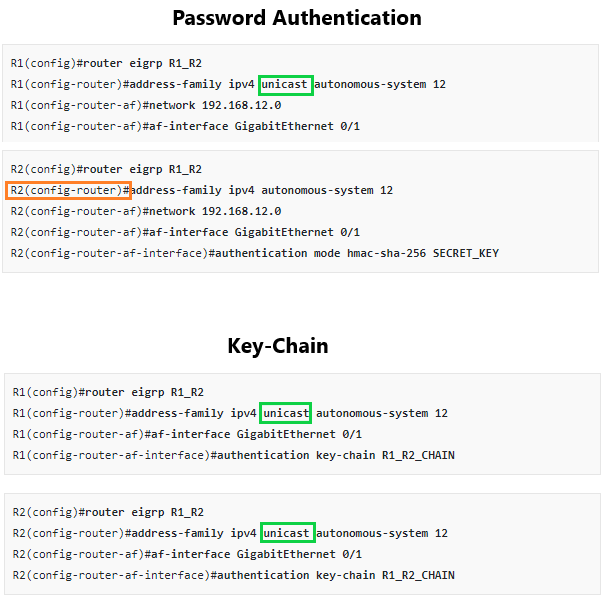
This topic is to discuss the following lesson:
Do any of you guys know why you to have to specify a SHA-256 password as well when using the key chain for the key chain method to work?
I understand you have two elements to this:
The authentication mode: MD5/SHA 256
The authentication method: key-chain/password
But the key chain method wont work until the mode is specified and the only way you can specify the sha256 mode is by using a password as well, this makes no sense to me as when you view the authentication being used with the show commands it even states the keychain is being used.
R4#show eigrp address-family ipv4 1 interfaces detail | inc Auth
Authentication mode is HMAC-SHA-256, key-chain is “EIGRP”
But it has to have a password as well to work:
af-interface Ethernet0/0
authentication mode hmac-sha-256 EIGRP
authentication key-chain EIGRP
exit-af-interface
This to me makes no sense…
Hello Matthew
What you state is very logical, it seems redundant to need to specify a password for the SHA-256 and then to need to specify a keychain password as well. However, this is the methodology used to configure SHA-256.
In order to specify a key-chain, you must first specify the authentication mode. And in order to specify the hmac-sha-256 mode, you must specify a password. (If you choose the MD5 method, you don’t specify a password, but you must employ the key-chain). If you choose to use the key-chain method, then once that is configured, the key-chain password supersedes the hmac-sha-256 password.
It’s just the way that the SHA-256 authentication has been designed. Cisco documentation actually seems to support not using the key-chain method, as the SHA-256 password is considered equally secure:
I hope this has been helpful!
Laz
Hi Guys,
Why is it that you use unicast in this both Password Authentication and Key-Chain for SHA-256 and not for MD5?
Also why is it that you use unicast command in R1 but not R2?
Hello Joseph
When configuring the address family of the named EIGRP configuration, the unicast keyword is actually optional. If it is not specified, the unicast address family is used by default. So in the configuration, whether you use the keyword or not, the resulting configuration remains the same.
For consistency, I will ask Rene to take a look and change the configs for the lesson.
I hope this has been helpful!
Laz
That’s all good Laz, thank you. I’m glad it was there so that I could ask you about it, and now know that it is the default.
Hi Laz,
In your first post you say that the key-chain password supersedes the hmac-sha-256 password. To prove your claim, I configured two routers, one with a different password than the other one and used the same keychain with only one key and the same key-string. The neighborship does not come up. It’s strange because I am also seeing the same output of “show eigrp address-family ipv4 interfaces detail” where the authentication mode only mentions HMAC-SHA-256 and not the static key. If I remove the authentication the neighborship comes up. I don’t have an answer for what is going on.
Here is the config from both routers:
R4(config-router-af)#do sh run | s r e
router eigrp EIGRP-NAMED
!
address-family ipv4 unicast autonomous-system 1
!
af-interface default
passive-interface
exit-af-interface
!
af-interface FastEthernet1/1
authentication mode hmac-sha-256 RIGHT-PASSWORD
authentication key-chain KEYCHAIN-EIGRP-NAMED
no passive-interface
exit-af-interface
!
topology base
exit-af-topology
network 192.168.5.2 0.0.0.0
exit-address-family
R4(config-router-af)#
R4(config-router-af)#do sh key chain
Key-chain KEYCHAIN-EIGRP-NAMED:
key 1 -- text "PASSWORD"
accept lifetime (always valid) - (always valid) [valid now]
send lifetime (always valid) - (always valid) [valid now]
R4(config-router-af)#
R5(config-router-af)#do sh run | s r e
router eigrp EIGRP-NAMED
!
