Hello.
ERSPAN configuration is rather confusing in comparison with SPAN/RSPAN.
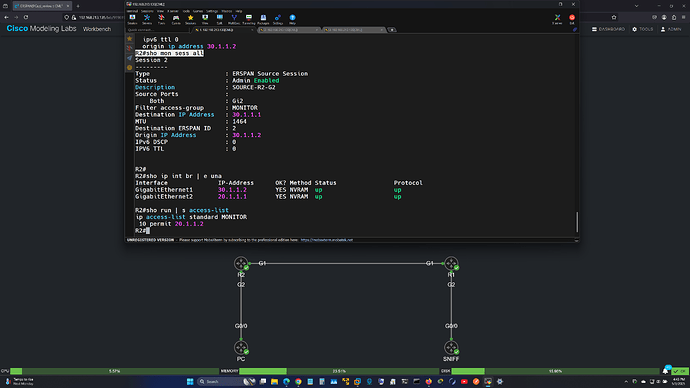
Question 1
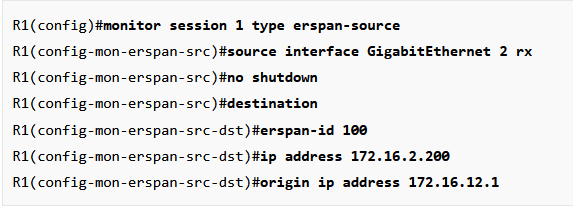
If I understand this right, if the ip address command is under the destination section, it’s telling R1 to which IP address it should tunnel traffic over. You also configure the origin ip address here which is the IP address that you’ll use, just like with traditional GRE configuration.
Question 2
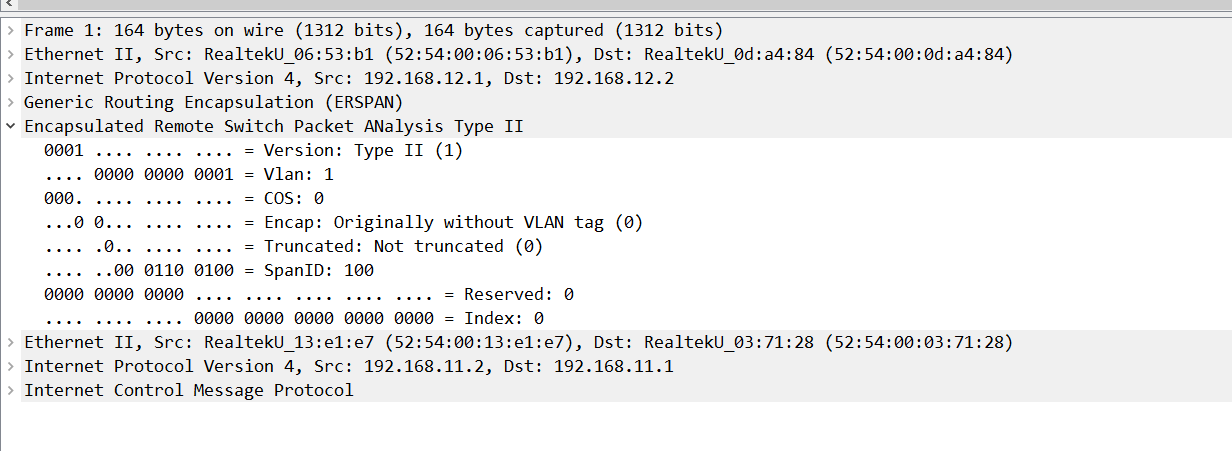
What’s pretty confusing to me is why the destination is 172.16.2.200. which is the traffic analyzer. I’ve seen Kevin Wallace use the same configuration but this isn’t something mandantory. I could just as well specify R2’s G3 interface as the destination.
