaches to the router and Host b/c suppose if host want to communicate with router it will send arp request and attacker will capture it against that attacker will send fake arp reply so packet is not reaching to the router stucked only b/w host and attacker same case when router send arp request the communication will be limited to Router and Attacker then how can be say communication happening though attacker PC and reaches to host ,router for both cases?
Hello Pradyumna
An attacker that wants to establish a MITM attack must have some application installed that is configured to relay all the traffic from the victim’s host to the internet and back. Such an application is designed to do this for the purpose of attacking in this manner. The original ARP request will be replied to by the attacker, and the attacker will act as a forwarder sending an ARP request to the real gateway and will forward everything it receives. The same happens in the other direction as well.
I hope this has been helpful!
Laz
actually mean that while sender send arp request to the destination host meanwhile somewhere attacker catch the packet and change the packet like will it’s own mac address as source address and ip address will be same ( actual sender ip) forward the packet to the destination host and when destination host reply with it’s own mac against destination ip (own ip in destination ip address field) again attacker catch the packet and change destination mac with it’s own mac and rest will be same. am i right?
Hello Pradyumna
I’m not sure I understand your question. When the sender sends an ARP request for the IP address of the gateway, the attacker host will reply to that request with its own MAC address. It doesn’t matter what its own IP address is. From that moment on, the original sender will now send all packets to the MAC address of the attacker. Does that answer your inquiry? If not, please clarify.
I hope this has been helpful!
Laz
Actually Laz I want to say that we know sender sends arp request for the destination host and somewhere is a attacker as well who will send fake arp reply in place of actual destination host so I want to know after sending arp request by sender, will it first catch by attacker, if yes then how request reaches to the original destination host and when attacker send arp reply to sender, does attacker send fake reply to sender and forward the arp request to the destination simultaneously and is this forwarded arp request from attacker or sender, and please also mention the address being used by devices(sender/attacker/receiver) when they send/forward arp reply/request packet.
