Hello Alberto
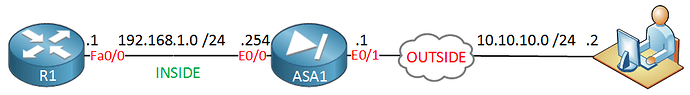
This is actually correct. This is what is called “Twice NAT” or “Identity NAT”. Take a look at the image of the network:
The ASA has NATing enabled, so any traffic going from INSIDE to OUTSIDE, or visa versa, will be NATed.
The VPN client on the OUTSIDE network is on the 10.10.10.0/24 subnet. When it connects via VPN, its connection is tunneled over this subnet, and the internal IP address it is provided is in the 192.168.10.0/24 subnet, which is configured in the VPN_POOL.
So the client sends encapsulated data to R1 over the tunnel. Outside IP header 10.10.10.0/24 subnet, inside IP header 192.168.10.0/24 subnet. Once it reaches the ASA outside interface, it is first decapsulated, so the 10.10.10.0/24 IP address is removed.
The result is an IP packet with a source and destination IP in the 192.168.10.0/24 subnet, and the packet is going in the OUTSIDE interface and exiting the INSIDE interface. Under normal circumstances, this traffic would be NATed. But we don’t want that, because the addresses are already the inside addresses we want. So we use this commands:
ASA1(config)# object network LAN
ASA1(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA1(config)# object network VPN_POOL
ASA1(config-network-object)# subnet 192.168.10.0 255.255.255.0
ASA1(config)# nat (INSIDE,OUTSIDE) source static LAN LAN destination static VPN_POOL VPN_POOL
These commands simply state that any traffic that traverses the ASA with these IP addresses should not be translated. It essentially says: translate 192.168.1.0/24 to 192.168.1.0/24 and 192.168.10.0/24 to 192.168.10.0/24. This is why LAN and VPN_POOL are stated twice in the comand.
I hope this has been helpful!
Laz