Hi
Is it possible to do RSPAN on a switch and carry the traffic via ISP (if layer2 hand off) and get the span output on another site? e.g say VPLS service? just wanted to know in case if it is possible or do we need RSPAN support from ISP? or just vlan if it is allowed would that be sufficient?
Hello Mahadevan
RSPAN requires that you create a VLAN that will be used as the RSPAN VLAN, and that both the switch with the source port and the switch with the destination port, must have access to that VLAN, and communicate with each other at Layer 2 across that VLAN.
This means that the two devices must have a L2 connection. This is indeed possible using VPLS. This requires a particular configuration on the ISP/carrier devices that will allow this, and more about such a configuration can be found at the following Cisco documentation:
This includes some restrictions that you will find on RSPAN as well.
Now if you want to use the SPAN feature between two devices that are not in any way connected over an L2 link of any kind, you can always use Encapsulated remote SPAN (ERSPAN) which creates a GRE tunnel between the two devices, and sends captured traffic over that tunnel. As long as the two devices can communicate over L3 (using IP addressing and routing), ERSPAN can be enabled. More information about the differences between SPAN, RSPAN, and ERSPAN can be found at this Cisco Community link.
You can also find out more about how to configure ERSPAN here:
I hope this has been helpful!
Laz
Thanks a lot for your response Lazaros Agapides!! much appreciated!
Hi Everyone,
Is it possible to use multiple VLANS for RSPAN?
Hello Sam
As stated in the lesson, for both SPAN and RSPAN:
- The source interface can be anything…switchport, routed port, access port, trunk port, etherchannel, etc.
- You can use multiple source interfaces or multiple VLANs, but you can’t mix interfaces and VLANs.
So this means that you can monitor a VLAN as the source (in such a case, all ports on that VLAN are monitored), and you can have multiple VLANs included as sources in the same SPAN or RSPAN session. However, you cannot mix and match both physical interfaces and VLANs in the same SPAN or RSPAN session.
More detailed information can be found at this Cisco documentation:
I hope this has been helpful!
Laz
Laz,
I have configured a trunk ports between three 3560 switches. Confirmed that the trunk is good and working.
On SW2 and SW3 configured the following two lines:
monitor session 1 source interface Fa0/13 , Fa0/23
monitor session 1 destination remote vlan 999
Note: vlan 999 is configured as a remote vlan. Also VTP version 1 with a domain name is configured and is working as expected.
On SW1, I have the following configured:
monitor session 1 source remote vlan 999
monitor session 1 destination interface Fa0/48
I have connected my laptop to port fa0/48. I have started capturing packet, however, I am NOT seeing anything other than DHCP activities. What I am doing wrong?
Basically, I am trying to learn more about the spanning tree, so I have configured the RSPAN, however, I cannot see anything other than the Loop and DHCP Protocols. I would like to see the BPDU and everything else. Thanks!
Hello Eyad
By default SPAN and RSPAN do not monitor Layer 2 protocol messages such as STP and CDP. This means that BPDUs will not be captured. However, if you use the encapsulation replicate keywords when configuring the destination port and VLAN, then all packet types, including BPDUs and other L2 protocol messages are also monitored.
Try using these keywords in your configuration and let us know your results!
I hope this has been helpful!
Laz
Laz, I just added the following commands on SW1 only and NOT on SW2 nor SW3, since SW1 is the switch that connects to my laptop via fa0/48:
monitor session 1 destination interface Fa0/48 encapsulation replicate
monitor session 1 source remote vlan 999
I still have the same problem and I cannot see CDP, nor STP protocols, however, once I removed this command by typing:
no monitor session 1 destination interface Fa0/48 encapsulation replicate
then I started seeing the CDP, STP, …etc.
So, I typed the command again:
monitor session 1 destination interface Fa0/48 encapsulation replicate
I am no longer seeing the STP nor CDP… I am so confused. Is this an IOS bug or I am missing something?
I removed it again, then I started seeing the CDP and STP protocols. What’s your thoughts?
Also, it looks that the “encapsulation replicate” command valids only for a “destination interface” since I couldn’t add it to a source nor for a VLAN. Please confirm. Thanks
Hello Eyad
In this Cisco documentation, you will find the following explanation:
The default configuration for local SPAN session ports is to send all packets untagged. SPAN also does not normally monitor bridge protocol data unit (BPDU) packets and Layer 2 protocols, such as Cisco Discovery Protocol (CDP), VLAN Trunk Protocol (VTP), Dynamic Trunking Protocol (DTP), Spanning Tree Protocol (STP), and Port Aggregation Protocol (PAgP). However, when you enter the encapsulation replicate keywords when configuring a destination port, these changes occur:
Packets are sent on the destination port with the same encapsulation—untagged, Inter-Switch Link (ISL), or IEEE 802.1Q—that they had on the source port.
Packets of all types, including BPDU and Layer 2 protocol packets, are monitored.
Therefore, a local SPAN session with encapsulation replicate enabled can have a mixture of untagged, ISL, and IEEE 802.1Q tagged packets appear on the destination port.
Now, originally, you mentioned in your previous post that you had configured SPAN but you weren’t seeing any BPDUs or CDP messages. But when you remove the monitor session destination configuration of the interface completely, you begin seeing them. Regardless of the encapsulation replicate command, can you specify what the difference in your configuration is between those two states?
Also, keep in mind that if you used the no monitor session 1 destination interface Fa0/48 encapsulation replicate command, then you are essentially removing Fa0/48 from the SPAN feature and not just the encapsulation. That’s where you have your packet sniffing laptop, right? So Fa0/48 becomes a normal port that sends normal packets, so you may see some STP or CDP packets being sent there.