You can say I just want to know how this whole process happening b/w source host, destination host and attacker, when and who will send arp request/reply to whom.
Hello Pradyumna
The lesson shows this process in detail. I suggest you apply the lab and you will have most of your questions answered. However, I will say this. The attacker does not need to wait for an ARP request from the sender in order to send an ARP reply and become the MITM. The Ettercap program will begin sending ARP replies whenever it likes to change the ARP entries in both the host and R1 to point to itself. It can do this at any time.
I hope this has been helpful.
Laz
GNS3 version 2.2.48.1
Kali version: Kali-Linux version 2024.2 VMware AMD 64
Router: IOSV
Switch: IOSVL2
OS: Windows 11
VMware version: 17.5 pro
Lab source: https://networklessons.com/cisco/ccna-200-301/arp-poisoning
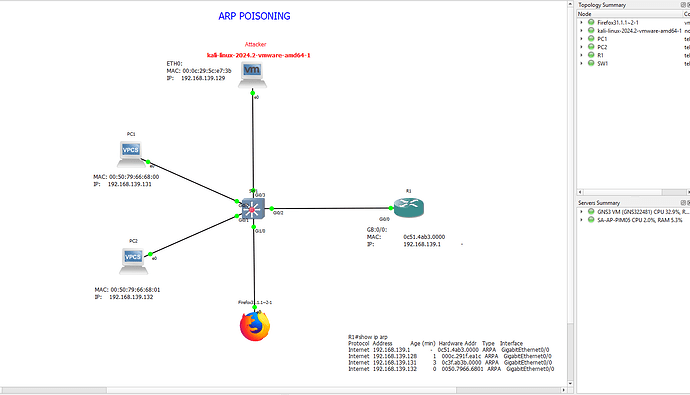
Lab topology:
Steps:
1. Download Kali-Linux-24-2-Vmware AMD 64
- Extract package and open the package in VMware
- Start GNS3
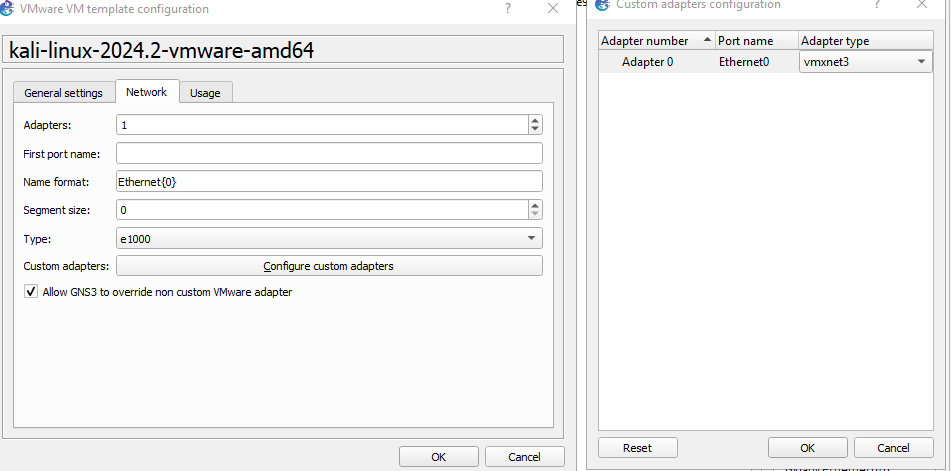
- Import Kali-Linux via menu Edit-Preferences- New → vmware-new (template)
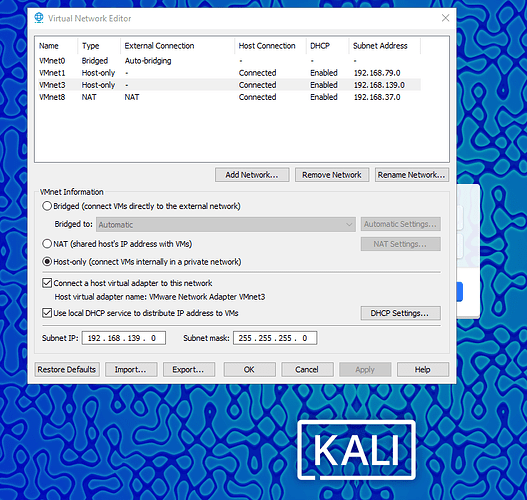
- Open Virtual network Editor in Vmware, select Change Settings
- Choose Add Network host-only VMnet 3
- Open DHCP Settings and make a note of the Scope
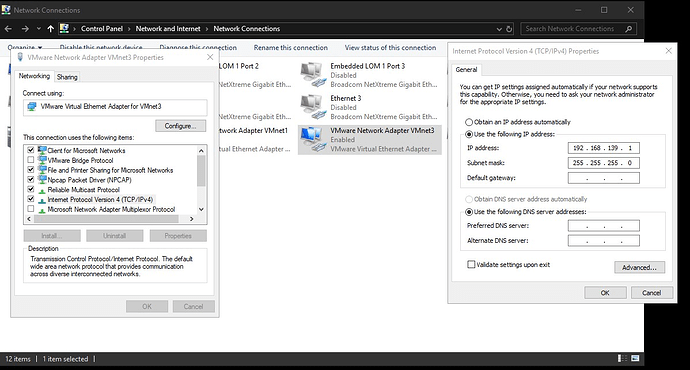
- Verify if the VMnet 3 adapter is installed in windows 11 (network adapter)
- Go to Vmware and Select tab kali-linux-2024-2-vmware in the Vmware console
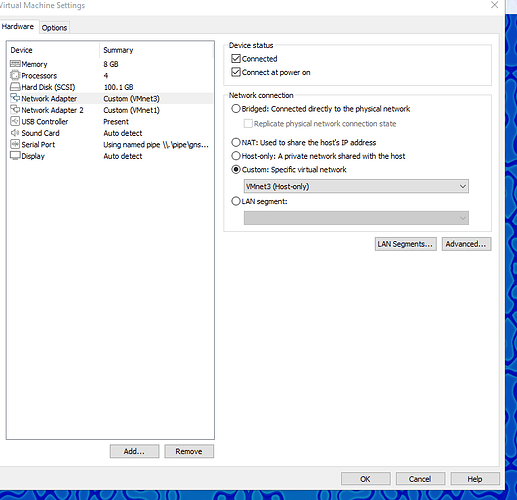
- Choose Edit virtual machine setting and add a new network adapter
- Select Custom: Specif virtual network en select VMnet3 (host-only) in de dropdown list
- Pull the Kali-Linux template into the GNS3 console and select from the drop-down menu ‘configure’, select tab network and custom adapter
- Select Vmxnet3 from the drop-down list.
- Check Allow GNS3 to override
- Save all settings and reboot windows 11.
- Restart GNS3 and complete the topology
- Start the lab and complete the configurations (R1 fixed IP address G 0/0)
- Select Kali in VMware environment
- Log in Kali/Kali
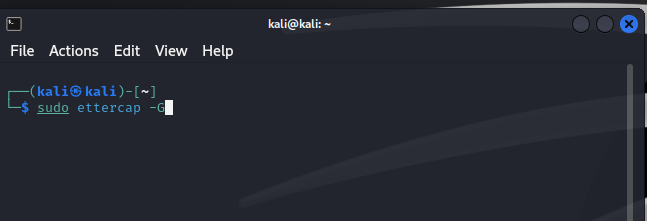
- Update Kali via Terminal shell (sudo apt update –y , sudo apt upgrade –y). If you skip the update Ettercap will not function.
