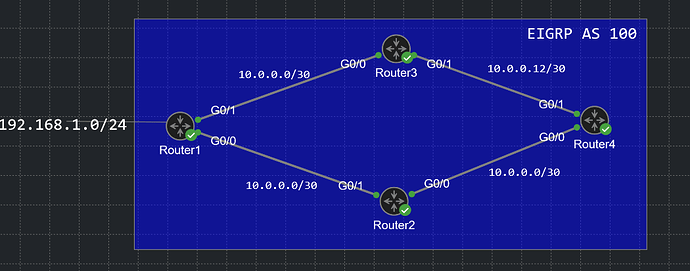
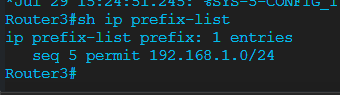
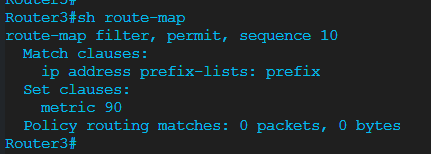
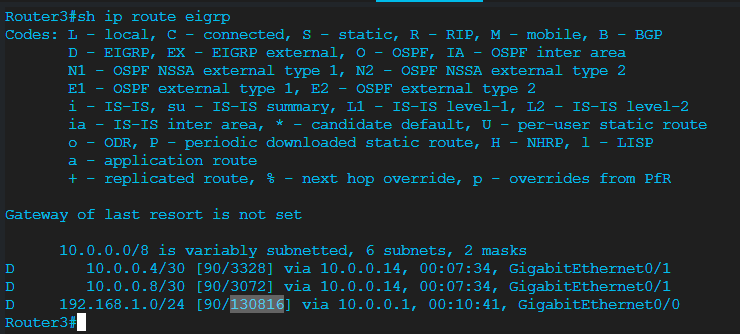
Thank you @lagapidis
If i am not wrong, a route-map of deny statement with a rule of deny/permit ACL would be denied
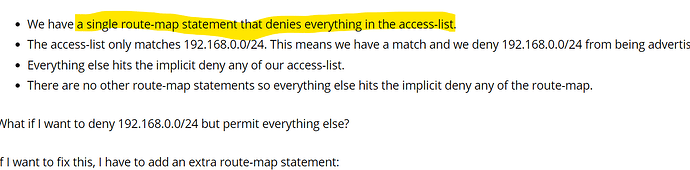
With single route-map deny:-
I have a single route-map deny statement that has an access rule to deny 1.1.1.1 and permit any. In this case route-map denies whatever matches like as below ( if i am not wrong ),
route-map deny + deny ACL = no match
route-map deny + permit ACL = Match but route-map denies all the match rule.
So the output of received eigrp route is none as expected, and thats what i got.
Router#sh ip access-lists R1
Standard IP access list R1
10 deny 1.1.1.1 (1 match)
20 permit any (5 matches)
Router#
Router#sh route-map
route-map TEST, deny, sequence 10
Match clauses:
ip address (access-lists): R1
Set clauses:
Policy routing matches: 0 packets, 0 bytes
Router#
Router#sh run | s r e
router eigrp 10
distribute-list route-map TEST in
network 0.0.0.0
Router#
Router#sh ip route eigrp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
Router#
Adding second route-map to permit all:-
I have added second route-map seq 20 statement to permit everything without any match rule. The output should match everything and must allow all routes
but it allows only 1.1.1.1 network. could you please explain why it allows a single prefix
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#route-map TEST permit 20
Router(config-route-map)#exit
Router(config)#
Router(config)#
Router(config)#exit
Router#
*Sep 26 12:22:05.126: %SYS-5-CONFIG_I: Configured from console by console
*Sep 26 12:22:13.304: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 192.168.13.1 (GigabitEthernet0/1) is resync: route configuration changed
Router#
Router#sh ip access-lists R1
Standard IP access list R1
10 deny 1.1.1.1 (1 match)
20 permit any (5 matches)
Router#
Router#sh route-map
route-map TEST, deny, sequence 10
Match clauses:
ip address (access-lists): R1
Set clauses:
Policy routing matches: 0 packets, 0 bytes
route-map TEST, permit, sequence 20
Match clauses:
Set clauses:
Policy routing matches: 0 packets, 0 bytes
Router#
Router#sh ip route eigrp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
D 1.1.1.1 [90/130816] via 192.168.13.1, 00:00:20, GigabitEthernet0/1
Router#
I removed the distribution list and see all the routes, just for your reference.
Router(config)#router eigrp 10
Router(config-router)#no distri
Router(config-router)#no distribute-list route-map TEST in
Router(config-router)#exit
Router(config)#
Router(config)#
Router(config)#exit
Router#
*Sep 26 12:35:02.049: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 192.168.13.1 (GigabitEthernet0/1) is resync: route configuration changed
Router#sh ip route eigrp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
D 1.1.1.1 [90/130816] via 192.168.13.1, 00:00:04, GigabitEthernet0/1
172.16.0.0/32 is subnetted, 5 subnets
D 172.16.1.1 [90/130816] via 192.168.13.1, 00:00:04, GigabitEthernet0/1
D 172.16.2.1 [90/130816] via 192.168.13.1, 00:00:04, GigabitEthernet0/1
D 172.16.3.1 [90/130816] via 192.168.13.1, 00:00:04, GigabitEthernet0/1
D 172.16.4.1 [90/130816] via 192.168.13.1, 00:00:04, GigabitEthernet0/1
D 172.16.5.1 [90/130816] via 192.168.13.1, 00:00:04, GigabitEthernet0/1
Router#