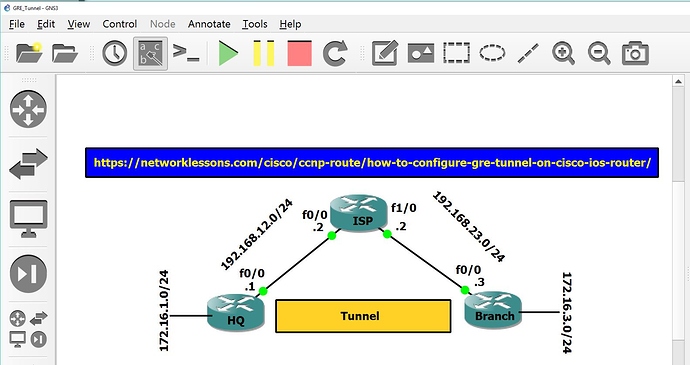
Hi Adrian,
When you use the tunnel source command, you can define an interface or an IP address. When you use the interface, the router will check for the IP address on the interface and use that so the end result is the same.
The tunnel source and destination addresses are only used to build the tunnel, that’s it. When you use this to tunnel something over the Internet, we typically use the public IP address on the outside interfaces for this.
You can use loopbacks as the source addresses if you want redundancy. Let’s say we have two routers that are connected with two physical interfaces. You could establish a tunnel using the IP addresses of one of the physical interfaces but that means that when that link goes down, the tunnel also goes down. In this case, you could establish the tunnel using loopback addresses. Your routing protocol will make sure that when one of the physical links goes down, it will reroute it using the other physical link.
About the IP addresses that we use, take a look at this wireshark capture:
The IP packet with the outer header uses the IP addresses on the outside interfaces, this is what we use to route the packet. You can see it has a GRE header, the second IP header is for the ping between the loopback interfaces. We use the IP addresses on the tunnel interfaces as the next hops.
Hope this helps, if not just ask ![]()
Rene