- In Terminal add network-tools with the command sudo apt install network-tools
- Type ifconfig and select interface with ip scope address of VMNET3. Make a note of the MAC address
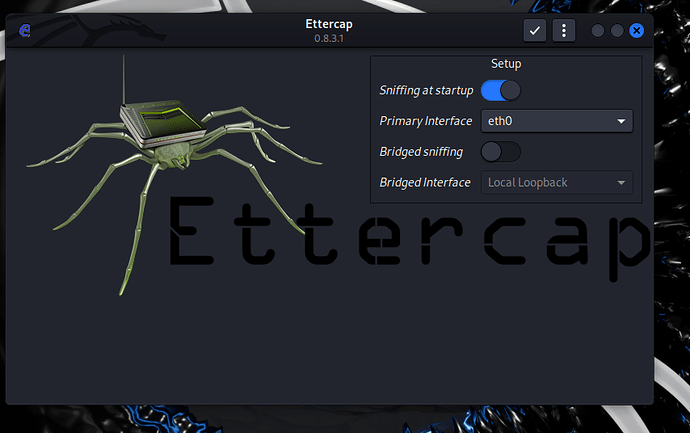
- Start Ettercap Graphical from the terminal as sudo (view is different from network lessons)
- Select ETH0
- Put your mouse on the tree dots right up
- Enter the subnet mask 255.255.255.0
- Do not select the option Bridged sniffing.
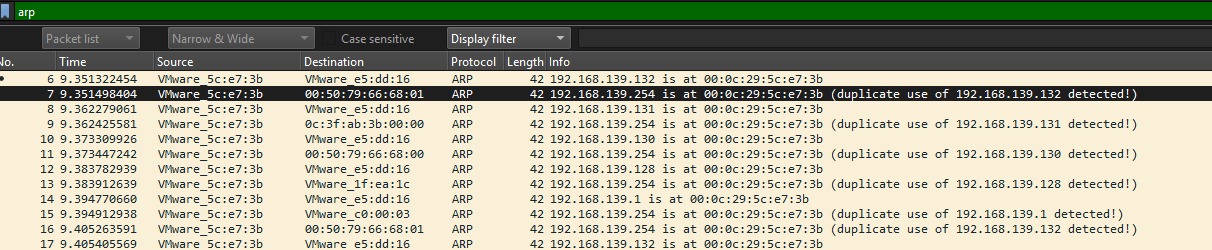
- Start Wireshark in Kali and select capture on ETH interface and start the capture
- Click on the checkbox and Ettercap starts with unified sniffing.
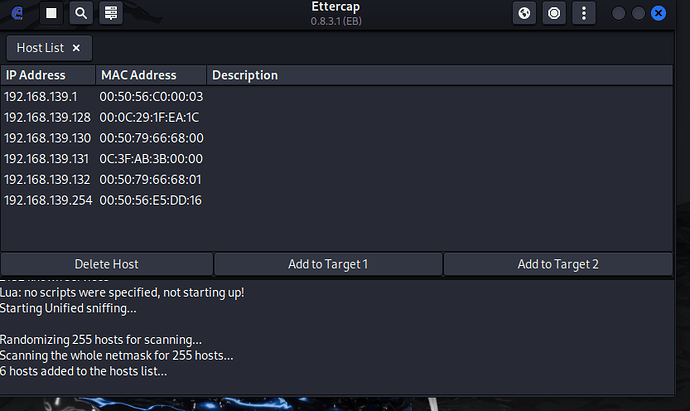
- Click on scan for hosts
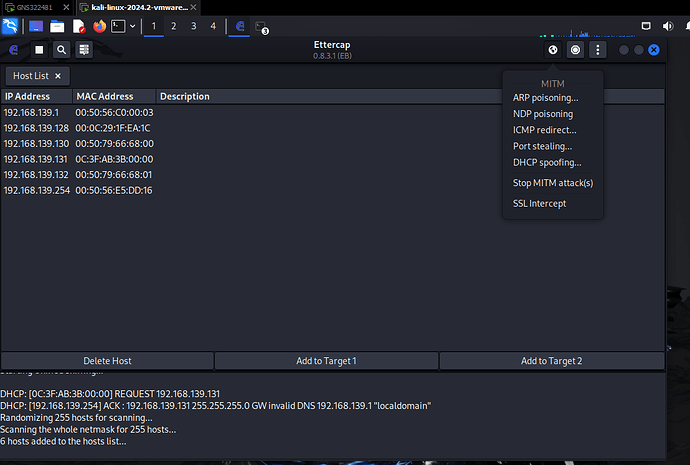
- Select ARP Poisoning
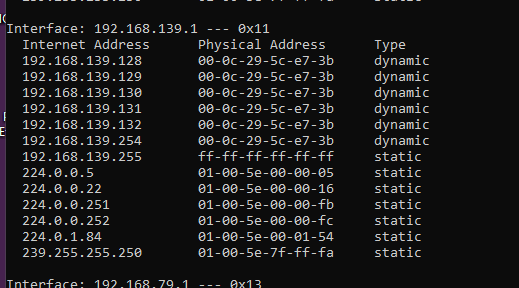
After the poisoning all MAC address have been changed to the MAC address of the Kali Machine.
Hello Michel
Thanks for sharing your lab procedure with us!
Laz
My Pleasure. The lab of Rene on this subject is really brilliant, but I missed the connection with Kali Linux.
Best Regards,
Michel