This topic is to discuss the following lesson:
Great post , very informative
Great post RENE!! CBAC is kind of obsolte but it’s a key in order to understand zone-based FW or as I named It ZOMBIES FIREWAL, thanks for all your help!!
Thanks Miguel!
Hi Rene,
I tried simple ACL in packet tracer and I found at least one explicit ACE entry is needed in acces-list to make implicit " deny ip any any" effective, otherwise it allows all the traffic if
it is an empty access-list.
Thanks,
Srini
Hi Srini,
That’s right, it’s strange that they programmed it like this but that’s the way it works ![]()
Rene
Hi Rene,
Command “ip inspect name FIREWALL ftp” takes care of active and passive ftp ?
Thanks,
Srini
Hi Srini,
Yes both should work. CBAC has more intelligence than the reflexive access-list. It will look into the payload to see what temporary rules are required.
Rene
Thanks Rene. Very Simple to Configure from operators perspective.
Hlw Rene,
CBAC will apply Dynamic ACL for returen traffic like Reflexive ACL by inspecting Protocol ??
br/
zaman
Hi Zaman,
Hello, that’s right. Inspect will keep track of outgoing connections and allows the return traffic.
Rene
Hi, Rene
How cisco CDA would work with CBAC? I wonder how CBAC is different then Idetity ACL? would you be able to provide article on it?
Thanks
Shraddha
I’m still a bit confused about how the ACL taking care of traffic from the outside ( the DENY_ALL_INTERNET) refers back to the inspect function? Is it just because we have inspect out and Access-group IN on the same interface that both will be associated ?
If that’s not clear, I’m referring to the output of the “show ip inspect all” , how the inspect function know which ACL the inspect results will be applied to ? Cheers !
Hello Clement
Essentially you are correct. Because the inspect command and the access group are configured on the same interface, they automatically work together. However, don’t think of the access list being associated in some way with the inspect command. The inspect command can be thought of as a modifier of any access list functionality that has been applied to the interface. You can add the same inspect command to other interfaces as well, and it will modify the behaviour of the access lists configured there.
I hope this has been helpful!
Laz
hi here iam unable to do the command ip inspect
Hello John
For this specific command, Cisco states that:
This command is supported in the Cisco IOS Release 12.2SX train. Support in a specific 12.2SX release of this train depends on your feature set, platform, and platform hardware.
In order to determine if your IOS supports this feature, you can use the Cisco Feature Navigator.
I hope this has been helpful!
Laz
Hi Rene and staff,
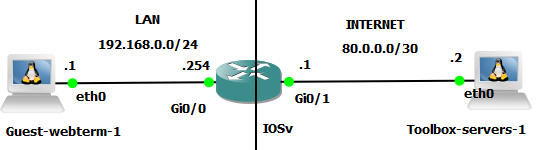
just for fun i do this lab using “realistic” client and “realistic” server and IOSv for router
I do also NAT to be realistic
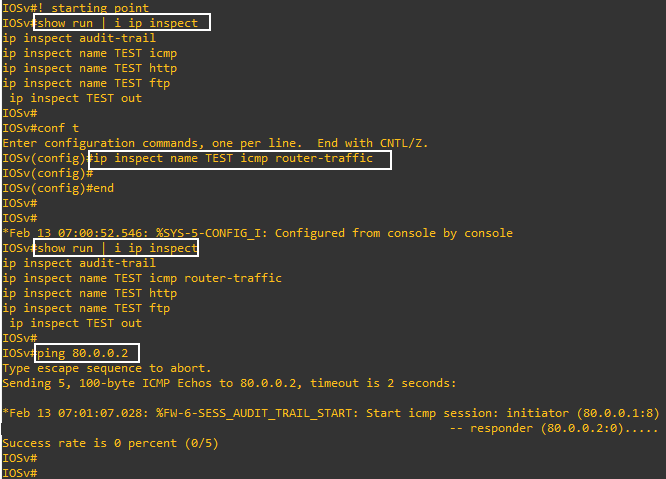
IOSv(config)#ip nat inside source static 192.168.0.1 80.0.0.1
All works fine, except when router initiates the ping
When i set
IOSv(config)#ip inspect name TEST icmp router-traffic
(in my lab, i use TEST instead of FIREWALL)
and to be specific, IOSv do not add a rule in the run config, but IOSv replace the rule ip inspect name TEST icmp with the rule ip inspect name TEST icmp router-traffic
and…it does not work
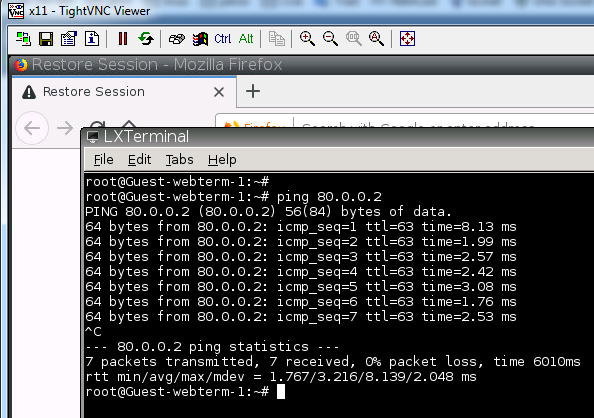
But the linux guest in the LAN can ping the server
Could it be an image issue ?

Regards
Hello Dominique
It’s always great to see you experimenting with various scenarios!
First of all, the addition of the router-traffic keyword does “overwrite” the previous entry without the keyword. But keep in mind that even with this keyword, the inspection of traffic takes place for both traffic generated by the router and traffic passing through the router. This is further described in this Cisco Documentation. So this is why your Linux device is able to ping.
Now about the router-generated traffic that is failing. This is likely due to the introduction of NAT. I suspect that if you remove the NAT configuration, the communication will take place as expected. When you ping 80.0.0.2, what source address is being used? Try specifying the source address in your command. Also, note the order of operations that take place with ACLs and NAT. Specifically, take a look at this post on the Cisco community forum that details the combination of NAT and CBAC, that might be helpful in your troubleshooting:
Let us know how you get along with this!
I hope this has been helpful!
Laz
am I wrong to think of this just as same concept as stateful firewall where the firewall knows to let any traffic back in where their is a connection?
To me it seems like the same thing except maybe the big difference is this is for a router instead of a firewall so we are basically giving a router some firewall capabilities and while it says layer 7 its kind of ports still 443 for http etc…
I read somewhere else that someone said this is older tech and so guessing other things came further I just ran into this when studying up on Control Plane Policing and was like what the hex is CBAC.
Hello Brian
CBAC is part of what Cisco calls the Cisco IOS Firewall feature set. It’s essentially a subset of firewall functionality that is made available on Cisco IOS routers. You can find out more about this feature set here:
The purpose of this feature set is to enable security features on an already existing Cisco IOS device, without the need to purchase a purpose-built firewall. I would say it is a feature of convenience and should be used sparingly. Some may call it a “poor man’s firewall.” It does have limitations, which are detailed here. In any case, it should be used sparingly and only in low-risk situations, such as a small office with no mission-critical network services or data.
For proper security, a separate purpose-built firewall should be used.
The technology is indeed old. The link I sent you above is almost 20 years old, but it is still an active feature in Cisco’s IOS 15M&T releases, so it’s still usable today.
I hope this has been helpful!
Laz