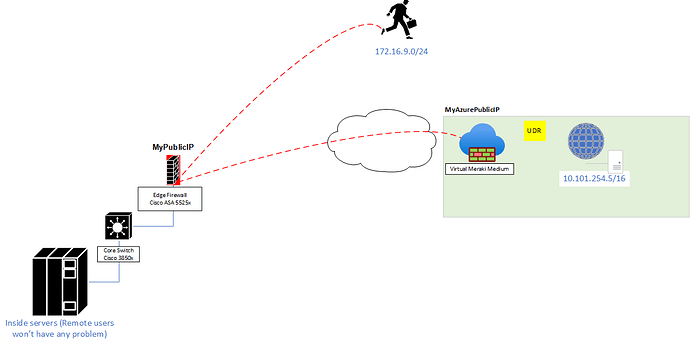
Hello everyone, this is my first post here, hopefully is just something I’m not able to see but; I have this requirement to enable Anyconnect users to access certain resources thru an existing VPN tunnel (a pretty simple hairpin configuration as per Cisco ASA 9.8 NAT reference guide). However traffic from remote users is not traversing the VPN tunnel (Is hitting the hairpin NAT statement) and traffic coming to the remote users from the far end resource is hitting the VPN tunnel, would you mind reviewing my sanitized configuration (topology enclosed).
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface are in the config.
Sanitized config
ASA-5525x(config)# show run
ASA Version 9.8(2)
!
hostname ASA-5525x
ip local pool VPN_POOL 172.16.9.1-172.16.9.240 mask 255.255.255.0
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address MyPublicIP
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 172.16.0.2 255.255.255.0
!
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network Azure_Network
description Azure virtual network
subnet 10.101.0.0 255.255.0.0
object network NETWORK_OBJ_172.16.9.0_24
subnet 172.16.9.0 255.255.255.0
object-group network Azure_Virtual_Network
description Azure virtual network
network-object 10.101.0.0 255.255.0.0
object-group network On_Prem_Network
description On_Prem_Network
network-object 172.16.0.0 255.255.0.0
access-list outside_access_in extended permit ip object-group Azure_Virtual_Network object-group On_Prem_Network
access-list outside_access_in extended permit ip object-group On_Prem_Network object-group Azure_Virtual_Network
access-list Split_Tunnel_List remark Azure_Servers
access-list Split_Tunnel_List standard permit 10.101.0.0 255.255.0.0
access-list outside_cryptomap_24 extended permit ip object NETWORK_OBJ_172.16.9.0_24 object Azure_Network
access-list outside_cryptomap_24 extended permit ip object Azure_Network object NETWORK_OBJ_172.16.9.0_24
nat (outside,outside) 1 source static NETWORK_OBJ_172.16.9.0_24 NETWORK_OBJ_172.16.9.0_24 destination static Azure_Network Azure_Network no-proxy-arp route-lookup
crypto ipsec ikev1 transform-set ESP-3DES-MD5_T esp-3des esp-md5-hmac
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 24 match address outside_cryptomap_24
crypto map outside_map 24 set peer MyAzurePublicIP
crypto map outside_map 24 set ikev1 transform-set ESP-3DES-MD5_T
crypto map outside_map 24 set security-association lifetime kilobytes unlimited
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ikev1 policy 120
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
webvpn
enable outside
enable inside
anyconnect image disk0:/anyconnect-win-3.1.14018-k9.pkg 1
anyconnect image disk0:/anyconnect-macos-4.7.02036-webdeploy-k9.pkg 2
anyconnect profiles USERS_RemoteAccess disk0:/users_remoteaccess.xml
anyconnect profiles USERS_Test disk0:/users_test.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy GrpPolicy_MyAzurePublicIP internal
group-policy GrpPolicy_MyAzurePublicIP attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_VPN_Users internal
group-policy GroupPolicy_VPN_Users attributes
wins-server none
dns-server value x.x.x.x
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Split_Tunnel_List
default-domain value mydomain.com
webvpn
anyconnect profiles value USERS_Test type user
group-policy GroupPolicy_VPN_RemoteAccess internal
group-policy GroupPolicy_VPN_RemoteAccess attributes
wins-server none
dns-server value x.x.x.x
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Split_Tunnel_List
default-domain value mydomain.com
split-tunnel-all-dns disable
webvpn
anyconnect profiles value USERS_RemoteAccess type user
tunnel-group DefaultRAGroup general-attributes
authentication-server-group LDAPSERVERS
tunnel-group VPN_Users type remote-access
tunnel-group VPN_Users general-attributes
address-pool VPN_POOL
authentication-server-group LDAPSERVERS
default-group-policy GroupPolicy_VPN_Users
tunnel-group VPN_Users webvpn-attributes
group-alias VPN_Users enable
tunnel-group MyAzurePublicIP type ipsec-l2l
tunnel-group MyAzurePublicIP general-attributes
default-group-policy GrpPolicy_MyAzurePublicIP
tunnel-group MyAzurePublicIP ipsec-attributes
ikev1 pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
class-map firepower_class_map
match access-list firepower
class-map INSIDE-Class
match access-list INSIDE_mpc_1
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect rsh
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
class firepower_class_map
sfr fail-open
class class-default
user-statistics accounting
policy-map DMI_Policy
class INSIDE-Class
police input 50000000 25000
police output 25000000 12500
!
