This topic is to discuss the following lesson:
Thanx Rene,
This a very clear manual. Gonna use it right away…
Andre
Thanks rené,
My present configuration is quite the same but I don’t have (yet) a subnet under the strongswan platform (this may come later).
So I would like to configure the VPN and test it (ping, scp…) directly with the strongwan plateform and not with its subnet.
What should I change in your configuration for it ?
Thanks again.
Hello Luc,
In this case, you might want to test to configure strongSwan as a remote client perhaps.
First I would try to configure a Cisco router as the VPN server and use a Cisco client. Here’s an example:
Once this is working, see if you can replace the client with Strongswan:
Rene
Rene,
How are you using the Ubuntu server with the strongswan on it. Is it in a laptop or do you have a server. Reason for asking is I am wondering how you got the two ports. Maybe you could point me in the right direction on how to set my lab up. thank you
Hi Cristopher,
I use a HP proliant DL360 G7 with a quad NIC running VMware ESXi. Using virtual machines is a great way to test things like this. You can also use a single physical connection from your VMware server to your switch and then configure it as a trunk. Each virtual NIC in your virtual machine can then use a different VLAN.
Rene
Hi Rene,
Just confuse but what’s benifit of using strongwan with a linux server instead cisco router or ASA devices ?
Thanks!
Hello Nguyen
strongSwan has some EAP and mobility extensions that can be useful for enterprise networks. However, the reason why you would use strongSwan for such a connection is primarily because it is a software package that has widespread use, and you will see it frequently in corporate networks. For this reason, it is a good idea to understand how to interconnect with it, as you may be called upon to make such a connection. Because it is well documented and maintained, it is likely that you will encounter it in the marketplace.
Although much of what strongSwan does can be done with a Cisco ASA, it is always good to know how to interconnect with devices of other vendors.
I hope this has been helpful!
Laz
Thanks Laz much !!!
Hi Rene,
The strongswan client and cisco router combo is exactly the setup i need right now.
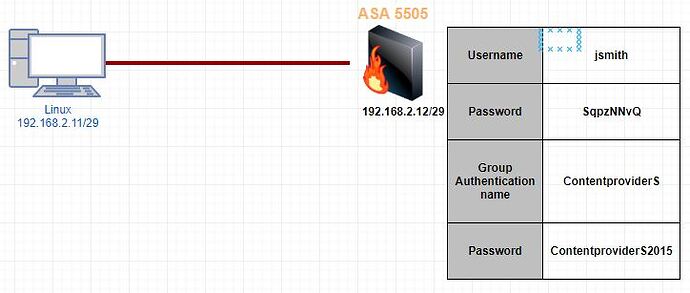
I configured a asa 5505 as remote access vpn server, and i am able to connect to it using the cisco vpn client. But for some reason I can’t get the strongswan settings right to connect to the asa.
I created a test environment (see pic) and I tried creating the conf file using the following guides:
https://www.strongswan.org/testing/testresults/ikev1/xauth-psk/
But without any luck.
I would really appreciate if you could help me out setting up the config for my scenario.
regards
jerrel
Hello Jerrel
Can you share with us more details about the types of problems you are having? Where is your configuration failing? Can you attempt to show us some verification commands such as those found in the Verify section of the Cisco document you shared? This way we’ll be able to help you more efficiently.
Looking forward to hearing from you.
Laz
Hello Rene,
I’m trying to configure ipsec ikev2 vpn between cisco ASA(ASA5506-X) and Pfsense but unfortunately unsuccessfully. Doing debug debug crypto ikev2 platform getting next messages:
IKEv2-PLAT-1: (88): IKEv2 protocol not allowed by policy set for vpn-tunnel-protocol
IKEv2-PLAT-1: (88): Connection is not authorized based on configured attributes
IKEv2-PLAT-2: (88): connection auth hdl set to -1
IKEv2-PLAT-1: Failed to remove peer correlation entry from cikePeerCorrTable. Local Type = 0. Local Address = 0.0.0.0. Remote Type = 0. Remote Address = 0.0.0.0. Correlation Peer Index = 0. IPSEC Tunnel Index = 0.
