Dear Rene & all,
I would like to know what is the best practice to place the proxy server in the network. I am having difficulties to decide where to place the proxy server (Kerio Control).
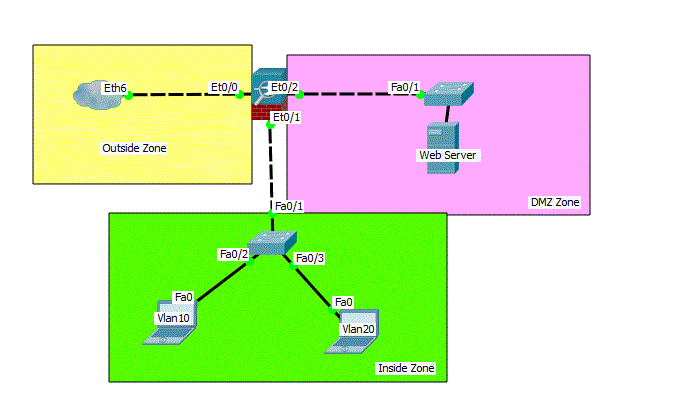
My current design is as attached. I want the traffics from Vlan 10 & 20 to go through proxy server where I am going to implement the content blocking & ACLs.
Option 1
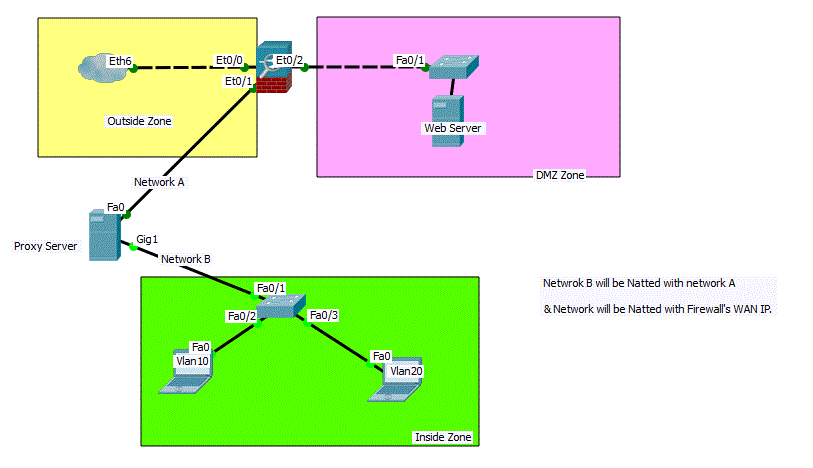
I am placing proxy server in between the firewall and internal switch. The proxy server will have two NIC cards, outside (Network A) & inside (Network B). So, the vlan 10 & 20 (internal) will be routed on proxy server inside and their gateway will be on proxy server. Network B will be natted with Network A and again Network A will be natted with wan ip address on firewall if the traffics is destined for internet. Is it normal practice ? Please suggest me.
Option 2 _1
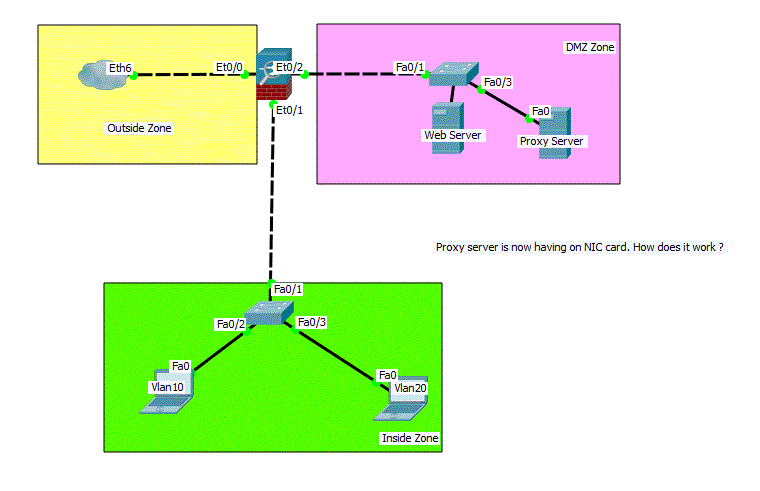
I am placing proxy server in DMZ zone. So, the proxy server is only having one NIC, I am not sure how does it work in this case. I believe my proxy (Kerio Control) can’t achieve this design. I must have two NICs if I want to use Kerio proxy.
