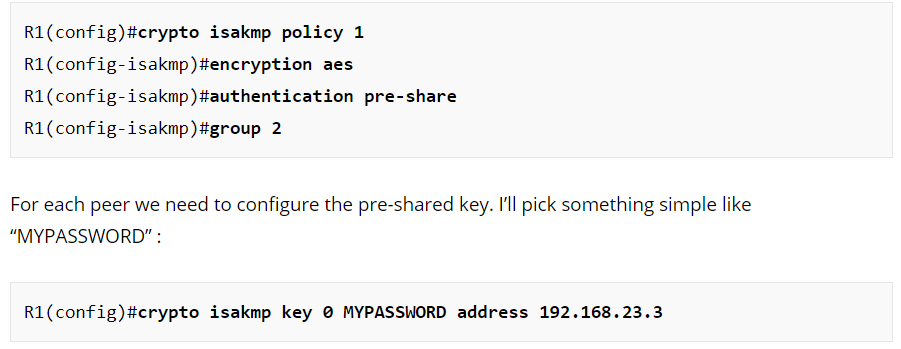
This topic is to discuss the following lesson:
what is the configuration of R2?
Nothing has been configured on R2, just the IP addresses on its FastEthernet interfaces.
Rene ..Not working for me. 1.1.1.1/32 and 3.3.3.3/32 are not reachable. i checked all configuration , almost same as above. But not working
**
R3#sh crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: CRYPTOMAP, local addr 192.168.23.3
protected vrf: (none)
local ident (addr/mask/prot/port): (3.3.3.3/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/0/0)
current_peer 192.168.12.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 192.168.23.3, remote crypto endpt.: 192.168.12.1
path mtu 1500, ip mtu 1500
current outbound spi: 0x0(0)
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
R3#
Hi Amit,
This show command only tells you that no packets are encrypted or decrypted. You need to check the following in order:
Is routing configured correctly?
Are your ACLs for the VPN configured correctly?
Are the crypto maps configured correctly?
Do you have a security association?
If those are all OK…do a debug for the security association to see what is wrong.
Hi
Don’t you need the tunnel ip address, so you can use that as next hop.
R1(config)#ex. ip route 3.3.3.3 255.255.255.255 192.168.13.3
best regards mpo
Its not working. Can u pls advise if any routing protocol is needed?
Hi Chiru,
The example is complete, I’m using static routes for connectivity so you won’t need a routing protocol.
We’ll need a little bit more details than “not working” to find out what the problem is ![]()
Rene
At first I got some issues, I thought there was an issue with the LAB itself, then I followed the troubleshooting RENE suggested and I found the ISSUE ![]()
I Created a LAB with IPSEC tunnels and sub-interfaces,if you want it just let me know.
Rene,Thanks for all your help.
Hi Renee!
I am wondering, is there anyway to initialize phase 1 or 2 from the router itself? For example, if I have an ACL such as permit host A to host B, normally I would have to ping from host A to B in order to initialize the tunnel. However, I’m wondering if there is anyway to initialize phase from from just the 2 peers without having to generate traffic from the end points?
I hope that’s clear, Thanks!
I went through this IPsec Tunnel configuration and checked the R1#‘show crypto ipsec sa’ table; but it did not come up with local and remote ident: ip addresses. that shows in your post as well as in ipsec site-to-site vpn. Everything else fine.
R1#show crypto ipsec sa
interface: Serial1/0
Crypto map tag: cryptomap, local addr 12.12.12.1
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/47/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/47/0)
…
please help to know why it is?
Hmm are you sure the VPN is working? Do you see the number of encrypted/decrypted packets increase?
differences between Diffie-Hellman and Authantication
hello , i have mixed up in my mind the two concepts. If we have already used pre-shared keys why is necessary to use Diffie-Hellman group? Of course i understand DIffie-Hellman parameter is mandatory to the configuration. Diffie-Hellman isn’t for exchange keys for origin authentication encryption and for integrity ? i am wonder if all these methods are linked together with share secret key
Thanks in advance
Geia sou Dionisis
Authentication and the use of the Diffie-Hellman algorithm are two distinct and separate functionalities of ISAKMP negotiation.
The authentication pre-share command indicates that a pre-shared key will be used (configured manually on each device) as the method by which the devices will establish the identity of each other as an IPsec peers.
The group 2 command on the other hand indicates the use of Group 2 Diffie-Hellman identifier to derive a shared symmetric secret without transmitting it. This is used for the purpose of encryption.
So the preshared key is to identify the peer, while the DH secret key is for encryption and decryption purposes.
I hope this helps!
Laz
Geia sou Lazare ,
your answered me very clear and you have simplified it for me . Are there any sources that you know that they can help me to learn more about IPsec . Not about configuraton because Rene explains about it very nice but for details about the protocols that we use . Like could we use HMAC with PKI player ( private- public key )instead for pre-share key authentication ? Now you understand how much confuse my mind all these concepts. ![]()
Thanks a lot
Hello again Dionisis
IPsec has been developed by IETF and as such there are quite a few RFCs that describe it and how it functions at a very low level. Because there are very many of these, the IETF has published RFC 6071 which is a snapshot of IPsec- and IKE-related RFCs. This can be found here.
Also, Wikipedia’s page on IPsec has a list of links to related RFCs that include HMAC, PKI and other cryptographic algorithms and modes of operation.
I hope this has been helpful!
Laz
Hello Laz ,
It is helpful
Thanks again about the information you have gave me
Rene,
I am not sure how to add a comment at the end of a lesson.
I just finished the Lesson on IPSEC tunnel mode and had trouble getting my GNS3 to work. After looking through your configs, I noticed that you had an extra command.
In the lesson you failed to mention the mode tunnel under the Crypto IPsec transform command.
Thanks for such great work,
John Harmon
Hi John,
Did you use IOS 12.4T? I think that’s the problem then.
In IOS 15, tunnel mode is added automatically under the crypto ipsec transform-set.
Rene