I suggest you attempt the SPAN lab from scratch, but initially work on local SPAN. Using the commands in the linked Cisco document, capture your local CDP and STP packets, and then move on to attempting it with multiple switches and RSPAN. Let us know how you get along!
I hope this has been helpful!
Laz
Thanks Laz, yeah it’s working fine on the local SPAN. This is good enough at this point time. Thanks again!
Hello Rene,
I am having 2 challenges,
No 1, i do not see vlans when i look into our wire shark capture for our voip calls.
Here is the config for the span monitor:
monitor session 1 source interface gigabitethernet1/0/20
monitor session 1 source interface gigabitethernet2/0/19
monitor session 1 destination interface Te3/1/3 encapsulation replicate
Secondly, we observe we were having voip issues.Our phone provider suggested a packet loss but i dont seem to see that in the capture .Kindly take a look to a capture we took for a phone extension (capture-between-2242-and-2296.pcapng (987.5 KB)
Hello Temitope
When you use the encapsulation replicate keywords, the monitored frames will be sent out of the destination interface in the same form as they have been sent/received on the source interfaces. If you are not getting VLAN tags, then it is likely that Gi1/0/20 and 2/0/19 are not sending/receiving tagged frames. I assume these ports have an IP phone on them and you are expecting the voice frames to be tagged? I see you’re using Grandstream phones. You may need to ensure that the phone is set to include a tag for voice traffic.
Looking briefly at your Wireshark capture, there is no packet loss nor is there any extensive jitter or latency. Voice is a tricky issue to deal with. When you have “issues” you must be very precise in your description. Do you hear a bad quality voice? one-way voice? no voice at all? I was able to listen to the conversation in the Wireshark capture, and it seems one user was speaking while the other could not hear. If it is indeed one-way voice, the problem can be a series of things including NAT issues, firewalls, routing and others.
Just a note, be careful what you share publicly as far as packet captures go, because voice conversations can be reconstructed, and even user names can be determined from these files.
I hope this has been helpful!
Laz
Thank you sir as helpful as always
Hi guys,
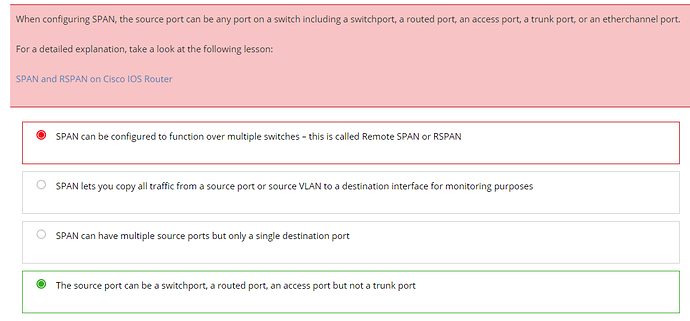
Can the source for SPAN be a trunk port, or not? I am seeing conflicting info below, where it says in the answer that it cannot be trunk port, but in the explanation it says it can:
Thanks!
Hello Louis
I took a look at this question, and it asks: Which of the following statements is not true concerning Switchport Port Analyzer (SPAN)?
The statement that is not true is indeed: “The source port can be a switchport, a routed port, an access port but not a trunk port.”
So this is the correct answer because it is not true.
I hope this has been helpful!
Laz
Hi,
I read in the course, and on the forum, that destination ports do not forward traffic but I found the following command on Cisco’s site that allows ingress traffic on a destination SPAN port:
monitor session session_number destination { interface interface-id [, | -] [ encapsulation replicate] [ingress {dot1q vlan vlan-id | isl | untagged vlan vlan-id | vlan vlan-id }]}
Enter ingress with keywords to enable forwarding of incoming traffic on the destination port and to specify the encapsulation type:
- dot1q vlan vlan-id— Accept incoming packets with IEEE 802.1Q encapsulation with the specified VLAN as the default VLAN.
- isl — Forward ingress packets with ISL encapsulation.
- untagged vlan vlan-id or vlan vlan-id— Accept incoming packets with untagged encapsulation type with the specified VLAN as the default VLAN.
However, I labbed this up in CML2 and the command doesn’t have the ingress option. Has it been deprecated? Or replaced by another command?
Thanks for the help.
Sam
Hello Samir
Yes, it is possible to enable a SPAN destination interface to accept incoming traffic and to forward it. This is a feature that is available only on some platforms and some IOS versions. Apparently, in CML2, the feature is not supported.
This allows you to connect a network monitoring device such as a computer with Wireshark, and provide that computer with network access. You would configure it using the commands you have shared above.
You can find out more info about it here:
As stated in the above documentation “The basic characteristic of a SPAN destination port is that it does not transmit any traffic except the traffic required for the SPAN session.” The forwarding feature is an exception to this general rule, but should be used sparingly as destination SPAN ports can be quite overwhelmed with traffic, depending upon the number of source ports and the traffic that they may be carrying.
I hope this has been helpful!
Laz
Just to verify. SPAN/RSPAN are used on switches only? Can we use SPAN//RSPAN on routers too?
Hello Leon
SPAN and RSPAN are indeed features that exist only in Cisco switches. There are however some exceptions to this rule. For example, the ASR 903 series router supports SPAN, but with some additional limitations. You can find more info on that here:
For the most part, however, if you want to perform packet capturing on a router, there are other more appropriate and useful features including:
I hope this has been helpful!
Laz
Is there a way to capture STP Events on a specific VLAN via RSPAN on a multiple Switches environment?