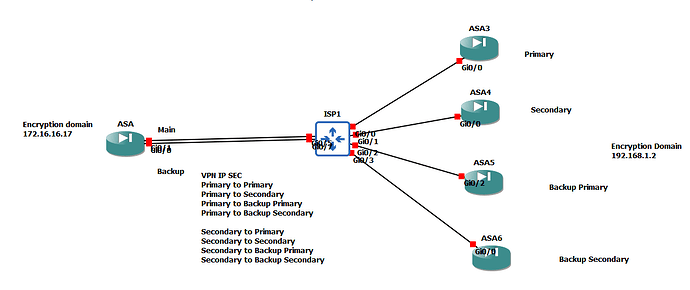
Hello Yik
The syslogs that you shared with us seem to indicate that the first and probably most significant error taking place, is one that involves the generation of the hash using SHA-1.
Jan 07 2023 18:52:27 <hostname> : %ASA-3-402145: CRYPTO: Hash generation error: algorithm 'sha1'
This message indicates an error in generating the hash using the SHA-1 algorithm. This is a significant issue as SHA-1 is fundamental to the secure communication and integrity of the IKEv2 VPN connection. This problem might lead to unsuccessful negotiation attempts.
The next important issue is the following message:
Jan 07 2023 18:52:27 <hostname> : %ASA-4-750003: Local:10.1.105.78:500 Remote:10.1.110.33:500 Username:10.1.110.33 IKEv2 Negotiation aborted due to ERROR: Create child exchange failed
This message indicates that the IKEv2 negotiation was aborted due to an error. This is most likely due to the hash generation error seen in the first log message.
Next we see this message:
Jan 07 2023 18:52:50 <hostname> : %ASA-4-113019: Group = 10.1.110.33, Username = 10.1.110.33, IP = 10.1.110.33, Session disconnected. Session Type: LAN-to-LAN, Duration: 23h:59m:21s, Bytes xmt: 54985186, Bytes rcv: 236614885, Reason: User Requested
Note the “user requested” reason at the end. It seems that the VPN session attempt was manually disconnected.
Finally, at the very end, we see a successful establishment of a new connection:
Jan 07 2023 18:52:50 <hostname> : %ASA-5-750006: Local:10.1.105.78:500 Remote:10.1.110.33:500 Username:10.1.110.33 IKEv2 SA UP. Reason: New Connection Established
This seems to indicate that the previous problems were resolved.
Now this is just a description of what some of the messages here mean. In order to fully troubleshoot, we would need to know more about your particular VPN setup, what application was being accessed, and some more information about the configuration on the ASA. Can you share some more information so that we can help you further?
I hope this has been helpful!
Laz