Hi,
Regarding this:
There are multiple methods for load balancing:
Round-robin: the AVG will hand out the virtual MAC address of AVF1, then AVF2, AVF3 and gets back to AVF1 etc.
Host-dependent: A host will be able to use the same virtual MAC address of an AVF as long as it is reachable.
Weighted: If you want some AVFs to forward more traffic than others you can assign them a different weight.
I’m not sure to understand the difference between glbp priority and glbp weighting.
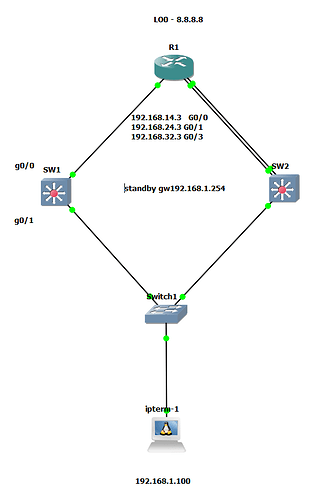
Also I’ve tried to replicate this lab but I think that a routing loop is occurring during pinging the loopback of R1.
can you help me?
Here my captures and a picture of my topology
capture_GLBP_SW1_G00.pcapng (16.1 KB) capture_GLBP_SW2_G00.pcapng (17.2 KB) capture-GLBP-SW2-G03.pcapng (8.6 KB)
topology: