Hi,
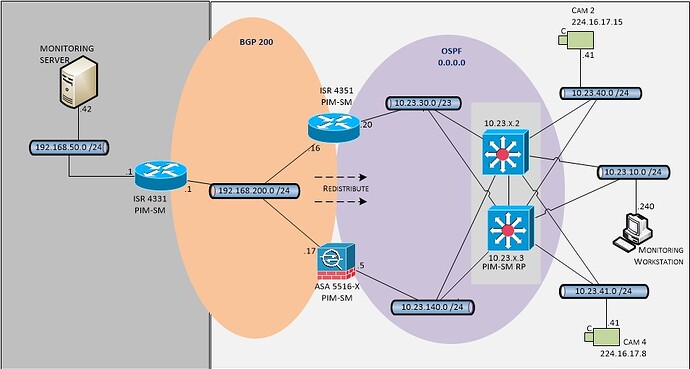
I’m troubleshooting a multicast-related issue across an ASA 5516, and finding it hard to understand how the ACL to permit multicast traffic across its interfaces works. The logical topology below shows my setup.
The monitoring server in far left needs to view multicast video stream from cameras (Cam 2 & Cam 4) in far right. The L3 switches route between vlans (different subnets) and the monitoring server is able to receive unicast streams (via the ASA) from the cameras.
The ASA interfaces shown are at the same security level (100). Multicast routing is configured and PIM sparse mode RP is configured as one of the L3 switches. Interface configs:
!
interface GigabitEthernet1/2
description Inside Interface
nameif inside
security-level 100
ip address 10.23.140.5 255.255.255.0
igmp join-group 224.16.17.15
igmp join-group 224.16.17.8
ospf message-digest-key 1 md5 *****
ospf authentication message-digest
!
interface GigabitEthernet1/3
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/3.200
description Cnxn to Monitoring Network
vlan 200
nameif GENETECFED
security-level 100
ip address 192.168.200.17 255.255.255.0
ipv6 address fd87:777d:126a:ce5b::200:17/64
ipv6 enable
igmp join-group 224.16.17.8
igmp join-group 224.16.17.15
!
!
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
!
pim rp-address 10.23.201.1 EVL-GENETEC-MCAST-GRPS
When I test using packet tracer, with source as multicast group IP and destination as monitoring server, the output shows the packet is dropped due to a configured ACL. There is an ACL on the ASA interface (10.23.140.5) and I have added entries to permit the multicast traffic but I don’t seem to be getting it right. The ACL is shown below
access-list inside_access_in extended permit tcp object-group Systems_Networks any object-group EXTERNAL_WEB_ACCESS
access-list inside_access_in extended permit udp object-group DNS_SERVERS_LOCAL object-group DNS_SERVERS_EXTERNAL eq domain
access-list inside_access_in extended permit udp object-group Systems_Networks object-group DNS_SERVERS_EXTERNAL eq domain
access-list inside_access_in extended permit udp object-group VOIP-GW-CUBE object-group SIP_REGISTRARS_EXTERNAL eq sip
access-list inside_access_in extended permit tcp object-group VOIP-GW-CUBE object-group SIP_REGISTRARS_EXTERNAL eq sip
access-list inside_access_in extended permit icmp any any echo-reply
access-list inside_access_in extended permit icmp any any echo
access-list inside_access_in extended permit icmp any any
access-list inside_access_in extended permit igmp any any
access-list inside_access_in extended permit pim any any
access-list inside_access_in extended permit tcp object-group CCTV-SUBNETS object EXT_GENETEC_SRV_HOST192
access-list inside_access_in extended permit udp object-group CCTV-SUBNETS object EXT_GENETEC_SRV_HOST192
access-list inside_access_in extended permit ip object-group EVL-CCTV-MCAST-GRPS any
access-list inside_access_in extended permit ip any object-group EVL-CCTV-MCAST-GRPS
!
access-group inside_access_in in interface inside
!
object network EXT_GENETEC_SRV_HOST192
host 192.168.50.42
description Genetec SC Server
object network EXT_GENETEC_SRV_SUBNET192
subnet 192.168.50.0 255.255.255.0
object network EXT_GENETEC_SRV_SUBNET172
subnet 172.16.50.0 255.255.255.0
object-group network CCTV-SUBNETS
network-object 10.23.40.0 255.255.255.0
network-object 10.23.41.0 255.255.255.0
object-group network EVL-CCTV-MCAST-GRPS
network-object 224.0.0.0 240.0.0.0
object-group network ETS-MCAST-RECIPIENTS
network-object object EXT_GENETEC_SRV_SUBNET192
network-object object EXT_GENETEC_SRV_SUBNET172
!
Any advice on tackling this would be appreciated.
Thanks