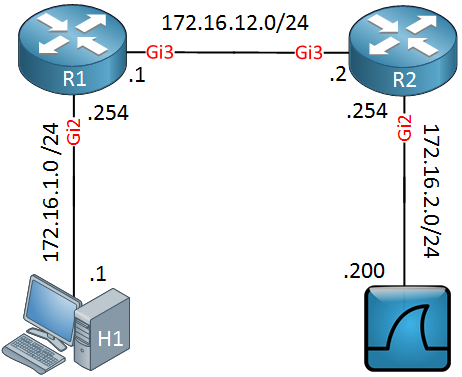
R1
monitor session 1 type erspan-source
no shutdown
source interface Gi1
destination
erspan-id 100
ip address 192.168.12.2
origin ip address 192.168.12.1
R2
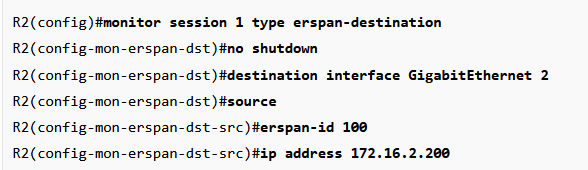
monitor session 1 type erspan-destination
no shutdown
destination interface Gi2
source
erspan-id 100
ip address 192.168.12.2
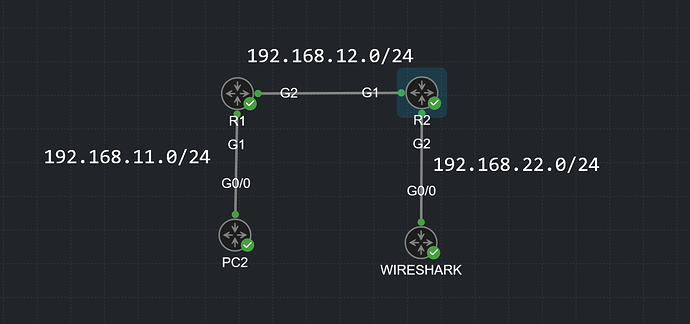
PC2(config-if)#do ping 192.168.11.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.11.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
PC2(config-if)#
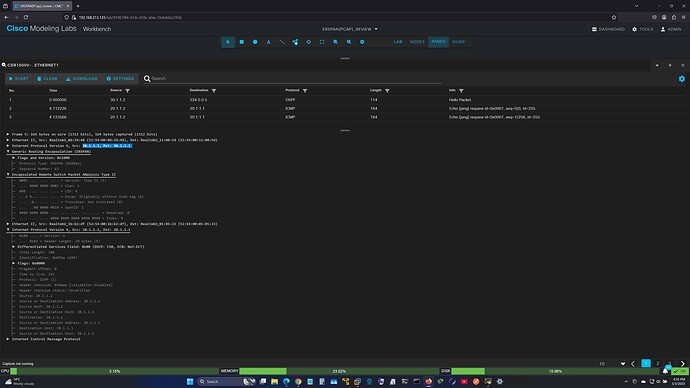
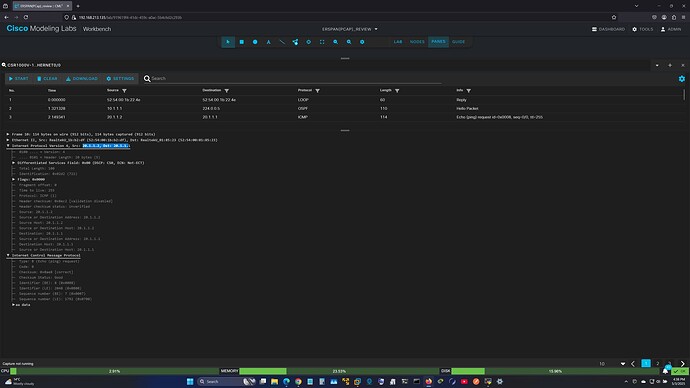
R2 - WIRESHARK
The traffic is being mirrored and appears there

So where did this idea behind specifying the traffic analyzer’s IP as the destination for GRE come from?
R1 - R2
It seems that the destination doesn’t really care about what IP is being used, as long as one that can actually reach R2 is being used, its fine. Since SPAN takes over and sends over the received packet.
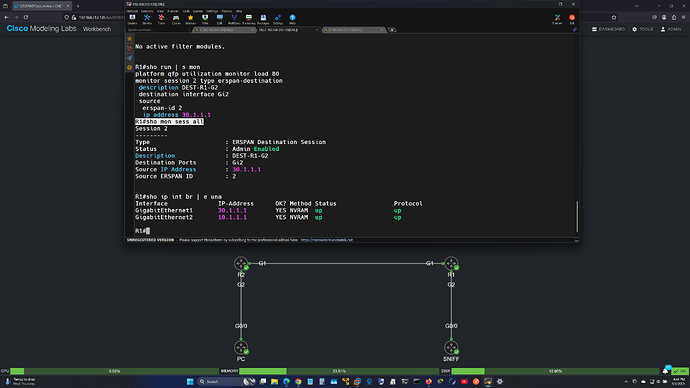
Question 3
Here we are telling R2 to send anything that it receives from R1 towards G2. The source here specifies from
who we should send the packet towards G2? So from someone whose SPAN session is 100 (R1!). However, why the need for the IP address? I’ve configured this without it and it works.
It’s just all slightly confusing considering that the configuration is completely different than from RSPAN. On the RSPAN destination device, you’d specify the source as the remote RSPAN VLAN while here, you use the SPAN session ID as source on R2
RSPAN
monitor session 1 source remote vlan x
ERSPAN
monitor session 1 type erspan-destination
source
erspan-id 100
Not to mention that source interface serves as the source of from where packets should be monitored while the entire source section is relevant to the GRE tunnel 
That’s all, thanks!
David