address-family ipv4 unicast autonomous-system 1
!
af-interface default
passive-interface
exit-af-interface
!
af-interface FastEthernet1/1
authentication mode hmac-sha-256 LEFT-PASSWORD
authentication key-chain KEYCHAIN-EIGRP-NAMED
no passive-interface
exit-af-interface
!
topology base
exit-af-topology
network 192.168.5.1 0.0.0.0
exit-address-family
R5(config-router-af)#
R5(config-router-af)#do sh key chain
Key-chain KEYCHAIN-EIGRP-NAMED:
key 1 -- text "PASSWORD"
accept lifetime (always valid) - (always valid) [valid now]
send lifetime (always valid) - (always valid) [valid now]
R5(config-router-af)#
Hello Kevin
This is an intriguing experiment that you shared, thanks for taking the time to do that! I went in and did some labbing myself and have confirmed that when you configure both a keychain and an hmac-sha-256 password, both must match across the routers in order for the neighborship to come up.
Based on our tests, it seems there’s more complexity in how EIGRP processes the hmac-sha-256 password and key-chain combination than what is immediately apparent from the configuration or documentation.
They show that the hmac-sha-256 password which is required when setting the authentication mode on each router must match for the neighborship to form, even though both are using the same key-chain with identical key-strings. That means that the password seems to still be factored into the authentication process alongside the key-chain.
EIGRP might internally combine the hmac-sha-256 password and the key-string from the key-chain to generate the authentication digest. If the passwords differ between the routers, the computed hash values would not match, resulting in failed authentication.
So in order to configure hmac-sha-256 using a keychain, you must also specify a password in the authentication mode command that is consistent across the routers in addition to the keychain for it to work.
I hope this has been helpful!
Laz
I have few questions:
1). Why we need the authentication like sha or md5
2). Can you help me understanding the wireshark capture cause I couldn’t understand the packet flow.
3). I add one more router R3 next to R2 and just configured eigrp with same as number and didn’t set any key chain between however set the authentication of sha between both. I thought R1 and R3 will not have route of each other.
Hello Speedosuper111
Excellent question! Configuring authentication is one thing, but understanding the “why” is another, and that’s extremely important!
One way that a malicious entity may use to disrupt or compromise a network is to try to establish an unauthorized EIGRP adjacency with one of the routers on the network. For example, I could bring in my own router to work (or run a program on my laptop that simulates a router) and plug it into the network jack in an attempt to create such an adjacency.
If I am successful, I can learn about the routes being advertised by EIGRP, and I can also inject my own routes into the routing domain. At the very least, I can disrupt the network, and at worst, I can inspect traffic traversing my “router” possibly compromising user data as well.
Authentication ensures that only authorized EIGRP peers will create adjacencies. Unless I have the password, I will not be able to create an adjacency from my rogue router to a legitimate EIGRP router, and that adds saftey and security to the network.
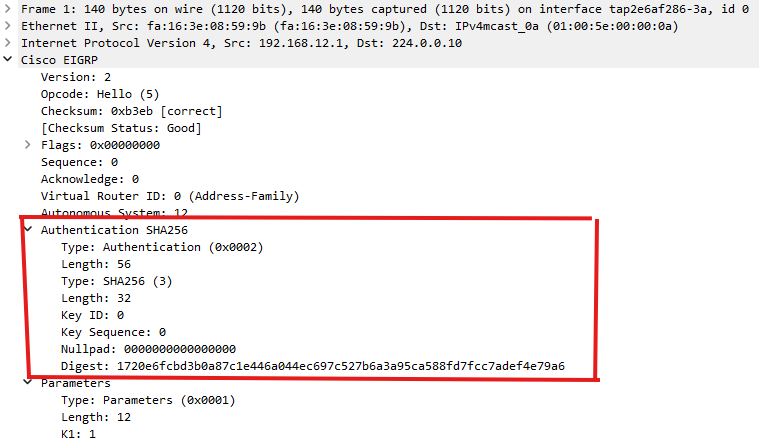
When authentication is enabled, each hello and update message is sent with the Authentication SHA256 section which contains a hash digest in the packet as shown:
The receiving router will verify that digest by running the hash on its own copy of the same key-string or password. The adjacency will form only if those match.
All subsequent messages (Hello and Updates) will contain that digest. (It will be different for each packet containing the messages, because the hash is applied to all the contents of the EIGRP message). The verification is performed for each received message, and only then will the messages be processed. This is the case for both the password configuration and the keychain configuration options.
I hope this has been helpful!
Laz