IKEv2-PLAT-2: (88): Encrypt success status returned via ipc 1
IKEv2-PLAT-2: Received PFKEY delete SA for SPI 0xFB21E1F5 error FALSE
Hello Alif
The error that you are receiving seems to be related with the identification of the traffic you want to send over the tunnel. Make sure that you have correctly configured the left and right subnets in the strongswan config, and that the same is done in the access list configuration in the ASA.
I hope this has been helpful!
Laz
Hey
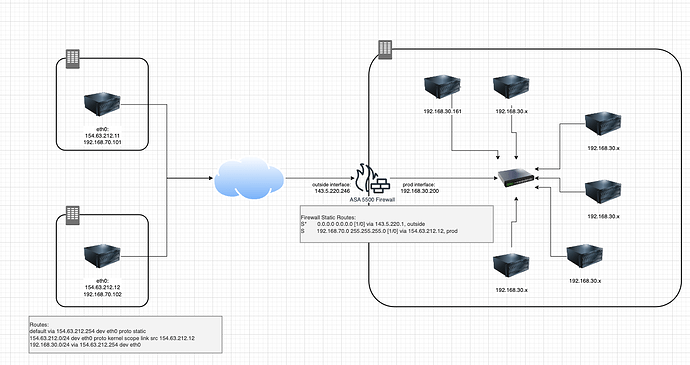
The network lesson for this was awesome, thanks, I was able to get the VPN tunnel up, but I’m hoping you might be able to point me in the right direction. I think I am missing some routing, as I can not ping between my subnets.
Looking at the this diagram I have 154.63.212.12 connected to the asa VPN, but if I do pings nothing comes through.
if I do show crypto isakmp sa:
IKEv2 SAs:
Session-id:10230, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
36313153 143.5.220.246/4500 154.63.212.12/4500 READY RESPONDER
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:14, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/24 sec
Child sa: local selector 192.168.30.0/0 - 192.168.30.255/65535
remote selector 192.168.70.102/0 - 192.168.70.102/65535
ESP spi in/out: 0x6c8f08d0/0xc5691db9on the server 192.168.30.161 routes are as follows:
default via 192.168.30.200 dev prod proto dhcp src 192.168.30.161 metric 100
192.168.30.0/24 dev prod proto kernel scope link src 192.168.30.161 metric 100
192.168.30.200 dev prod proto dhcp scope link src 192.168.30.161 metric 100on the server 192.168.70.102 routes are in the diagram.
Hello Philip
At first glance, there doesn’t seem to be anything that “sticks out” as a potential problem. It looks like the tunnel is up and it seems that your routing is configured on both ends. A couple of things that may help you to further troubleshoot are the following:
- It looks like in your implementation, the 154.63.212.12 device is not directly connected to the ASA, but is reaching the ASA via some routing, which is achieved through the default gateway of 154.63.212.254, which I assume is the default gateway on the local subnet. In the lesson, such routing was not configured in Strongswan, you just configured the “left” and “right” IP addresses (which I assume you have done correctly). So one of the issues may have to do with the way that the strongswan device and the ASA communicate with each other. Ensure that communication is achieved correctly.
- Secondly, on the ASA, for the return routing, you have configured recursive routing, indicating the IP address of 154.63.212.12 as the next hop IP for a destination of 192.168.70.0/24. And a default route to the default gateway of your local subnet. This wasn’t done on the other end of the link at the 154.62.212.12 device, so there is a lack of symmetry in the routing on either end. You may want to investigate that as a possible problem.
- Ensure that your VPN tunnel access lists on both ends are correct, so that the correct traffic is matched and tunneled.