service-policy global_policy global
service-policy DMI_Policy interface inside
Output of show nat translation details
1 (outside) to (outside) source static NETWORK_OBJ_172.16.9.0_24 NETWORK_OBJ_172.16.9.0_24 destination static Azure_Network Azure_Network no-proxy-arp route-lookup
translate_hits = 11722, untranslate_hits = 11722
Output of show show cap asp detail | i 172.16.0.9.100 (a remote user going to remote resource)
172.16.9.100 > 10.101.254.5: icmp: echo request (ttl 128, id 5685) Drop-reason: (acl-drop) Flow is denied by configured rule
10.101.254.5 > 172.16.9.100: icmp: echo request (ttl 127, id 8896) Drop-reason: (acl-drop) Flow is denied by configured rule
172.16.9.100 > 10.101.254.5: icmp: echo request (ttl 128, id 5686) Drop-reason: (acl-drop) Flow is denied by configured rule
10.101.254.5 > 172.16.9.100: icmp: echo request (ttl 127, id 8897) Drop-reason: (acl-drop) Flow is denied by configured rule
172.16.9.100 > 10.101.254.5: icmp: echo request (ttl 128, id 5687) Drop-reason: (acl-drop) Flow is denied by configured rule
10.101.254.5 > 172.16.9.100: icmp: echo request (ttl 127, id 8898) Drop-reason: (acl-drop) Flow is denied by configured rule
172.16.9.100 > 10.101.254.5: icmp: echo request (ttl 128, id 5688) Drop-reason: (acl-drop) Flow is denied by configured rule
10.101.254.5 > 172.16.9.100: icmp: echo request (ttl 127, id 8899) Drop-reason: (acl-drop) Flow is denied by configured rule
172.16.9.100 > 10.101.254.5: icmp: echo request (ttl 128, id 5689) Drop-reason: (acl-drop) Flow is denied by configured rule
10.101.254.5 > 172.16.9.100: icmp: echo request (ttl 127, id 8900) Drop-reason: (acl-drop) Flow is denied by configured rule
172.16.9.100 > 10.101.254.5: icmp: echo request (ttl 128, id 5690) Drop-reason: (acl-drop) Flow is denied by configured rule
10.101.254.5 > 172.16.9.100: icmp: echo request (ttl 127, id 8901) Drop-reason: (acl-drop) Flow is denied by configured rule
172.16.9.100 > 10.101.254.5: icmp: echo request (ttl 128, id 5691) Drop-reason: (acl-drop) Flow is denied by configured rule
10.101.254.5 > 172.16.9.100: icmp: echo request (ttl 127, id 8902) Drop-reason: (acl-drop) Flow is denied by configured rule
172.16.9.100 > 10.101.254.5: icmp: echo request (ttl 128, id 5692) Drop-reason: (acl-drop) Flow is denied by configured rule
10.101.254.5 > 172.16.9.100: icmp: echo request (ttl 127, id 8903) Drop-reason: (acl-drop) Flow is denied by configured rule
172.16.9.100 > 10.101.254.5: icmp: echo request (ttl 128, id 5693) Drop-reason: (acl-drop) Flow is denied by configured rule
10.101.254.5 > 172.16.9.100: icmp: echo request (ttl 127, id 8904) Drop-reason: (acl-drop) Flow is denied by configured rule
I’ve tried setting an acl to the outside interface as out, but results were the same (heck even LAN users were impacted) this is the statement
access-list outside_access_out extended permit ip object Azure_Network object NETWORK_OBJ_172.16.9.0_24
access-list outside_access_out extended permit ip object NETWORK_OBJ_172.16.9.0_24 object Azure_Network
access-group outside_access_out out interface outside
Note: Please not that I’ve sanitized the config, I apologize if I removed any command continuity.