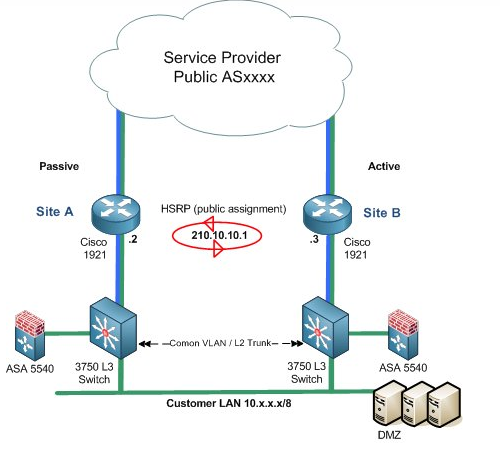
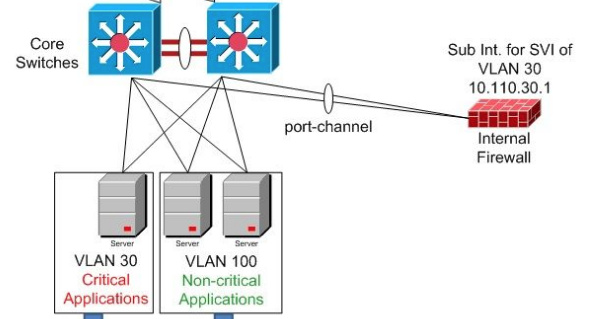
I am working on some firewall/data center labs and came across a similar design and trying to find the best way to approach. fwplacement #1 image is what I have on my lab and i am trying to force the traffic to my firewall before going to the HSRP Cisco 1841s. I have two 3750 L3 switches that have 4 Vlans on them. I can point them to the firewall but I am kinda lost after that. I am used to having the firewall on the outside.
- Would this be the equivalent of hairpinning ? 2) Not changing the configuration, would I have to do a static route and leave no default routing.
Any suggestions would be appreciated.
M
FW placement 1
FW placement 2
Reference: