This topic is to discuss the following lesson:
Doing some more research on this. Is this process described here for the wired EAPOL “handshake”. Is there different 4 way handshake used for wireless that uses PMK and GMK keys? Appreciate all the work you guys do!
-Chase
Hello Chase
EAPOL and the WPA 4-way handshake are both important components in network security, especially in authentication processes. In the lesson, EAPOL is described in the context of wired network security, and in particular, with 802.1X authentication. It’s a part of the IEEE 802.1X standard for port-based Network Access Control (NAC).
In this context, EAPOL and WPA 4-way handshake are quite different in their use and processes. Their key differences are listed below:
- Network Type: EAPOL is mainly used in wired networks, while the 4-way handshake is specific to wireless networks.
- Scope: EAPOL is focused on the authentication phase and supports a variety of authentication methods, whereas the 4-way handshake is specifically for establishing encryption keys in WPA/WPA2 wireless networks.
- Key Management: The 4-way handshake directly involves key management for securing data traffic, while EAPOL is more about facilitating authentication and does not deal directly with key management for data encryption.
Now having said that, EAPOL can be used in wireless networks, and in particular, in the context of WPA 4-way handshake. In such a case, EAPOL becomes part of the 4-way handshake process, which is important for key management. Here, it helps in transporting the key material and signaling actions for key management.
So EAPOL is quite versatile as it can play a role in both wired and wireless network environments but with different focuses. In wired networks, its role is predominantly in authentication, while in wireless networks, it extends to key management as part of the WPA/WPA2 protocols.
As far as the use of PMK and GTK in wireless networks, EAPOL is involved in the key management process by facilitating the secure exchange of MPK, PTK, and GTK keys.
I hope this has been helpful!
Laz
@ckress I’m writing an explanation of the WPA 4-way handshake today, which should be finished in a couple of days. I’ll add a link here once it’s finished.
Understanding the WPA keys is a prerequisite. I published this yesterday:
Rene
Here is an explanation of the WPA 4-way handshake:
Hi, everyone.
After seeing this
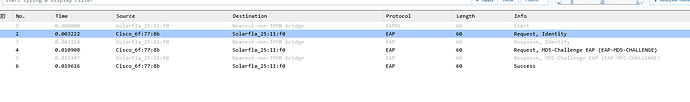
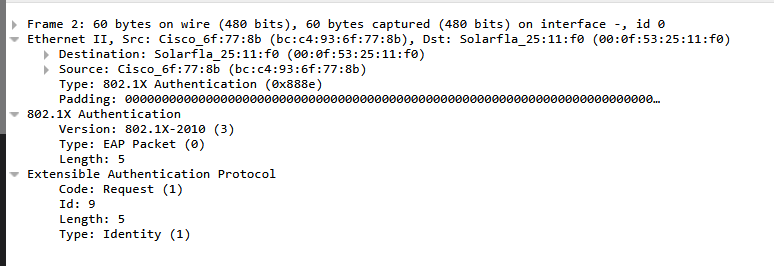
Why are EAP messages such as request identity, etc encapsulated in an EAPOL header? Which is basically the part where it says 802.1X Authentication.
Wouldn’t it make more sense to just grab those fields in EAP and include them in EAPOL altogether?
Rene said that EAP messages are always carried by another protocol which is EAPOL in this case.. Are there any other protocols that can also carry EAP messages? What if EAPOL just wasn’t there? If we removed the EAPOL header, couldn’t the EAP message still be read? Why do EAP messages need to be transported via another protocol?
David
Hello David,
Your understanding is on the right track! It will be helpful to clarify the relationship between EAP and EAPOL, and why they appear as distinct elements in your capture.
EAP (Extensible Authentication Protocol): This is a flexible authentication framework used to validate client credentials (e.g., EAP-TLS, PEAP). It defines message formats (Request/Response) but does not handle transport—it relies on other protocols to carry its messages.
EAPOL (EAP over LAN): This is a Layer 2 encapsulation protocol defined by IEEE 802.1X. It transports EAP messages between a supplicant (client) and an authenticator (switch/Wi-Fi AP) over a LAN. You can think of EAPOL as the “envelope” that delivers EAP “letters.”
How do these two work together? EAP messages (e.g., EAP-Request/Identity) are embedded within EAPOL frames. This is why Wireshark decodes them as separate layers: EAPOL is the outer frame, EAP is the payload.
EAPOL includes its own control packets (e.g., EAPOL-Start, EAPOL-Key, EAPOL-Logoff) to manage the authentication process on the LAN. These are distinct from EAP messages and handle tasks like initiating authentication or distributing encryption keys.
So why does your capture show both EAPOL and EAP? Because EAPOL packets are the Layer 2 frames (e.g., EAPOL-Start, EAPOL-Key) while EAP messages are the authentication payloads inside EAPOL frames (e.g., EAP-Request, EAP-Response).
In your screenshot, Wireshark is highlighting both layers: the outer EAPOL header and the inner EAP data. This is normal—EAP messages are indeed encapsulated within EAPOL as you correctly stated. The distinction in terminology exists because EAPOL handles LAN-specific operations, while EAP is the universal authentication protocol reused across different transports (e.g., RADIUS, PPP).
This may be a simpler approach for this specific scenario, however, EAP and EAPOL have been developed as part of a broader framework, and they have been intentionally designed in this manner to serve a wider range of implementations. So it’s a matter of overall design.
I hope this has been helpful!
Laz