Hello Juan
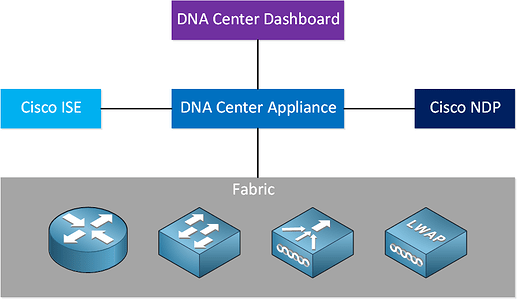
Let me try to elaborate on all of these. First, take a look at the diagram Rene shared in the lesson once again:
Notice that Cisco ISE and NDP are two separate entities. These are actually separate software processes that are run on either dedicated hardware, or on virtual machines. In each case, each one serves a very specific purpose:
- ISE is a security policy management platform that enables organizations to enforce security policies across their network infrastructure. This includes things like Network Access Control, Authentication and Authorization, Endpoint Compliance, Device Profiling, Security Intelligence Integration, and Policy Enforcement Across Wired, Wireless, and VPN. ISE can be used as a standalone solution, but or it can be integrated with DNA Center, where the policies defined in DNA can then be enforced by ISE. More about ISE can be found here.
- Cisco Network Data Platform or NDP is a multipurpose real-time network data collection and analytics engine used to significantly increase the business potential of network data. It is essentially an analysis tool that “ingests” a multitude of logging and monitoring info and does data correlation analysis, visualization, and action through a whole series of APIs connected to the DNA system.
Now the provision and assurance sections, as they are described, are actually parts of the DNA center dashboard. The provision section essentially lists the network devices that are “registered” to the DNA center and are configured and prepared to receive commands and to be controlled by the DNA center. The assurance section essentially gives you an overview of the network where you can view various aspects and vitals. You don’t control anything there, you only view. Does that make sense?
I believe that the only way to be able to further and more deeply understand the various concepts and their inner workings is to gain hands-on experience with these systems. You can do a bit more reading about each one, but nothing can replace the benefit of real hands-on experience.
I hope this has been helpful!
Laz