Hello Abdul
I tried the lab on my computer as well, and I found that when I use Chrome or Edge, I too cannot find any packets that match the http.host=="cisco.com" filter. This filter will show all HTTP packets that contain the cisco.com string. This should be found within an HTTP GET statement.
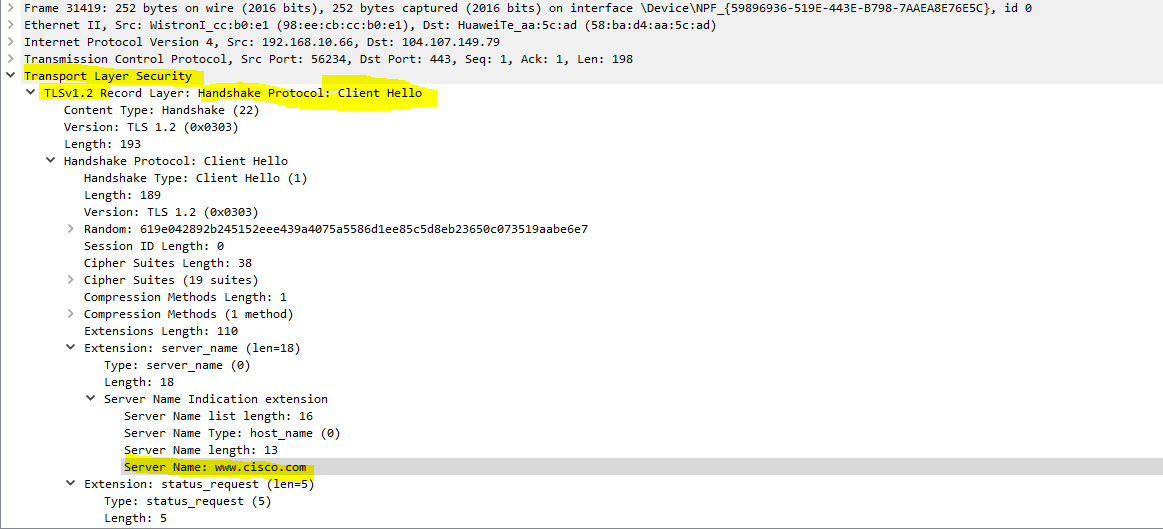
I researched it a little deeper and found that newer browsers don’t actually use a plain HTTP GET statement to receive web data. Using Wireshark, I searched for “cisco.com” as a string of text in any location within any packet, and I found a single entry in a packet using the TLSv1.2 protocol as a client hello:
This means that the browser is establishing a TLS session (sometimes incorrectly referred to as an SSL session, but SSL is the predecessor of TLS). It is within that session that the HTTP GET request is sent, but this is encrypted, so Wireshark cannot see it. More about how Wireshark sees TLS can be found here:
https://wiki.wireshark.org/TLS
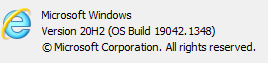
Now if you want to be able to see it, you can try the following. On my Windows 10 computer, I still have Internet Explorer (IE). The version I have is:
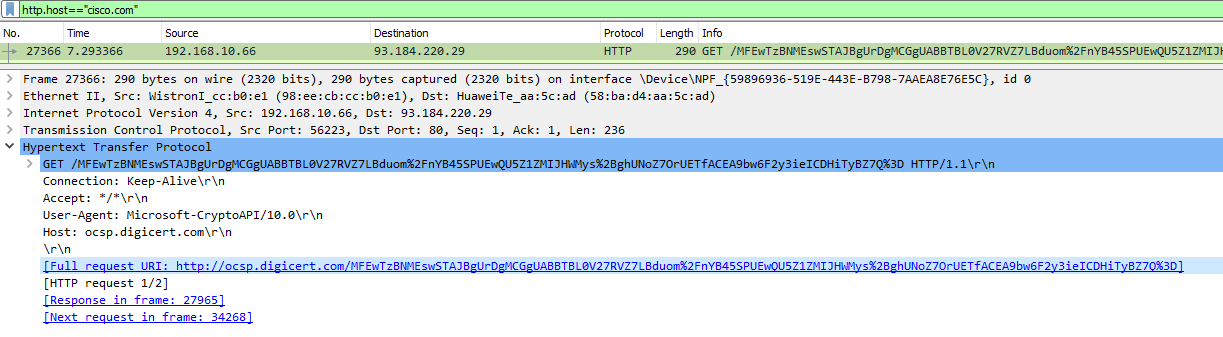
I tried going to cisco.com and capturing those packets, and I was able to see the GET request as shown in the lesson:
Notice here that you can’t actually see the “cisco.com” in the HTTP portion of the packet. That’s because even this version of IE is using HTTPS, which is a secure version. So it is encrpyted. However, Wireshark is able to decrypt and detect this text within the GET request.
I hope this has been helpful!
Laz