This topic is to discuss the following lesson:
Thanks Rene for your introduction to firewall.
just a friendly feedback, I like a lot your videos when you use the White Board in person with your colored pens, It’s amazing, please keep using it. I feel like I am sitting in a real classroom.
Hi @wisamani,
Glad to hear you like it. I am also trying some “whiteboard” videos on my surface pro like the one in the SDN article:
Do you think those are just as good or still prefer the real whiteboard videos?
Rene
Thanks Rene for your reply, this video is very good, but honestly I am seeing your videos on the white board is much better. They are very strong, very clear and easy to understand.
Thanks for your amazing classes Rene. I just passed CCNP switch.
Thanks for your input Wisam, and grats for passing the SWITCH exam!
I really enjoyed this lesson. Thanks Rene for making this so easy to understand! I have a question though.
- What is NGFW and how it is different from the regular ones e.g. the one discussed in the lesson.
- Also Would be helpful if you guide to some resource on DPI (deep Packet Inspection) firewalls.
Also I Prefer this mode of presentation coz i feel more focussed this way. Whiteboard does not look so neat and also my focus shifts when you move during the video. Just my bit of feedback ![]()
Thank you!
Hi @Satish,
Thanks for your feedback. I also prefer the desktop recording, it’s more convenient than a whiteboard that requires cleaning and it’s easier to record from my desk ![]()
Laz wrote about the differences between “regular” firewalls and NGFWs awhile ago:
I’ll see if I can write some more about DPI in the future.
Hi, quick question regarding the service policy placement on the ASA, not including global because that’s pretty self explanatory. I created just a simple topology where the ASA was in the middle and has 2 routers on either side, the outside interface had a security level of 0 and inside 100, the outside interface is also blocking all traffic coming in. I implemented NAT on the ASA as well to change the inside network IP’s to the outside interface.
My policy map inspects ICMP and i applied it to a service policy that was placed on the inside interface, i tested it and everything worked as it should. NAT worked and allowed the traffic back into the inside network, the outside router could not ping the outside ASA interface IP and any inside network addresses. So everything is fine there. The same was done for the outside interface and the same behaviour was present.
My main question is then, how does the traffic get back through when the service policy is placed on the inside interface, when the class map matches ICMP then the inspection is applied on the policy map and the service policy is assigned to the inside interface, so the source IP would be the private IP of the host on the inside network, it then goes through NAT where NAT changes the source IP to the outside IP, when the return traffic comes back then it comes back with a destination address of the ASA outside IP but the dynamic ACL return traffic is for the destination address of the private IP, so how does it get through when there is no ACL for the traffic coming into the outside interface?
This is different from assigning the service policy on the outside where the dynamic ACL is the outside IP as the destination which can then be allowed and then the NAT binding table can direct traffic along it’s merry way.
Does anyone know the answer to this?
Hello Michael
First of all, we apologise for the late response. This is an excellent question, and thank you for sharing it with us.
It all has to do with order of operations. The standard document that is usually provided for order of operations regarding NAT is the following:
Based on this, the inside to outside and outside to inside orders are different. This means that when the traffic returns, it first goes through a NAT outside to inside translation and then goes through the policy routing, in which your policy maps are included. So the policy routing will take place after the NAT translation. So to answer this question:
… is that first the NAT translation occurs, then the policy routing which is based on the ACL which contains the internal IP address, that is, the translated IP address of the host in question.
I hope this has been helpful!
Laz
taking in mind this excerpt from this lesson:
“To ensure traffic from the OUTSIDE is able to reach the servers in the DMZ, we will use an access-list that only permits traffic to the IP address (and port numbers) that the servers in the DMZ use.”
Where you have to configure the ACL ? i mean, if i want to permit a specific public ip addr to have connectivity to a mail server behind the firewall, i could configure an ACL to permit this public ip addr, but where the ACL has to be located ?
Hello Juan
Keep in mind that traffic from a lower security level to a higher security level is denied by default. In general, a DMZ will have a higher security level than the outside interface, so in order to go against this default behaviour, an access list which will permit such traffic must be applied.
Now the ACL itself is defined globally using the well-known access list syntax. Once it is defined, you must then apply it to an interface specifying an in our outbound direction. You can find out more information about how to apply access lists on an ASA at the following lesson:
For your specific question, you must create an ACL that permits the destination IP address and port of the server in the DMZ and apply it to the outside interface on an inbound direction. In the above lesson, Rene describes just such an example in the section titled Permit Traffic to DMZ.
I hope this has been helpful!
Laz
Hi I want to know how how ASA FW does packet inspection on encrypted packet? If browser is using https to access something how ASA does deep packet inspection?
Hello Suman
HTTPS filtering is not supported on ASA due to the fact that HTTPS content is encrypted. So no deep packet inspection can be applied. This is according to the following Cisco documentation:
I hope this has been helpful!
Laz
hi,
if don’t have the Hardware,how to practice ASA firewall?
