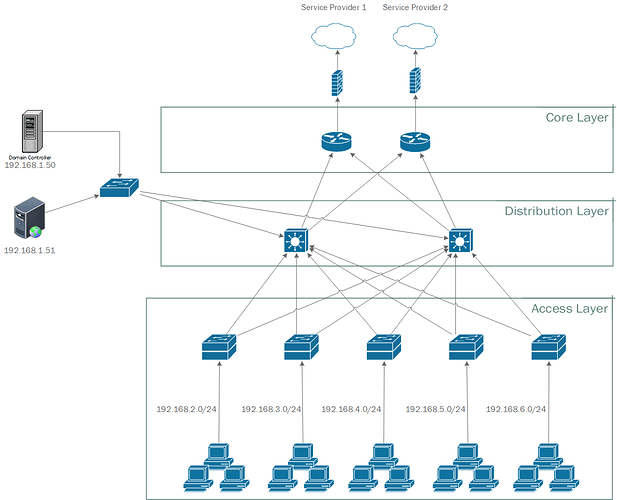
In advance, i apologise for the long post. I’ve been assigned the task of producing a logical design for a new network that must be capable of supporting 1000 machines. The network must provide 99.9% availability and thus i must take measures to ensure capability. There must be an internet connection and provision of a reliable service is necessary. The network must support the business for a further 5 years. I am given no architectural plans of the building but there is only one building and i’m assuming one floor. The previous network had servers running Windows server 2008 R1 with domain controller there also existed a web server. I don’t think i have to be concerned with specific hardware models/names.
I have no previous experience with designing networks and I have little knowledge in the field other than a few days worth of research on the internet. I am not confident in my ability to complete the task but it is critical that i do so.
I have concluded that a hierarchical design is most fitting and that redundancy throughout each layer is necessary to comply with availability requirements. Therefore i plan to make use of multiple service providers with a partial mesh topology connecting two layer 3 switches (in the distribution layer). Then, also with partial mesh, multiple stacks of layer 2 switches in the access layer and obviously the ~1000 end devices.
I’m not sure how many stacks of layer 2 switches should exist and how they should be divided up and how or if i should subnet? I’m not entirely sure if any wireless access points are required since there is no mention of such a requirement however to be safe i imagine at least one wireless access point should be included? Are two switches sufficient to meet the 99.9% availability requirement? Where do local services, domain controller and web server, fit in such a design? Do i require some implementation of the Spanning Tree Protocol? What about firewalls, security and other software?
Thanks for reading.