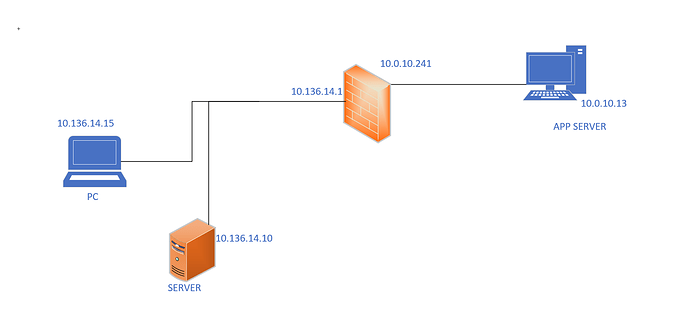
I have a perculiar problem with Cisco ASA that I have been trying to resolve for many days but I cannot even find the root cause. I have a network as seen in the diagram below. I cannot establish pings between these two LAN segments.
See output of the important parts of the Firewall Config realted to the configuration/operation of ICMP.
interface GigabitEthernet1/1
nameif OUTSIDE
security-level 0
ip address X.X.X.X 255.255.255.240
interface GigabitEthernet1/2.100
vlan 100
nameif ISIDE
security-level 100
ip address 10.136.14.1 255.255.254.0
interface GigabitEthernet1/2.804
vlan 804
nameif DMZ
security-level 90
ip address 10.0.10.241 255.255.255.0
object network PC
host 10.136.14.15
object service APP_SERVER_5050
service tcp source eq 5050
!
!
!
!
access-list LAN_access_in extended permit ip 10.0.10.0 255.255.255.0 host 10.136.14.15 log
access-list LAN_access_in extended permit ip 10.0.10.0 255.255.255.0 host 10.136.14.10 log
!
!
!
nat (INSIDE,DMZ) source static PC interface service any APP_SERVER_5050
!
!
access-group LAN1_access_in in interface DMZ
!
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
!
!
!
!
!
class inspection_default
inspect dns preset_dns_map
inspect icmp
!
service-policy global_policy global
The Firewall can reach the remote server.
Firewall# ping 10.0.10.13
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.10.13, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
However, this is what happens on the devices on the INSIDE
Server1:~$ ping 10.0.10.13
PING 10.0.10.13 (10.0.10.13) 56(84) bytes of data.
^C
--- 10.0.10.13 ping statistics ---
54 packets transmitted, 0 received, 100% packet loss, time 192ms
LAPTOP# ping 10.0.10.13
PING 10.0.10.13 (10.0.10.13) 56(84) bytes of data.
^C
--- 10.0.10.13 ping statistics ---
36 packets transmitted, 0 received, 100% packet loss, time 35000ms
But we know ICMP works because when we ping a remote device on the internet, we get a reply.
LAPTOP# ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=118 time=2.41 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=118 time=2.48 ms
64 bytes from 8.8.8.8: icmp_seq=3 ttl=118 time=2.40 ms
64 bytes from 8.8.8.8: icmp_seq=4 ttl=118 time=2.39 ms
64 bytes from 8.8.8.8: icmp_seq=5 ttl=118 time=2.43 ms
Server1:~$ ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=118 time=1.83 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=118 time=1.69 ms
64 bytes from 8.8.8.8: icmp_seq=3 ttl=118 time=1.84 ms
64 bytes from 8.8.8.8: icmp_seq=4 ttl=118 time=1.57 ms
64 bytes from 8.8.8.8: icmp_seq=5 ttl=118 time=1.65 ms
What is it I am missing and how can I make this work? I have replicated this with other firewall brands and I get ICMP replies on the LAN but not with Cisco ASA.