Option2_2
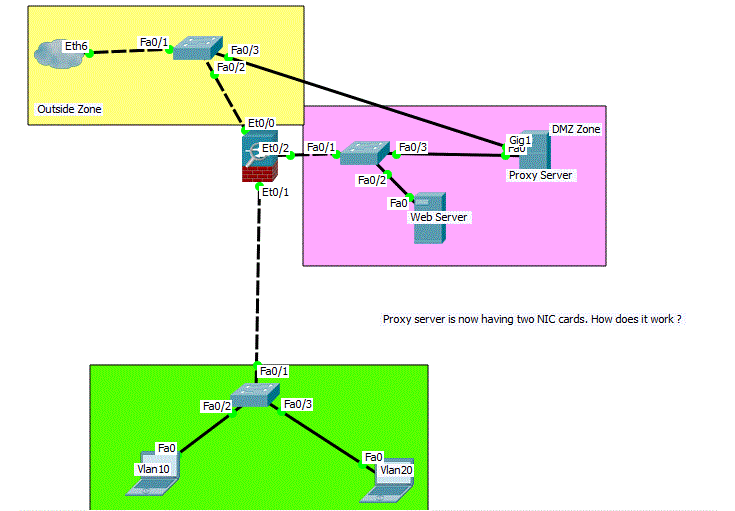
This might be silly design having two NICs on proxy server which is located in DMZ zone.  I believe I could connect back to the outside zone on ASA instead of having a additional switch in outside zone. The logic is still the same so, please bare with me on this.
I believe I could connect back to the outside zone on ASA instead of having a additional switch in outside zone. The logic is still the same so, please bare with me on this.
Please suggest me which option is the best and also feel free to recommend me if you have other options. Thank you so much to you all.
Best Regards,
Ronnie
Hi Ronie,
I’m not really familiar with Kerio Control, it looks more like a firewall than a proxy server if I’m correct?
It really depends on the product where you should place it.
About your options:
-
Placing Kerio control between your switch/firewall could be a good option but you shouldn’t configure NAT on it. Double NAT is always a bad idea. Make sure only your firewall with the public IP is doing NAT.
-
It depends on how Kerio Control works. With a “regular” proxy server you would place it in the DMZ and then you can configure your applications/computers to use the proxy server instead.
-
Only if you put it in your traffic path then you should need two interfaces (in and out). Unless you need a second interface for failover/load balancing.
Rene
Hi Rene,
In short, I would like to know do we always need two NICs (in & out) on a proxy server ? You have done one tutorial WCCP with a unix proxy, how many NICs were you using on your unix proxy ?
If I place my proxy server in DMZ, how many NICs do I need ? While knowing one NIC to connect to DMZ switch and how about another one ?
Thank you so much for your guidance in advance.
Best Regards,
Ronie
Hi Ronie,
It depends on the product. In my example with the squid server, it would be placed in the DMZ and it only has one interface. You can then configure your computers (or Cisco router in my example) to forward traffic to the squid server. Squid is a “pure” proxy server, it does caching but that’s about it.
Kerio control looks more like a firewall. It does packet inspection, NAT, etc. In that case, it should probably be placed inline so you need two interfaces.
Rene
Hi Rene,
Thank you so much for your reply and appreciate it. It makes sense to me now.
I happened to check your tutorial on GNS3vault about the SLB. I was searching online but I couldn’t find it. Can you please tell me if the load balancing method is persistence (meaning to say, one session is maintained to one particular server till it is over else, even a single refresh could redirect the traffic to another server).
Best Regards,
Ronnie
Hi Ronnie,
NP!
About SLB, it has been awhile since I configured it. It does have support for “sticky connections” which ensures that (new) connections from a host IP address will always be assigned to the same server.
Rene
![]() I believe I could connect back to the outside zone on ASA instead of having a additional switch in outside zone. The logic is still the same so, please bare with me on this.
I believe I could connect back to the outside zone on ASA instead of having a additional switch in outside zone. The logic is still the same so, please bare with me on this.