This topic is to discuss the following lesson:
Thank You Rene, Cisco TAC used to do it and now I can do it ![]()
One thing that puzzles me about EPC is this seemingly artificial choice Cisco has you make between CEF and Process-switched methods. Why not just have it capture everything that traverses the interface in question? For example, I was trying to extend your example (and practice with extended ACLs) so that I would capture only BGP information being exchange between neighbors. I filtered on TCP 179 in both directions, and even threw in TCP established for good measure. No matter what I did, I would always capture zero packets. The only thing I can think of is that BGP traffic must be process-switched and not CEF switched.
Also, I find it a bit odd that any commands entered as “monitor capture” don’t show up in the running config. It would sure be handy to run a “show run | s monitor capture” to see all the related commands that have already been issued.
I thought about it some more, and, of course, the BGP traffic would be processed switched since it is destined for the router itself to be processed (stupid me). I still don’t know why it is necessary to specify whether you want the buffer to be CEF or Processed. Perhaps it is because traffic that would have normally been sent through CEF is now having to be punted so a copy can be placed in the EPC buffer.
Hi
Can we use the same method in nexus also ?
On NX-OS you can use Ethanalyzer:
Hi Andrew,
BGP is indeed process switched ![]() There are some different EPC options for CEF or process switched traffic so I guess that’s why they implemented it like this.
There are some different EPC options for CEF or process switched traffic so I guess that’s why they implemented it like this.
It does punt CEF traffic so when you use EPC, you should see your CPU load increase a bit…it’s something to be aware of.
I agree the configuration could be a bit easier. I always find myself copy/pasting a lot when I have to use EPC ![]()
Rene
Hello Rene,
On a production network is it possible to crash the router when we capture packets? If yes, how we should know whether it is high risk and we shouldn’t run EPC at all?
Angelos
Do you have a lesson on configuring port mirror on switches when using wireshark?
Hi Angelos,
EPC increases the CPU load so technically, it’s possible. When you do this, I would recommend to start with an access-list that doesn’t match a lot of traffic. Capture some traffic, then look at the CPU load.
Also, you can set a limit to the number of packets with the limit packets parameter.
Rene
Hi Jason,
Here they are:
Rene
Rene,
Is it possible to provide an example of the above mentioned procedure you provided? Would like to see how this can be configured. Thanks in advance.
Angelos
Hello Angelos
The lesson itself contains an example where EPC was used to capture the packets on R2, and how the capture file was transferred to a computer to be viewed via Wireshark.
Now what I suggest , and I believe this will also help you in gaining experience, is to try to recreate this topology in GNS3 or some other simulator with the config options that Rene has suggested so you can recreate this example and you can have the opportunity to view the results first hand. I believe that we always learn best when we apply it and gain personal experience from it.
If you do perform the experiment, please share your results with us!
I hope this has been helpful!
Laz
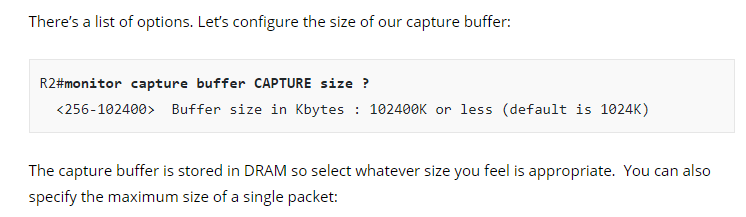
I have a question regarding this buffer of 8192K? Does it mean that the max. pcap file can be 8 MB? I think this is really small.
Hello Lukas
The maximum buffer size for the particular device that Rene is using is actually 102400 KB or 102 MB. See the screenshot below:
Now keep in mind that the buffer is in the RAM of the Cisco device, which is usually not excessively large. The maximum sizes available for buffers will depend on the platform, the IOS and the available memory at the time.
For this reason, unlike Wireshark, the EPC feature is not designed to run for extensive periods of time. It should be used to capture specific traffic that is generated for the purpose of it being captured and analysed.
I hope this has been helpful!
Laz
Hi Laz,
thanks a lot for your nice explanation ![]()
Kind regards,
Lukas
Where are the return packets of the ping?
Hello Arun
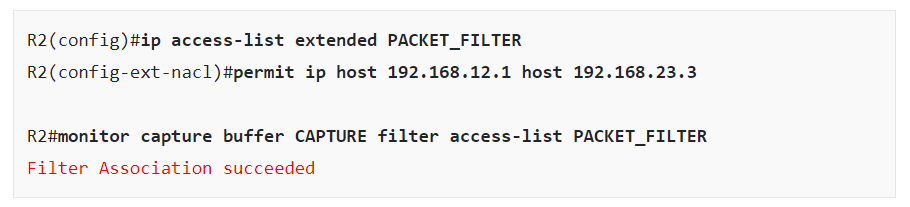
In the configuration of the capture buffer, Rene created an access list that specifies which packets will be captured. The specific access list and how it was applied is shown below:
The access list specifies that only traffic from 192.168.12.1 to 192.168.23.3 will be captured. This means that only the echo requests will be captured and not the replies.
I hope this has been helpful!
Laz
Just a syntax question .. if you want to export capture to local flash what is the command? I have searched various websites / docs but the expectation is always ftp or tftp.
Many Thanks
Frank
Hello Frank
In order to redirect the output of a show command, you can use the pipe character “|”. I’m sure you’ve used it with the begin or include keywords, but it can be used to redirect to a file on the device file system. You can use the following syntax:
show command | append flash:showoutput.txt
where the word “command” can be replaced with whatever command you want to show.
Now Cisco actually calls the “flash:showoutput.txt” portion of the command a URL. This can indeed be a URL using FTP or TFTP, but it can also be a URL with the specific file system you want to save to. Some platforms may not use “flash” but another indicator. You can determine which memory you want to save to by issuing the show file systems command. It will list all of the available prefixes that you can use.
I hope this has been helpful!
Laz