Hello,
I ma using your postman restconf collection to do a restconf lab on EVE-NG VM with the IOS-XE
“Cisco IOS Software [Everest], Virtual XE Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 16.6.7”
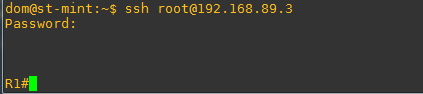
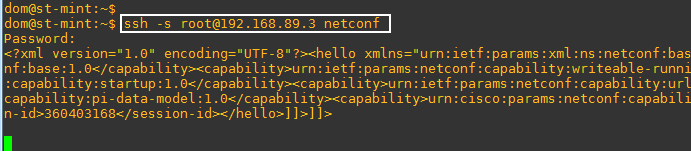
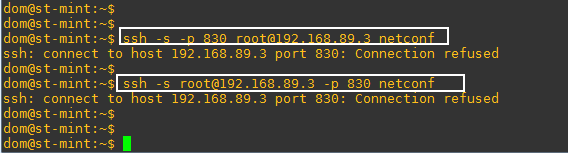
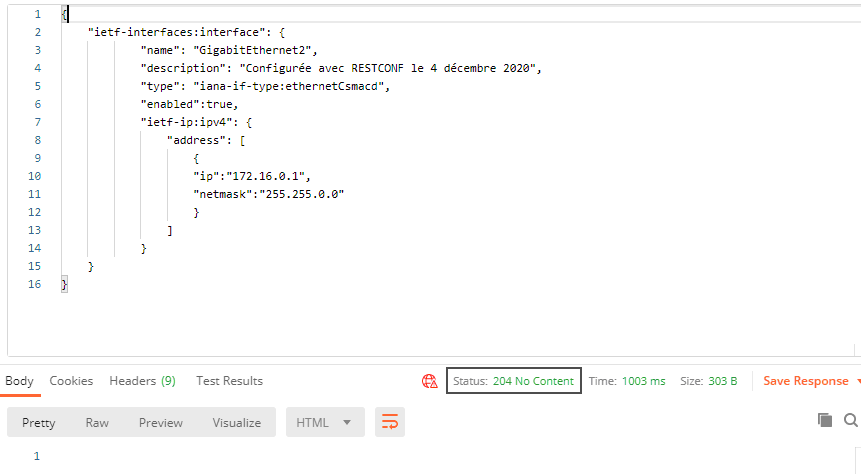
I followed the exact same steps to configure the router and Postman but still not working:
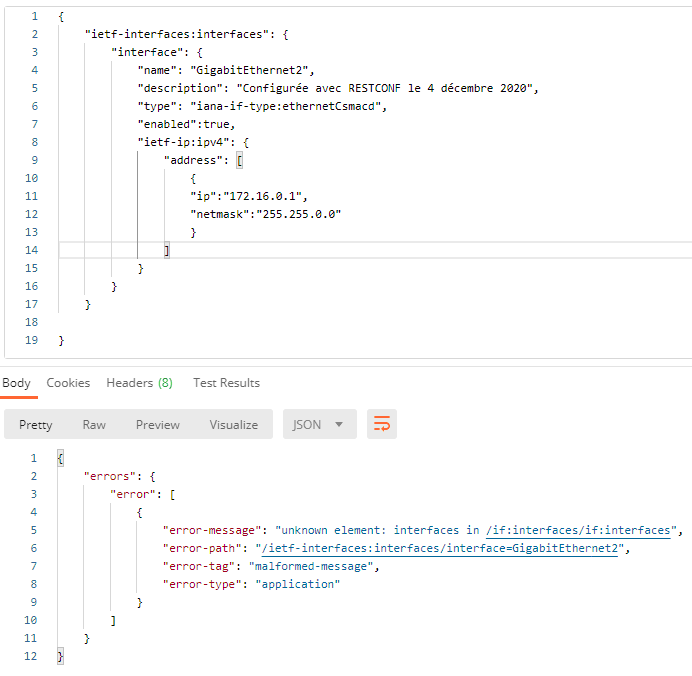
I am getting: “Could not get any response” in Postman right away when I click send
SSL certificate is turned off
Postman is running on my host and I can ping the router. could you please give some hints for troubleshooting…thanks
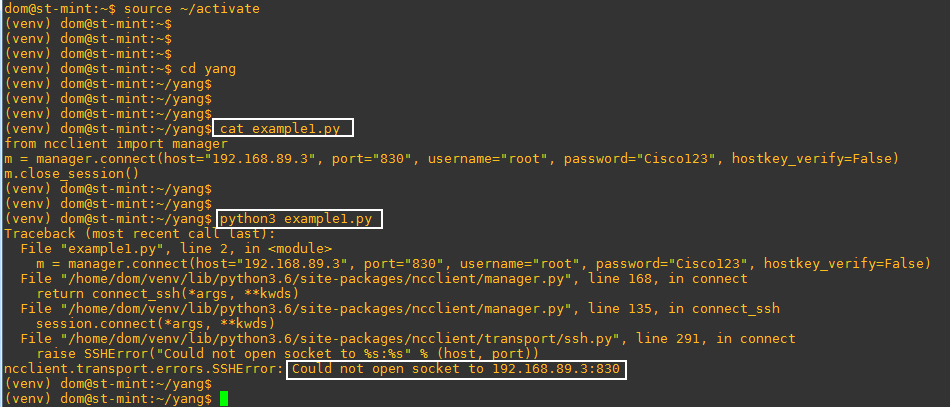
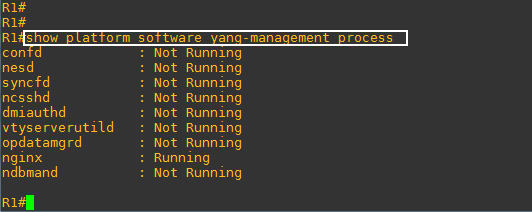
logs show this error but no clue how to resolve it:
Error: write EPROTO 6900:error:14094410:SSL routines:ssl3_read_bytes:sslv3 alert handshake failure:c:\users\administrator\buildkite-agent\builds\pm-electron\postman\electron-release\vendor\node\deps\openssl\openssl\ssl\record\rec_layer_s3.c:1407:SSL alert number 40
Hany