Thanks,
Tin
Hello Tin
The ASA is available on the GNS3 platform. Take a look at this information from the GNS3 site that details how to get the ASA working on their platform.
I hope this has been helpful!
Laz
Hi Rene,
Thanks for this tutorial but i think you should have discussed about types of firewall ?
As per my point of view the stuff of R&S ( CCNA to CCIE ) you created and sharing globally that’s great which help me a lot and and i think others as well so I want to give my view that you must add Security part ( CCNA to CCIE) written and Lab both in your curriculam.
BTW thanks a lot again you and Laz too for creating this channel and well support for clearing doubts.
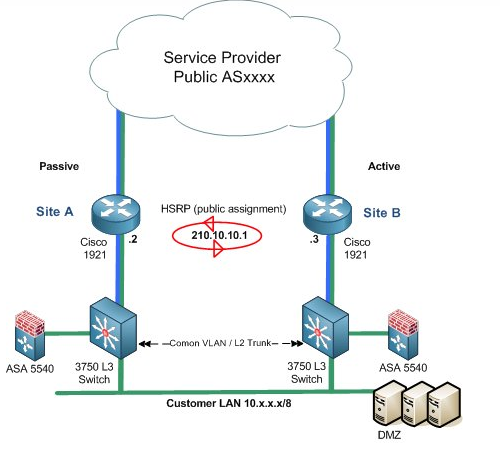
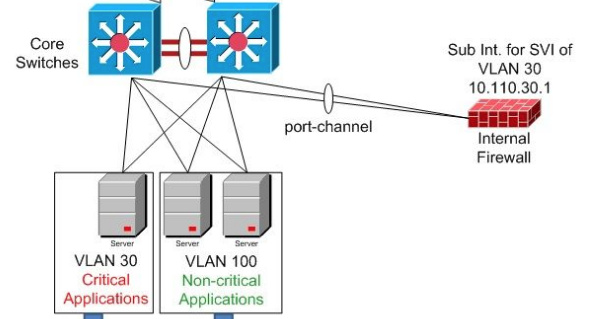
I am working on some firewall/data center labs and came across a similar design and trying to find the best way to approach. fwplacement #1 image is what I have on my lab and i am trying to force the traffic to my firewall before going to the HSRP Cisco 1841s. I have two 3750 L3 switches that have 4 Vlans on them. I can point them to the firewall but I am kinda lost after that. I am used to having the firewall on the outside.
- Would this be the equivalent of hairpinning ? 2) Not changing the configuration, would I have to do a static route and leave no default routing.
Any suggestions would be appreciated.
M
FW placement 1
FW placement 2
Reference:
Hello Matt
There is no single best answer, but there are specific principles that will determine the best arrangement for a particular topology.
Remember that a firewall introduces another location where routing takes place. This affects your topology, as well as introduces a single point of failure into the network, if you ave only one device. So if you have an HSRP arrangement and you want to maintain that redundancy, introducing a high availability firewall implementation is necessary.
Next you have to determine if “firewall on a stick” is the way to go for you. In the options described in the diagrams, this is the topology that is represented. Typically, you will have three VLANs hanging off of the ASA (inside, DMZ, outside). If you use firewall on a stick, a single physical link will be used to carry traffic for all three VLANs. Alternatively, you can use three physical connections to your switches, but that uses up valuable physical ports on your switches. For this reason, you may want to place them physically inline, between the 3750s and the 1921s shown in the first diagram. That in turn, seems to defeat the purpose of the HSRP configuration, so you may consider replacing the 1921s with an Active/Active firewall arrangement will perform the same type of redundancy as the HSRP implementation. In this way, you remove additional points of failure.
If I was building something from scratch, I’d connect the firewalls directly to the service provider in an Active/Active arrangement to replace the HSRP routers. I’d connect both firewalls to both 3750 switches with two physical connections each (DMZ and inside network) and let the 3750s to the rest of the routing for the rest of the internal VLANs.
I would only use the firewall on a stick topology in an already established network for which I want to change the least amount of things.
I know I haven’t definitively answered the question, simply because there is no definitive answer. But I hope it gives you more insight in order to decide on how to proceed.
If your topology is similar to the first diagram, then you would have to configure firewall on a stick for each ASA, and then have all your outgoing traffic (from both DMZ and inside networks) use the firewall as the default gateway (or at least route the traffic there) , and have the firewall route traffic to the HSRP virtual address.
I hope this has been helpful!
Laz
Laz,
This has been very helpful and thank you for your candid response. You brought up some points to consider and overall helped me to understand this method as opposed to the traditional one. I will work on your recommendations and then see how it goes. Thanks again for your response, much appreciated!
M
Hi Rene,
It is a great video. Eventhough I know some of the concepts, you have tied, routers firewall, firewall server and DMZ, and explained the functionality very well. I understand the individual modules.
Awesome job!
Keep up the great work!
Thank you,
Sreeni