Hi Nityanand,
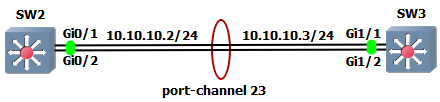
this “L3” written over the line means that both link end-points on switches are routed ports. We can add one more link interconnecting switches, make both of its end-points routed ports. Bundle links together, add IP on each end-point of port-channel and then run OSPF over it. It is no problem, should look like this.
Create virtual port-channel interface, make it routed port-channel and add IP on it.
SW2(config)# interface port-channel 23
SW2(config-if)# no switchport
SW2(config-if)# ip address 10.10.10.2 255.255.255.0
SW3(config)# interface port-channel 23
SW3(config-if)# no switchport
SW3(config-if)# ip address 10.10.10.3 255.255.255.0
Make physical interfaces routed ports and bundle them into port-channel. You can use interface range command for it.
SW2(config)# interface range g0/1 - 2
SW2(config-if-range)# no switchport
SW2(config-if-range)# channel-group 23 mode on
SW3(config)# interface range g1/1 - 2
SW3(config-if-range)# no switchport
SW3(config-if-range)# channel-group 23 mode on
Port-channel should be up, you can try some verification commands.
SW2# show etherchannel 23 summary
<..output omitted..>
Group Port-channel Protocol Ports
------+-------------+-----------+-----------------------------------------------
23 Po23(RU) - Gi0/1(P) Gi0/2(P)
Enable IP routing on both switches.
SW2(config)# ip routing
SW3(config)# ip routing
Run OSPF process on created L3 port-channel interfaces. For example like this.
SW2(config)# router ospf 1
SW2(config-router)# network 10.10.10.2 0.0.0.0 area 0
SW3(config)# router ospf 1
SW3(config-router)# network 10.10.10.3 0.0.0.0 area 0
OSPF adjancency should come up. You can verify it.
SW2# show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
10.10.10.3 1 FULL/DR 00:00:36 10.10.10.3 Port-channel23
Edit:
Notice that ip address is configured only on virtual port-channel. There is no ip address configured on physical routed ports.
In case you shutdown one physical interface then port-channel stays up. Verify it like this.
SW2(config)# interface g0/2
SW2(config-if)# shut
SW2# show etherchannel 23 summary
Group Port-channel Protocol Ports
------+-------------+-----------+-----------------------------------------------
23 Po23(RU) - Gi0/1(P) Gi0/2(D)
Pay attention to letters in brackets.
- Po23(RU), R means that it is layer 3 portchannel and U means that its status is up (working).
- Gi0/1(P ), P means that interface G0/1 is active and still bundled.
- Gi0/2(D), D tells us that interface is down, well because we did shut it down.
Is this what you was looking for?