One other troubleshooting suggestion is to establish the connection via a directly link between the ASA and the remote device so that they are on the same subnet, so that you can recreate the lab completely. That way you can determine of the issue really is the routing, or if it is something else in the rest of your configs. Based on the IP addresses you are sharing, I assume this is a production network, so I don’t know if that is a possibility or not. You can always simulate the implementation, work out all the kinks, and them deploy it on the production network. Let us know how you get along!
I hope this has been helpful!
Laz
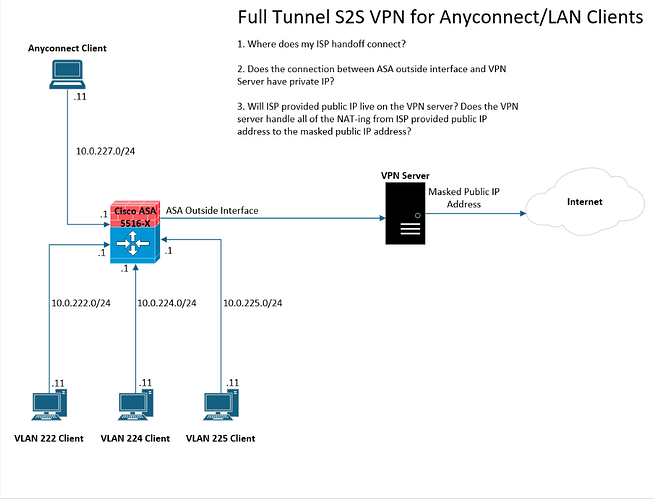
I am trying to Full-tunnel all of my LAN/Anyconnect traffic through a S2S VPN to a VPN Server (considering using StrongSwan on a Linux box). I want to encrypt my internet traffic and mask my public IP address. Based on my drawing and what I am trying to do, is this feasible? Am I thinking about this the right way?
Hello McKay
Thanks for sharing your planned network topology. There are a few questions I have before considering the problem at hand:
- You say that it’s a site-to-site VPN. This means that the VPN server and the Cisco ASA are at different sites and are connected over the Internet? Are they connected behind NAT or with public IP addresses?
- If “1” is true, then does the VPN server connect to the internet via the same connection it uses to create a site-to-site VPN with the ASA over another Internet connection? This will affect how internet traffic is routed, and how VPN trafffic is routed.
Once these topological questions are cleared up, then we can move on to the more specific VPN configurations. Ultimately, the setup you are attempting to create is indeed doable and is often used in networks where branch office traffic to the Internet is served from the Internet connection of HQ, even if each branch has its own Internet connection. This is often done to enforce policies on internet traffic and for security purposes. Let us know so we can continue the conversation.
I hope this has been helpful!
Laz
Lazarus,
Thank you for your response!
As far as exactly where the VPN server is located, I was thinking that it would be physically connected to my ASA’s outside interface. Would a setup like that work? Does the VPN server need to be behind the internet from perspective of the ASA?
Hello McKay
A site to site VPN by definition is one where the VPN tunnel itself goes from one site to another, and traverses some sort of unsecured network, such as the Internet. Site to site VPNs are established between devices that terminate the VPN tunnel. I assumed the ASA was one of those devices, and the VPN server the other, that is why I thought the internet would be between those two.
Can you define your sites in your “site to site” topology? That will help to further understand your setup and what you want to achieve. Since you have an anyconnect VPN client, could it be that you are not creating a site to site VPN but a client server VPN? Let us know…
I hope this has been helpful!
Laz
Lazarus,
Upon researching this further, it seems that I will need to spend some $$$ to make this work. I would need likely Azure/AWS/Business-level VPN services for my VPN server to operate as I intend.
I am looking to have a S2S connection between my ASA FW (on prem) to a VPN Server, to mask my client internet traffic without needing software installed on all of my individual devices. Unless you know of a cheap/free way to accomplish this, I will probably abandon the enterprise.